- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
CISO2CISO Editors' Picks
Latest News
Latest Published Posts
Cyber Topics
CISO Strategics & Leadership

Security Operations & SOC

Red - Blue & Purple Teams

Cloud Security

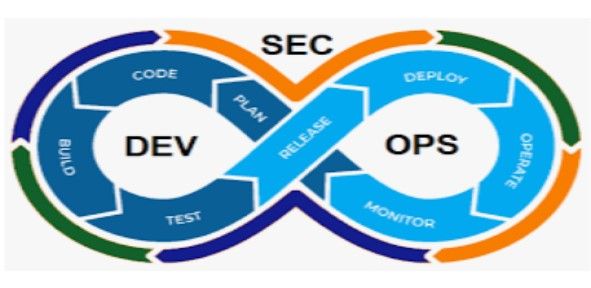
DevSecOps Discipline
THREAT INTELLIGENCE

Data Breaches & Leaks

Latest News
More Latest Published Posts
Latest News
Views: 3