The CIS Critical Security Controls (CSC) are a time-proven, prioritized, “what works” list of 20 controls...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Splunk
Query to identify failed login attempts:sourcetype=auth* "authentication failure"| stats count by user| sort -count Query to...
Like you, cybercriminals are on their own digital transformation journey. Trends like remote work, Internet of...
SECURING YOUR MULTI CLOUD Securing_Cloud_�?_1659516594-1Descarga
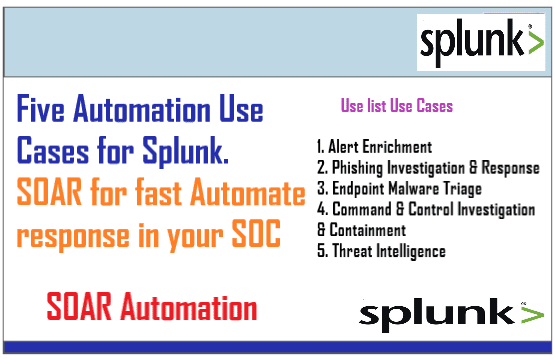
Splunk Use Cases Tags: Splunk 1- Windows Audit Log Tampering Check for any tampering done to Windows...
Business leaders need transformational security teams. The role of the chief information security officer (CISO) is...
The security operations center (SOC) is constantly overwhelmed. Analysts are drowning in security alerts, with far...