Source: securityboulevard.com – Author: Shikha Dhingra
Web application security testing aims to detect, prevent, and address security vulnerabilities within web applications. Flaws in web application coding accounted for 72% of the identified vulnerabilities. This evaluation involves scrutinizing the code, architecture, and deployment environment to assess the security posture of the applications. Security testing for web application can be executed manually or through automation, with the objective of uncovering potential risks such as cross-site scripting (XSS), SQL injection, buffer overflow, and malicious file execution.
The primary objective of web application security testing is to verify that web applications are secure and devoid of exploitable vulnerabilities that could result in data breaches or other malicious attacks.
Why is Web Application Security Testing Important?
Web application security testing plays an important role in the overall security strategy of organizations. With the increasing adoption of cloud technology by businesses, ensuring the security of web applications is paramount to safeguarding data and maintaining compliance with industry regulations. Given the vulnerability of web applications to malicious attacks, organizations must conduct regular testing and implement protective measures to mitigate potential threats.
The necessity for security testing for web applications stems from the exposure of these applications on public networks, making them accessible to anyone with internet connectivity. This accessibility increases the risk of attackers exploiting vulnerabilities within web applications to gain unauthorized access to sensitive information or disrupt operations. Moreover, web applications often serve as entry points into other systems, such as databases or servers, amplifying the potential impact of security breaches if not adequately secured.
Benefits of Web Application Security Testing to Organizations
Improvement in Security
Conducting web application security testing enables businesses to identify both current vulnerabilities and potential risks within the system, empowering them to take proactive measures to mitigate these issues. This proactive approach can significantly lower the risk of costly data breaches and other malicious attacks.
Enhanced Reputation
Businesses that prioritize security and regularly test web applications demonstrate their commitment to safeguarding customers’ data and upholding a positive reputation, which in turn enhances trust among customers.
Cost Savings
Early detection of potential issues through web application security testing allows businesses to save costs by preventing the need for expensive repairs or replacements resulting from malicious attacks or data breaches. Furthermore, conducting web application security testing assists organizations in meeting industry regulations, thereby avoiding substantial fines associated with non-compliance.
Improvement in Performance
Consistently testing web applications can reveal areas of performance lag or inefficient processes causing delays or errors. This insight enables businesses to implement necessary improvements that enhance overall performance and user experience.
Increased Efficiency
Web application security testing aids businesses in identifying system weaknesses, enabling them to streamline processes and enhance efficiency throughout the organization by removing unnecessary steps or redundant tasks.
Different Types of Software Testing in Web Application Security Testing
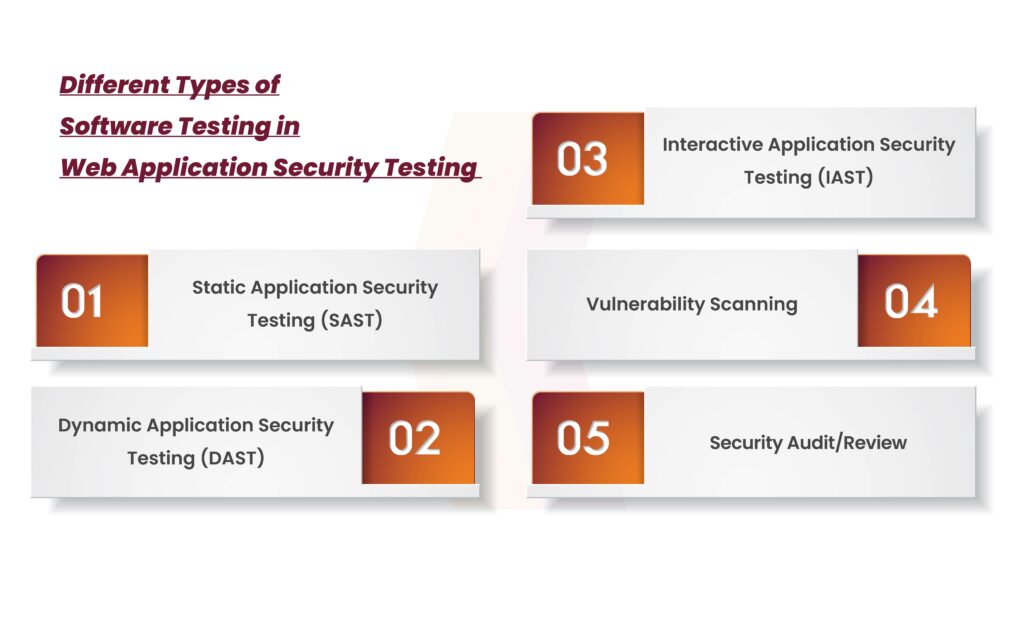
Static Application Security Testing (SAST)
This testing method is known as White Box Testing, allowing developers to detect security vulnerabilities within the source code of an application in the early stages of the software development life cycle. By using this approach, developers can verify that the application complies with coding guidelines and standards.
Dynamic Application Security Testing (DAST)
This approach entails injecting malicious data into the software to simulate SQL injection and XSS attacks, aiming to reveal prevalent security vulnerabilities. It is a form of black box or grey box security testing that empowers testers to pinpoint potential weaknesses in web applications.
Interactive Application Security Testing (IAST)
This method integrates aspects of both Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST), utilizing an Interactive Application Security Testing (IAST) agent embedded within the application to conduct real-time analysis. Our extensive network includes substantial experience in providing security testing services and identifying vulnerabilities for clients across various domains.
Vulnerability Scanning
This testing process utilizes automated software to inspect application vulnerabilities, conducting assessments for issues such as cross-site scripting, command injections, and more within web applications.
Penetration Testing
Penetration testing, commonly known as pen testing, is a security assessment performed by authorized cyber-security professionals to identify and exploit vulnerabilities within an application. Different types of penetration testing include Internal, External, Black Box, and Grey Box approaches.
Process of Web Application Security Testing
Web application security testing encompasses several essential procedures aimed at identifying vulnerabilities and maintaining a secure online environment. Let’s have a look at the fundamental processes:
Information Gathering
It is a vital aspect of web application security testing. During this initial stage, the focus is on thoroughly understanding the target application. Various testing methods involve conducting search engine reconnaissance and discovery to identify potential information leaks, enumerate applications, and fingerprint apps to determine the entry points for the application.
Authentication Testing
It involves verifying the digital identity of a communication sender. The most common example is the login process. Testing the authentication system requires understanding how the procedure works and leveraging that understanding to bypass the authentication mechanism. Examples of issues include weak lockout mechanisms, bypassing authentication schemes, vulnerabilities related to browser caching, and insufficient authentication in other channels.
Authorization Testing
After successfully authenticating with clear credentials linked to specific roles and privileges, the penetration tester will proceed to validate authorization. This process involves checking for insecure direct object references, potential privilege escalation, and bypassing permission rules. Permission testing entails understanding how the authorization system functions and using this knowledge to navigate around it effectively.
Testing for Error Handling
In the course of a web application penetration test, testers often encounter a range of error codes generated by applications or web servers. These issues can be revealed through specific requests crafted manually or using tools. Error codes are valuable to penetration testers because they provide insights into databases, security vulnerabilities, and other technical aspects relevant to online applications. Analyzing error codes and stack traces are just a few examples of how testers leverage this information.
Client-Side Testing
In the course of a web application penetration test, testers often encounter a range of error codes generated by applications or web servers. These issues can be revealed through specific requests crafted manually or using tools. Error codes are valuable to penetration testers because they provide insights into databases, security vulnerabilities, and other technical aspects relevant to online applications. Analyzing error codes and stack traces are just a few examples of how testers leverage this information.
Reporting
The goals of the reporting phase include presenting, ranking, and prioritizing findings, and providing project stakeholders with a concise, actionable report accompanied by relevant data. At Kratikal, we view this stage as the most critical and place significant emphasis on effectively communicating the significance of our findings and services.
How Does Security Testing for Web Applications Mitigate Risk for Organizations?
Security testing for web applications is vital for organizations to mitigate cyber threats and protect digital assets. This testing involves assessing web application design, functionality, and codebase to ensure resilience against attacks and compliance with industry regulations. Its objectives include identifying and mitigating vulnerabilities like XSS and SQL injection, preventing data breaches, ensuring compliance with regulations, averting negative publicity from breaches, and continuously improving security posture through proactive risk assessment and mitigation.
Book a Free Consultation with our Cyber Security Experts

Conclusion
Security testing for web application is essential for organizations to mitigate cyber threats, protect digital assets, and ensure compliance with industry regulations. By identifying and addressing vulnerabilities such as XSS, SQL injection, and authentication issues, security testing helps prevent data breaches and other malicious attacks. Moreover, security testing enhances organizational reputation by demonstrating a commitment to safeguarding customer data and maintaining compliance. Regular testing and improvement in security posture through various testing methods enable organizations to stay ahead of evolving threats and ensure a secure online environment. Overall, investing in web application security testing is critical for organizations to effectively manage and mitigate risks associated with cyber threats.web application security testing is essential for organizations to mitigate cyber threats, protect digital assets, and ensure compliance with industry regulations.
By identifying and addressing vulnerabilities such as XSS, SQL injection, and authentication issues, security testing helps prevent data breaches and other malicious attacks. Moreover, security testing enhances organizational reputation by demonstrating a commitment to safeguarding customer data and maintaining compliance. Regular testing and improvement in security posture through various testing methods enable organizations to stay ahead of evolving threats and ensure a secure online environment. Overall, investing in web application security testing is critical for organizations to effectively manage and mitigate risks associated with cyber threats.
Kratikal a CERT-In empanelled auditor provides businesses with a wide range of cybersecurity solutions & services. Trusted by over 450+ SMEs and Enterprises worldwide, Kratikal delivers robust cybersecurity solutions. We are one of the fastest-growing firms committed to safeguarding companies and organizations of different sectors, for instance, SaaS, Fintech, Healthtech, Govt., etc., against cyber risks.
FAQ
- Q1: What Is The Standard Followed For Web Application Testing?
Ans: The VAPT of web applications typically adheres to industry security frameworks such as OWASP Top 10, SANS 25, NIST, and other relevant standards.
- Q2: What Does A Web Application Security Testing Report Consist Of?
Ans: The report defines objectives and provides detailed risk descriptions for each vulnerability found, along with Proof-of-Concept (POC) evidence. Vulnerabilities are categorized by severity levels (Critical, High, Medium, Low, Info) based on their CVSS score, with recommendations for mitigation included.
The post What is Web Application Security Testing? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/what-is-web-application-security-testing/
Original Post URL: https://securityboulevard.com/2024/04/what-is-web-application-security-testing-2/
Category & Tags: Security Bloggers Network,Cyber Security – Security Bloggers Network,Cyber Security