Source: securityboulevard.com - Author: Michael Yegypko Protecting your e-commerce platform from unauthorized changes and skimming attacks...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: bacohido By Byron V. Acohido Spread spectrum technology helped prevent the jamming...
Source: securityboulevard.com - Author: cybernewswire Cary, United States, May 28th, 2024, CyberNewsWire If there is a...
Source: securityboulevard.com - Author: Enzoic Penetration testing, commonly known as pentesting, is an essential practice for...
Source: securityboulevard.com - Author: Ingrid Gliottone The link between cybersecurity and personal reputation management for executives...
Source: securityboulevard.com - Author: Kyle Morris, Senior Compliance Success Manager, Scytale ‘Vendor Risk Management’ is more...
Source: securityboulevard.com - Author: Wajahat Raja Recent reports claim that the Microsoft Threat Intelligence team stated...
Source: securityboulevard.com - Author: Walker Banerd Who do you want running your security operations: robots or...
Source: securityboulevard.com - Author: Robert Levine In May 2024, a comprehensive Transport Layer Security (TLS) scan...
Source: securityboulevard.com - Author: Rohan Timalsina On May 2, 2024, the City of Helsinki announced the...
Source: securityboulevard.com - Author: Shubham Jha A security breach. Headlines scream, investors panic, and fingers get...
Source: securityboulevard.com - Author: Dwayne McDaniel St. Charles, MO, is known as the launching point for...
Source: securityboulevard.com - Author: Deborah Erlanger What is the Centraleyes AI Governance Framework? The AI Governance...
Source: securityboulevard.com - Author: Joao Correia One of the most critical yet often overlooked aspects of...
Source: securityboulevard.com - Author: Marc Handelman Photograph Courtesy of the United States Marine Corps, Photographer: Caitlin...
Microsoft’s Copilot+ Recall Feature, Slack’s AI Training Controversy – Source: securityboulevard.com
Source: securityboulevard.com - Author: Tom Eston Episode 331 of the Shared Security Podcast discusses privacy and...
Source: securityboulevard.com - Author: Grip Security Blog Innovation has always been a catalyst for transformation, driving...
Source: securityboulevard.com - Author: Marc Handelman Authors/Presenters:Phillip Rieger, Marco Chilese, Reham Mohamed, Markus Miettinen, Hossein Fereidooni,...
Source: securityboulevard.com - Author: Lohrmann on Cybersecurity Artificial intelligence is yielding unprecedented benefits, battles, opportunities and...
Source: securityboulevard.com - Author: Ofir Stein Protecting credentials has become increasingly critical in recent years, with...
Source: securityboulevard.com - Author: Nathan Eddy Human error is responsible for most cybersecurity risks, with nearly...
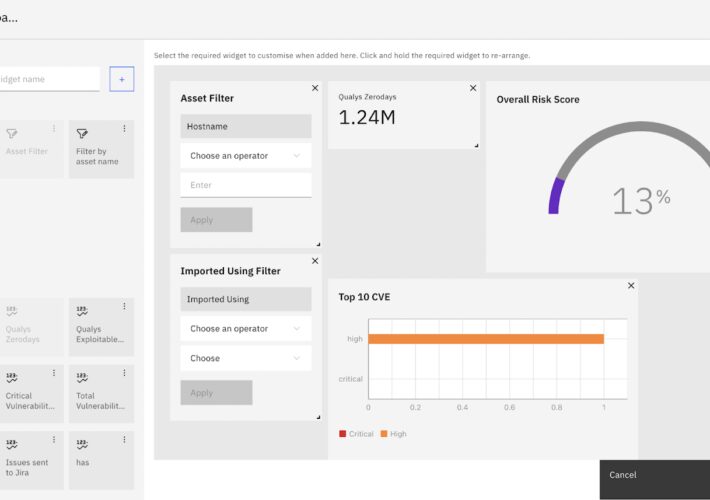
Source: securityboulevard.com - Author: Alibha CISOs require a central hub for visualizing critical security data. Strobes...
Source: securityboulevard.com - Author: Ahona Rudra Reading Time: 4 min Why is software security so important?...
Source: securityboulevard.com - Author: Ani Khachatryan At Ekran System, we constantly enhance the capabilities of our...
Source: securityboulevard.com - Author: Riddika Grover The digital era is constantly evolving, and businesses are rapidly...
Source: securityboulevard.com - Author: Max Aulakh In the past, we’ve talked a lot about the various...
Source: securityboulevard.com - Author: Apurva Dave Tools Workload IAM automatically manages access. Secrets management tools such...
Source: securityboulevard.com - Author: Lorenzo Vayno Digital ad fraud is taking billions out of marketing budgets,...
Source: securityboulevard.com - Author: Nathan Eddy There are significant security concerns in the deployment of leading...
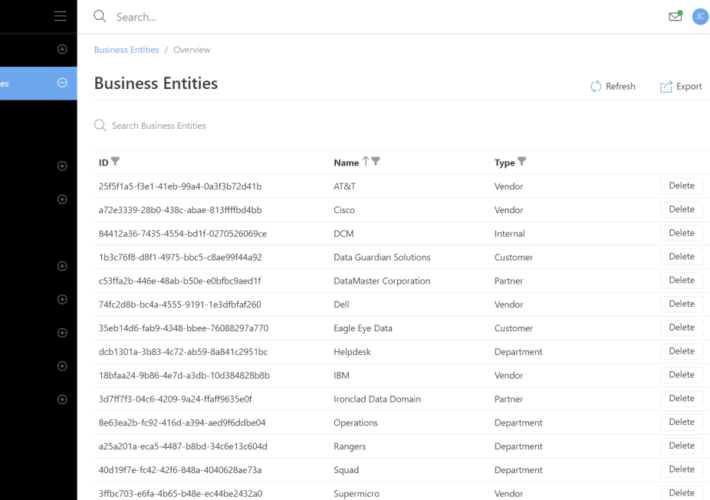
Source: securityboulevard.com - Author: Rajan Sodhi We’ve introduced Business Entities, a game-changer for tracking customers, partners,...