Source: thehackernews.com – Author: . NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a defense against a variant of a RowHammer attack...
Author: CISO2CISO Editor 2
Over 600 Laravel Apps Exposed to Remote Code Execution Due to Leaked APP_KEYs on GitHub – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered a serious security issue that allows leaked Laravel APP_KEYs to be weaponized to gain remote code execution...
Squid Dominated the Oceans in the Late Cretaceous – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier New research: One reason the early years of squids has been such a mystery is because squids’ lack of hard...
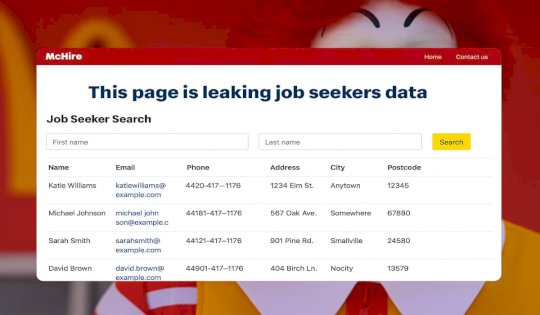
McDonald’s AI hiring tool’s password ‘123456’ exposed data of 64M applicants – Source: www.csoonline.com
Source: www.csoonline.com – Author: A security flaw in McHire allowed access to sensitive applicant data via default admin credentials and a vulnerable API. The issue was...
DoNot APT Hits European Ministry with New LoptikMod Malware – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Trellix reveals how the India-linked DoNot APT group launched a sophisticated spear-phishing attack on a European foreign affairs ministry. Learn...
McDonald’s AI Hiring Tool McHire Security Flaw Exposed Candidate Chat Data – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. McHire’s AI system vulnerability briefly exposed limited candidate chat information. Learn how Paradox promptly fixed the issue, confirming data for...
Athlete or Hacker? Russian basketball player accused in U.S. ransomware case – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russian basketball player arrested in France over alleged ties to a ransomware group accused of targeting U.S. firms and federal...
CVSS 10 RCE in Wing FTP exploited within 24 hours, security researchers warn – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones Huntress security researchers observed exploitation of the CVSS 10.0 remote code execution (RCE) flaw in Wing FTP Server on July...
UK Online Safety Act ‘not up to scratch’ on misinformation, warn MPs – Source: go.theregister.com
Source: go.theregister.com – Author: Lindsay Clark The Online Safety Act fails to tackle online misinformation, leaving the UK in need of further regulation to curb the...
Pay2Key Ransomware Gang Resurfaces With Incentives to Attack US, Israel – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
350M Cars, 1B Devices Exposed to 1-Click Bluetooth RCE – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
As Cyber-Insurance Premiums Drop, Coverage Is Key to Resilience – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Factoring Cybersecurity Into Finance’s Digital Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeff Prelle Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Digital Fingerprints Test Privacy Concerns in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
ISACA Addresses Experience Gap with CISA Associate Designation – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: ISACA has launched the Certified Information Systems Auditor (CISA) Associate designation, enabling CISA exam passers without the required experience to kickstart their...
British Man Sentenced for Network Rail Wi-Fi Hack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A British man has been sentenced for the hack of Network Rail public Wi-Fi last year which resulted in customers being exposed...
Indian Cyber Espionage Group Targets Italian Government – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The DoNot APT group has recently conducted a multi-stage cyber espionage campaign targeting the Italian Ministry of Foreign Affairs, according to Trellix....
Over Half of “Finfluencer” Victims Have Lost Money, Says TSB – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A growing number of young people are losing money after acting on the advice of unregulated “finfluencers” they follow on social media,...
MPs Warn of “Significant” Iranian Cyber-Threat to UK – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Iranian threat actors pose a major threat to the UK, especially its petrochemical, utilities and finance sectors, a new parliamentary report has...
Watchguard Analysis Surfaces Major Spike in Malware Detections – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard An analysis of cyberattacks shared this week by Watchguard Technologies finds there was a 171% increase in total unique network...
Spyware on Androids Soars – Source: securityboulevard.com
Source: securityboulevard.com – Author: Teri Robinson In general, malware aimed at Androids rose 151% in February and March but a whopping increase came with the 692%...
Rubio Impersonation Incident is Latest High-Profile Deepfake Scam – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The State Department sent an alert to embassies and consulates warning of AI-generated impersonations of high-ranking federal officials after someone...
GTT Extends Palo Alto Networks Alliance to Add Managed SASE Service – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard GTT Communications extended its alliance with Palo Alto Networks to include an additional managed secure access service edge (SASE) offering....
Leaked Shellter Elite Tool Now Fueling Infostealer Attacks Worldwide – Source:hackread.com
Source: hackread.com – Author: Waqas. A new report details how the advanced hacking tool Shellter Elite was leaked and is now being used by cybercriminals. Learn...
FBI Seizes Major Sites Sharing Unreleased and Pirated Video Games – Source:hackread.com
Source: hackread.com – Author: Waqas. The Department of Justice and the FBI’s Atlanta Field Office confirmed today that they have seized and dismantled several notorious online...
New Study Shows Google Tracking Persists Even With Privacy Tools – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Google and its tracking of user activity is nothing now but a recent study by SafetyDetectives, conducted across the US,...
14 Arrested in Romania for £47 Million UK Tax Phishing Scam – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. A major international operation has led to the arrest of 14 individuals suspected of involvement in a large-scale phishing attack...
Magento 2 Shipping Automation: Cut Costs While Enhancing Customer Experience – Source:hackread.com
Source: hackread.com – Author: Owais Sultan. Imagine slashing shipping costs by 30% while speeding up deliveries, and watching 4-star reviews roll in. That is the power...
Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257) – Source:thehackernews.com
Source: thehackernews.com – Author: . Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary database...
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could allow...