Source: securityboulevard.com – Author: wlrmblog
On Friday April 12, Palo Alto disclosed that some versions of PAN-OS are not only vulnerable to remote code execution, but that the vulnerability has been actively exploited to install backdoors on Palo Alto firewalls. A patch is expected to be available on April 14th. The advisory from Palo Alto is here. The CISA advisory is here. Palo Alto has marked this vulnerability as critical and NVD has scored it a 10.0 with CVSSv3. Wallarm currently detects attacks against this vulnerability with no additional configuration required.
What is CVE-2024-3400
A severe command injection vulnerability in the GlobalProtect Gateway feature of PAN-OS versions 10.2, 11.0, and 11.1 underscores the critical importance of API security in devices at the frontline of network connections. The vulnerability, identified as CVE-2024-3400, allows unauthorized users to execute commands as the system administrator, significantly threatening the security of critical infrastructure.
The issue, rated with the maximum severity score of 10 out of 10, was discovered during routine operations and specifically affects systems with both GlobalProtect gateway and device telemetry enabled.
Affected and unaffected versions are as follows:
- Affected: PAN-OS 10.2 versions below 10.2.9-h1, PAN-OS 11.0 versions below 11.0.4-h1, and PAN-OS 11.1 versions below 11.1.2-h3.
- Unaffected: Cloud NGFW, Panorama appliances, Prisma Access, and all other PAN-OS versions.
To determine vulnerability, users should check their firewall configurations for an active GlobalProtect gateway (Network > GlobalProtect > Gateways) and enabled device telemetry (Device > Setup > Telemetry). Palo Alto Networks has noted a few instances where this flaw has already been exploited.
Fixes for the impacted versions are scheduled to be released by April 14, 2024.
Exploit Details and Detection Challenges of CVE-2024-3400
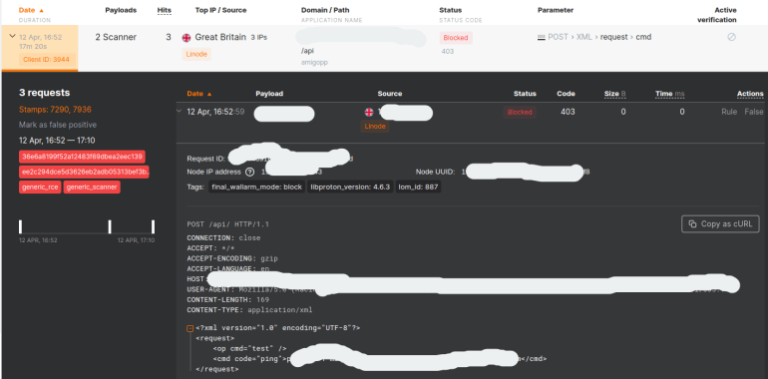
The exploit for CVE-2024-3400 operates through a straightforward XML RPC request that embeds malicious code within an XML tag, specifically
OS command exploit is there
This particular method of attack highlights the need for comprehensive API security measures, as the exploit can bypass traditional security systems like Web Application Firewalls (WAF) and Intrusion Prevention Systems (IPS) through XML obfuscation techniques.
For organizations utilizing PAN-OS, it is critical to be aware that while the access to the /api endpoint can be tracked in the logs, the actual exploit payload within the XML body is not recorded in the standard access.log or other log files. This absence of detailed logging underscores the necessity of deploying a dedicated API security solution to monitor and protect these vectors effectively.
Given these complexities, it is crucial for network administrators to enhance their monitoring capabilities to include detailed analysis of all API traffic, particularly focusing on XML data that might not typically be logged. Implementing an advanced API security solution will provide the additional layer of scrutiny required to detect and mitigate such obscured exploits effectively
GitHub’s Response
In response to the discovery and exploitation of CVE-2024-3400, GitHub has actively started to remove repositories containing exploits and proof-of-concept (POC) code related to this vulnerability. An example of such swift action can be seen with the removal of one of the first exploits published for this issue, available at https://github.com/DrewskyDev/CVE-2024-3400, which was uploaded on April 12th. Despite GitHub’s efforts to curb the spread of this exploit, numerous other resources and platforms have already distributed this POC, indicating a rapid dissemination across the cyber community.
Wallarm Response and First Exploits
Customers of Wallarm Advanced API Security , whether they use inline or out-of-band (OOB) deployments, are automatically shielded from threats. This protection is provided through Wallarm’s advanced mechanisms designed to prevent many types of API injections, including the OS commanding payloads of CVE-2024-3400, and its robust features for parsing XML APIs.
The first exploits detected by Wallarm occurred on April 12th at 4:52 PM CST. Since this initial detection, there has been a significant increase in activity, with about 500 new attacks being recorded every hour. This escalating pattern underscores the urgency for continuous monitoring and adaptive security measures to protect against emerging threats. Wallarm’s proactive approach and sophisticated security infrastructure are pivotal in defending against such high-risk vulnerabilities, ensuring the integrity and security of customer data and services.

Attackers have already demonstrated the capability to exploit this vulnerability by using sophisticated XML obfuscation methods, making the detection of such attacks by usual WAFs and IDS/IPS systems challenging. These techniques involve altering the XML encodings, structure, and sizes in ways that evade detection by conventional security tools, which rely on recognizing known patterns of attack signatures.
Recommendation and next steps
Wallarm strongly advises all users to frequently check the official Palo Alto Networks advisory page at https://security.paloaltonetworks.com/CVE-2024-3400 for the latest updates. It is critical to update affected devices immediately once the patch is available. To ensure comprehensive security, Wallarm also recommends performing a complete firmware hard reset on updated devices to eliminate any potential backdoors that might have been installed. Additionally, if your PanOS devices were handling SSL/TLS termination, it’s crucial to review and potentially revoke any certificates to prevent any security breaches that might have occurred through compromised certificates. This
The post How to track and stop CVE-2024-3400: Palo Alto Devices API Exploit Causing Critical Infrastructure and Enterprise Epidemics appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by wlrmblog. Read the original post at: https://lab.wallarm.com/palo-alto-devices-api-exploit-causing-critical-infrastructure-and-enterprise-epidemics/
Original Post URL: https://securityboulevard.com/2024/04/how-to-track-and-stop-cve-2024-3400-palo-alto-devices-api-exploit-causing-critical-infrastructure-and-enterprise-epidemics/
Category & Tags: Security Bloggers Network,API security – Security Bloggers Network,API security