Number of new cyber operations recorded In 2023, the European Repository of Cyber Incidents (EuRepoC) recorded a total of 895 new cyber operations, averaging about 75...
Month: May 2024
Attacking IOS
In this comprehensive guide, we delve into the world of iOS security from an offensive perspective, shedding light on the various techniques and methodologies used by...
Artificial Intelligence and Cybersecurity Research 2023
Artificial Intelligence (AI) is a typical dual-use technology, where malicious actors and innovators are constantly trying to best each other’s work. This is a common situation...
Android Security Research Book
Android security research plays a major role in the world of cybersecurity that we live in today. As of 2024, Android has a 71.74% global market...
Active Directory Penetration Testing Training Online
Active Directory (AD) is a Microsoft Windows Server-based directory service. Active Directory Domain Services (AD DS) manages directory data storage and makes it accessible to network...
Active Directory Security
Active Directory (AD), introduced with Windows 2000 [1], has become an integral part of modern organizations, serving as the backbone of identity infrastructure for 90% of...
GLOBAL AUTOMOTIVE CYBERSECURITY REPORT
Connectivity is continuing to transform the Automotive and Smart Mobility ecosystem, increasing cybersecurity risks as more functionality is exposed. 2023 marked the beginning of a new...
2024 Cyber Security Report by Checkpoint
Welcome to the Check Point 2024 Cyber Security Report. In 2023, the world of cyber security witnessed significant changes, with the nature and scale of cyber...
2023 Mobile Banking Heists Report
Zimperium’s latest research explores a dynamic and expanding threat landscape by meticulously analyzing 29 banking malware families and associated trojan applications. This year alone, the research...
2023 Internet Crime Report
Today’s cyber landscape is threatened by a multitude of malicious actors who have the tools to conduct large-scale fraud schemes, hold our money and data for...
RedTail Cryptomining Malware Exploits PAN-OS Vulnerability – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cryptocurrency Fraud , Endpoint Security , Fraud Management & Cybercrime Threat Actors Mirror the Tactics of North Korea’s Lazarus Group Prajeet...
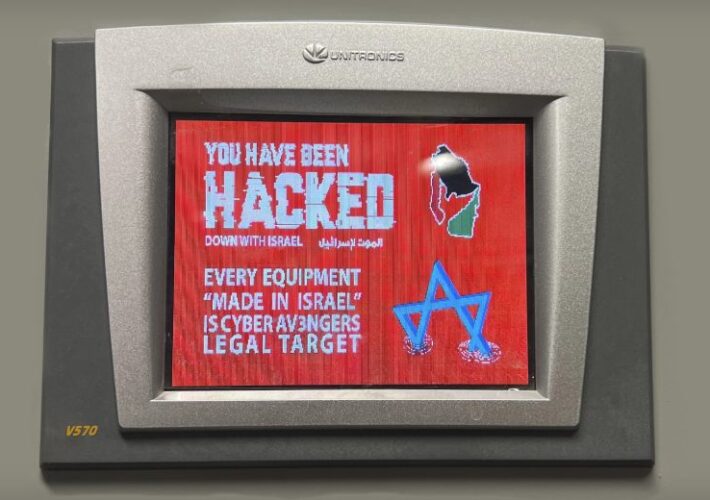
Internet-Exposed OT Devices at Risk Amid Israel-Hamas War – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security Cyberattack on Aliquippa Water Plant Highlights Vulnerabilities in OT Systems Prajeet Nair (@prajeetspeaks) • May 30, 2024 ...
Hospital Allegedly Skirting Ransomware Death Suit Settlement – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Attorneys Say Hospital Is Reneging on Paying Up in Case Involving Baby’s...
Cryptohack Roundup: FTX Paid Off Whistleblowers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Guilty Pleas – Lots of Them Rashmi Ramesh (rashmiramesh_)...
EU’s New AI Office Is Set to Begin Operating in June – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development The Office Will Oversee the Implementation of the European Union’s...
Australian Industries Need OT-IT Convergence to Beat Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Operational Technology (OT) IT and OT Teams Rarely Talk and When They...
US Army Unveils $1B Modern Software Development Initiative – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybersecurity Spending , Government , Industry Specific Army Seeking Public Input on $1 Billion Software Modernization Contract Vehicle Chris Riotta (@chrisriotta)...
Rx Benefits Firm Notifying 2.8 Million of Data Theft Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Healthcare The Breach Notice Raises the Question of Whether Sav-Rx Paid a Ransom...
Live Webinar | Passwordless – The Future of Authentication – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Password & Credential Management Presented by Duo 45 minutes Passwords are inherently...
Hiring Kit: Cryptography Engineer – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cryptography engineers often collaborate with cybersecurity teams to integrate robust cryptographic solutions into software, hardware and network infrastructure, addressing potential vulnerabilities and...
Identity vulnerabilities a concern at Microsoft, outside researcher claims – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Top insights for IT pros From cybersecurity and big data to cloud computing, IT Brew covers the latest trends shaping business...
A Microsoft under attack from government and tech rivals after ‘preventable’ hack ties executive pay to cyberthreats – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Microsoft has come under fire recently from both the U.S. government and rival companies for its failure to stop a Chinese...
Pakistani ‘Transparent Tribe’ APT Aims for Cross-Platform Impact – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Muhammad Toqeer via Alamy Stock Photo A Pakistan-linked cyber-espionage group has pivoted to a wider variety of...
CatDDOS Threat Groups Sharply Ramp Up DDoS Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Aleksey Funtap via Alamy Stock Photo Researchers have spotted a recent surge in activity involving a Mirai...
Making the Case for ‘Reasonable’ Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer Source: Kjetil Kolbjørnsrud via Alamy Stock Photo In litigation, specificity is crucial. “Beyond a reasonable doubt” is the...
Attackers Target Check Point VPNs to Access Corporate Networks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Wright Studio via Shutterstock In recent months, researchers have observed an increase in attackers using remote access...
OpenAI Forms Another Safety Committee After Dismantling Prior Team – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: SOPA Images Limited via Alamy Stock Photo Open AI is forming a safety and security...
90+ Malicious Apps Totaling 5.5M Downloads Lurk on Google Play – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Anatolii Babii via Alamy Stock Photo More than 90 malicious mobile apps have been downloaded more than...
Treasury Sanctions Creators of 911 S5 Proxy Botnet – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. Department of the Treasury today unveiled sanctions against three Chinese nationals for allegedly operating 911 S5, an online anonymity...
Building AI on a Foundation of Open Source Requires a Fundamentally New Approach to Application Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Nadav Czerninski, Co-founder and CEO, Oligo Security AI has sprung from the pages of science fiction into our daily...