Source: www.proofpoint.com - Author: 1 Top insights for IT prosFrom cybersecurity and big data to cloud...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Proofpoint
Source: www.proofpoint.com - Author: 1 Microsoft has come under fire recently from both the U.S. government...
Source: www.proofpoint.com - Author: 1 Chief information security officers around the globe "are nervously looking over...
Source: www.proofpoint.com - Author: 1 Top insights for IT prosFrom cybersecurity and big data to cloud...
Source: www.proofpoint.com - Author: 1 To mitigate this area of vulnerability, 86% of CISOs in Canada...
Source: www.proofpoint.com - Author: 1 To mitigate this area of vulnerability, 87% of CISOs are turning...
Source: www.proofpoint.com - Author: 1 Source: Thongden Studio via ShutterstockA likely Chinese threat actor is using...
Source: www.proofpoint.com - Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies &...
Source: www.proofpoint.com - Author: 1 Proofpoint Archive customers will meet the globally recognized industry standards in...
Source: www.proofpoint.com - Author: 1 CRN spoke with the CEOs and CTOs of a number of...
Source: www.proofpoint.com - Author: 1 The Power 100 is culled from the ranks of CRN’s Women...
Source: www.proofpoint.com - Author: 1 Vendors including Palo Alto Networks, Trellix and Proofpoint debuted new AI-powered...
Source: www.proofpoint.com - Author: 1 10,851 followers 1w Edited To wrap up this edition of NightVision,...
Source: www.proofpoint.com - Author: 1 At RSA Conference 2024 this week, vendors are showcasing new products...
Source: www.proofpoint.com - Author: 1 Customers now benefit from both new pre-delivery social engineering and link...
Source: www.proofpoint.com - Author: 1 In a special episode of Behind the Deal live from Thoma...
Source: www.proofpoint.com - Author: 1 Home » Videos » Proofpoint’s Brian Reed on the Data Loss...
Source: www.proofpoint.com - Author: 1 Greg Lesnewich, senior threat researcher at Proofpoint, sits down to discuss...
Source: www.proofpoint.com - Author: 1 AWS customers worldwide can now deploy Proofpoint’s full stack of people...
Source: www.proofpoint.com - Author: 1 New DLP Transform revolutionizes insider and data loss programs to enable...
Source: www.proofpoint.com - Author: 1 Proofpoint is the only vendor evaluated to receive the Customers' Choice...
Source: www.proofpoint.com - Author: 1 Source: Yuri Arcurs via Alamy Stock PhotoAt first, analysts thought the...
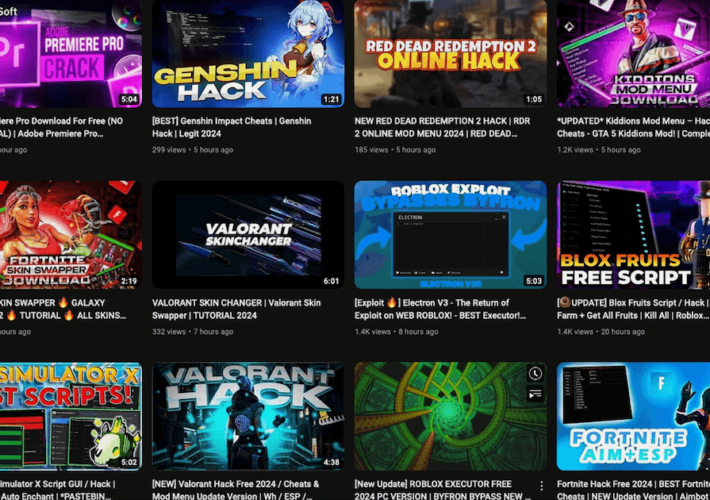
Source: www.proofpoint.com - Author: 1 Hackers are distributing malware through multiple YouTube channels that promote cracked...
Source: www.proofpoint.com - Author: 1 Jesse Fasolo, Director, Technology Infrastructure & Cyber Security, St. Joseph’s Health...
Source: www.proofpoint.com - Author: 1 Thread hijacking attacks. They happen when someone you know has their...
Source: www.proofpoint.com - Author: 1 Proofpoint’s Threat Protection platform achieves a "Strong Positive" rating in all...
Source: www.proofpoint.com - Author: 1 SECURITY New service from Proofpoint prevents email data loss through AI...
Source: www.proofpoint.com - Author: 1 WASHINGTON (AP) — Hackers linked to the Chinese government launched a...
Source: www.proofpoint.com - Author: 1 New Adaptive Email Data Loss Prevention closes a gap in DLP...
Source: www.proofpoint.com - Author: 1 85% of organizations experienced data loss in the past year; 90%...