Source: securityboulevard.com – Author: Flashpoint Intel Team
Yesterday was the monthly (in)famous Patch Tuesday, where many major vendors release vulnerability fixes for their products. While many vendors mainly focus on the Microsoft releases, our Flashpoint VulnDB team, as usual, closely tracked and covered the releases by all the different vendors and pushed standardized alerts to our clients. A total of 220 new vulnerabilities were covered by the team and another 562 VulnDB entries were updated with additional information with the remaining lower severity issues being covered Wednesday.

The Practitioner’s Guide to Vulnerability Intelligence and Vulnerability Management
A guide in adopting a risk-based approach, and how to build a scalable, high-quality vulnerability management program (VMP).
The first vendor of the day to release their security fixes was SAP with 15 new vulnerabilities. None of those stood out as critical with the most severe being CVE-2023-32111, which could lead to a remote denial of service in SAP PowerDesigner Proxy. System administrators of SAP systems should still evaluate the fixed issues and determine the impact to their specific environment and how to prioritize the patch effort.
The next vendor to follow was Siemens, who also released a total of 15 new vulnerabilities along with a lot of updates to existing issues. Three vulnerabilities stood out from the rest: two vulnerabilities in the Siemens Siveillance Video product that could lead to authenticated remote code execution (CVE-2023-30898 and CVE-2023-30899) as well as an authenticated remote command injection vulnerability in the Siemens SCALANCE LPE9403 product (CVE-2023-27407).
Later in the day, we saw releases from Mozilla (31 new vulnerabilities), Rockwell Automation (3 new vulnerabilities), Citrix (2 new vulnerabilities), Schneider Electric (2 new vulnerabilities), AMD (26 new vulnerabilities), and Intel (85 new vulnerabilities) before the two main vendors of the day, Adobe and Microsoft, finally released their security advisories covering 14 and 38 new vulnerabilities (49 including updates), respectively.
The vulnerabilities fixed by Adobe this month only affected Adobe Substance 3D Painter. If using this product, be aware that some of these fixes did address potential code execution vulnerabilities so applying the update should be prioritized.
Of the remaining vulnerabilities addressed by this Patch Tuesday, the two that mostly stood out were two 0-days fixed by Microsoft: CVE-2023-29336 and CVE-2023-24932. Please note that some media and security vendors claim that Microsoft addressed three 0-day vulnerabilities by erroneously including CVE-2023-29325 in the mix.
Two Microsoft 0-days
Secure Boot Security Feature Bypass Vulnerability
The first 0-day addressed by Microsoft is CVE-2023-24932, which is a local vulnerability in the boot manager that allows bypassing the Secure Boot protection mechanism. According to Microsoft, this is actively being exploited “by the BlackLotus bootkit to exploit CVE-2022-21894.” It should be noted that in order to exploit this vulnerability, an attacker would either need physical access or administrative rights to the system. The most plausible attack vector would not be a malicious Administrator but rather malicious code planted on the system via exploitation of another vulnerability or vulnerability chain that allowed compromising the system and gaining administrative rights.
While a patch is available to address this vulnerability it’s imperative that people note that after applying the fix, additional actions are required to fully implement the protections. Microsoft also warns that “if this fix is not properly enabled there is a potential to cause disruption and prevent a system from starting up.” Details are available in the accompanying guidance document provided by Microsoft.
Microsoft state that they will be providing a second release on 2023/07/11 to “provide additional update options to simplify the deployment of the protections.” Finally, Microsoft plans to release a final version of the fix during the first quarter 2024 to “enable the fix for CVE-2023-24932 by default and enforce bootmanager revocations on all Windows devices.”
Win32k Elevation of Privilege Vulnerability
The second 0-day addressed by Microsoft is CVE-2023-29336. This is a local privilege escalation vulnerability within the Win32k component that allows gaining SYSTEM privileges. No details are currently available about the scope of active exploitation or targets. Our team is actively monitoring this vulnerability as well as researching more details.
Other vulnerabilities worth mentioning
Apart from the two 0-days, based on the vague currently available information about the vulnerabilities fixed, the following stand out as being worth keeping an eye on and address in a timely manner:
CVE-2023-29325
As previously mentioned, this is the vulnerability that some sources incorrectly refer to as a 0-day. It is not. Microsoft’s security bulletin lists it as “Publicly Disclosed: Yes” but “Exploited: No”.
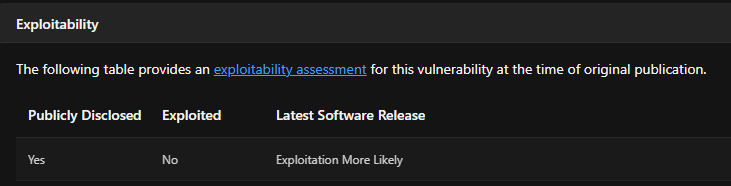
This means that details about the vulnerability were shared publicly prior to the security bulletin being released i.e. an uncoordinated disclosure, but not that it was actively exploited as a zero-day. Microsoft does, however, flag it as “Exploitation More Likely” so it’s one of the vulnerabilities that should be prioritized to address. The issue was reported to Microsoft by Will Dormann, who shared further information about his findings:
Merely referencing {00000315-0000-0000-C000-000000000046} or {00000316-0000-0000-C000-000000000046} as a COM object in a Rich Text email would cause Outlook to crash.
I handed off to MSRC before further investigating exploitability beyond a denial of service. pic.twitter.com/ZdPuseSj6e— Will Dormann (@wdormann) May 9, 2023
Apparently, simply referencing two CLSIDs ({00000315-0000-0000-C000-000000000046} or {00000316-0000-0000-C000-000000000046}) as a COM object in a Rich Text email would crash Outlook. Upon further investigation, Microsoft determined that this has a potential code execution impact and can even be triggered from the Preview Pane. As a workaround, Microsoft recommends reading email in plain text format.
CVE-2023-24902
This is another privilege escalation vulnerability in the Win32k component. While this is not currently being actively exploited unlike CVE-2023-29336, Microsoft does rate it as “Exploitation More Likely”. Similar to the actively exploited vulnerability this could allow local attackers to gain SYSTEM privileges.
CVE-2023-24954
This is an information disclosure vulnerability in Microsoft SharePoint Server. While authentication is required, Microsoft states that it could be exploited to disclose “user tokens and other potentially sensitive information.” This vulnerability is also rated by Microsoft as “Exploitation More Likely”.
CVE-2023-24941
The final vulnerability worth prioritizing is in the Network File System (NFS) service and can potentially be exploited for remote code execution via a specially crafted request. Microsoft clarifies that NFSV2.0 and NFSV3.0 are not affected. Exploitation is also deemed more likely for this vulnerability.
Microsoft did address other vulnerabilities with higher CVSS scores e.g. in the Bluetooth driver, LDAP functionality, Microsoft Office, SSTP (Secure Socket Tunneling Protocol), PGM (Pragmatic General Multicast) feature, and AV1 video extension. However, these were all rated as “Exploitation Less Likely”. This should not be viewed as a guarantee that exploits for these vulnerabilities won’t surface, so these would still be prudent to also prioritize.
Over the next few days we expect to add a lot of new details to many of these entries both based on external research and research performed by our in-house team.
Original Post URL: https://securityboulevard.com/2023/05/tracking-patch-tuesday-vulnerabilities-may-2023/
Category & Tags: Security Bloggers Network,Vulnerabilities,cyber threat intelligence,patch management,Patch Tuesday,Threat Intelligence,vulnerability intelligence,Vulnerability Management,Vulnerability Remediation – Security Bloggers Network,Vulnerabilities,cyber threat intelligence,patch management,Patch Tuesday,Threat Intelligence,vulnerability intelligence,Vulnerability Management,Vulnerability Remediation




















































