Source: www.securityweek.com – Author: Ionut Arghire Gmail users in the US can now run scans to find out whether their Gmail ID appears on the dark...
Day: May 10, 2023
Equifax Releases Security and Privacy Controls Framework – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Credit reporting agency Equifax on Wednesday released its security and privacy controls framework to provide a public blueprint to help...
Appeals Court Sides With Corellium in Apple Copyright Case – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A US appeals court on Monday sided with Corellium in the copyright infringement lawsuit filed by Apple against the company...
Dragos Says Ransomware Gang Accessed Limited Data but Failed at Extortion Scheme – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Industrial cybersecurity vendor Dragos on Wednesday said a known ransomware group breached its defenses and accessed threat intel reports, a...
SquareX Raises $6 Million for Browser Security Product – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cybersecurity startup SquareX today emerged from stealth mode with $6 million raised in a seed funding round led by Sequoia...
Webb Raises $7 Million for Blockchain Asset Transfer Privacy System – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Blockchain company Webb Technologies this week announced that it has raised $7 million in seed funding for its privacy solutions...
IBM Delivers Roadmap for Transition to Quantum-safe Cryptography – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend IBM has introduced a quantum-safe roadmap to help the complex organizational transition to post-quantum cryptography at this year’s annual Think...
Capita Says Ransomware Attack Will Cost It Up to $25 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs UK-based business process outsourcing and professional services company Capita said on Wednesday that it expects to incur costs ranging between...
CISO Conversations: HP and Dell CISOs Discuss the Role of the Multi-National Security Chief – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend HP and Dell Technologies are two of the world’s largest international computer manufacturers. Their CISOs, Joanna Burkey (HP) and Kevin...
SAP Patches Critical Vulnerabilities With May 2023 Security Updates – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire German enterprise software maker SAP this week announced the release of 18 new security notes on its May 2023 Security...
RiskLens SOC 2 Type 2 Certification Validates Privacy, Security Commitment – Source: securityboulevard.com
Source: securityboulevard.com – Author: RiskLens Staff RiskLens successfully completed a SOC 2 Type 2 audit and certification of our security measures and operational practices. The audit...
7 Building Blocks for a Successful Internal Developer Platform for Kubernetes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Cook As organizations continue to adopt Kubernetes for container orchestration, the need for a robust internal developer platform has become increasingly...
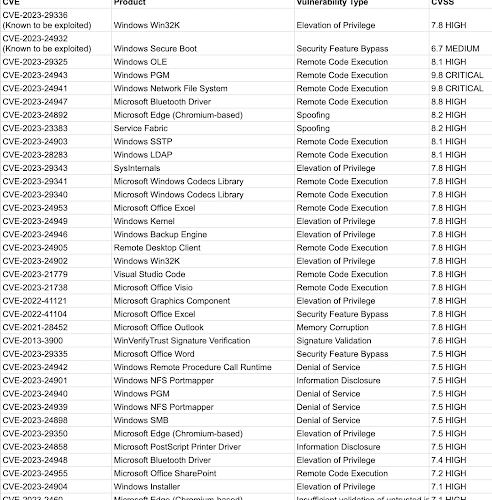
Tracking Patch Tuesday Vulnerabilities: May 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flashpoint Intel Team Yesterday was the monthly (in)famous Patch Tuesday, where many major vendors release vulnerability fixes for their products. While many...
Patch Tuesday May 2023: Microsoft Addresses 49 Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ofri Ouzan On May 9th 2023, Microsoft released their May Patch Tuesday and revealed 38 vulnerabilities fixes, 11 vulnerabilities fixes published on...
SafeBreach Coverage for US-CERT Alert (AA23-129A) – Snake Malware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach The Cybersecurity and Infrastructure Security Agency (CISA) shared the findings of an investigation...
USENIX Enigma 2023 – Marcus Hodges – ‘Meaningful Hardware Privacy For A Smart And Augmented Future’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/usenix-enigma-2023-marcus-hodges-meaningful-hardware-privacy-for-a-smart-and-augmented-future/ Category & Tags: Security Bloggers Network,appsec education,cybersecurity...
How You Can Save Time During a SOC 2 Audit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Satya Moutairou POV: an important prospect requires all of their partners to get a SOC 2 audit. You’ve just met with your...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #241 — Team – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Open Source Threat Intelligence Tools & Feeds: A Complete 2023 List – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yuzuka Akasaka The rapidly evolving cyber threat landscape demands constant vigilance from organizations seeking to protect their digital assets. Open source threat...
What are Indicators of Compromise in Threat Intelligence? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yuzuka Akasaka Managing security in today’s highly interconnected world can be like trying to put out fires with a collection of squirt...
Microsoft Fixes BlackLotus Vulnerability, Again – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management May Patch Tuesday Fixes 38 Bugs Including 3 Zero Days Prajeet Nair (@prajeetspeaks) •...
Profiles in Leadership: JT Jacoby – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Multi-factor & Risk-based Authentication , Security Operations , Video IRC CISO on Modernizing Security Controls to Detect Rather Than Respond to...
Researchers Find Bypass for a Fixed Bug; MSFT Patches Again – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Email Threat Protection , Fraud Management & Cybercrime , Governance & Risk Management Akamai Says Exploit Sidesteps Patched Vulnerability Exploited by...
EU Attorneys Question Legality of Chat App Scanning For CSAM – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Encryption & Key Management , Endpoint Security , Governance & Risk Management European Commission Legal Service Says Proposal Likely Violates Europeans’...
YouTube tests blocking videos unless you disable ad blockers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan YouTube is running an experiment asking some users to disable their ad blockers or pay for a premium subscription, or...
Fake in-browser Windows updates push Aurora info-stealer malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A recently spotted malvertising campaign tricked users with an in-browser Windows update simulation to deliver the Aurora information stealing malware....
New ransomware decryptor recovers data from partially encrypted files – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new ‘White Phoenix’ ransomware decryptor allows victims to partially recover files encrypted by ransomware strains that use intermittent encryption....
Cybersecurity firm Dragos discloses cybersecurity incident, extortion attempt – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Industrial cybersecurity company Dragos today disclosed what it describes as a “cybersecurity event” after a known cybercrime gang attempted to...
Surprise! Coldplay lyrics hidden in Kingston SSD firmware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma What has firmware got to do with pop rock, you ask? That’s the question that crossed a security researcher’s mind...
Top 5 Password Cracking Techniques Used by Hackers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software One of the biggest security threats is password cracking. Are you an IT system administrator concerned about the...