Source: www.bitdefender.com – Author: Graham Cluley
Surprise! The LockBit ransomware group has re-emerged, just days after a high-profile law enforcement operation seized control of its infrastructure and disrupted its operations.
“Operation Cronos” saw global agencies around the world work together to seize control of LockBit’s website, where information had been published about ransomware victims and their stolen data, possibly leaving many hoping that LockBit was gone for good.
However, at least some of those at the heart of the notorious ransomware gang have chosen not to run to the hills – but instead appear to have created a new website on the dark web where they are listing what appear to be corporate victims.
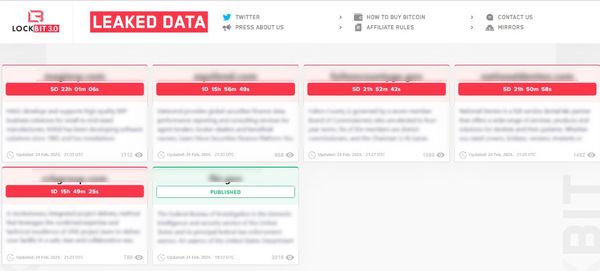
Like the Hydra of Greek mythology, cutting off one head of LockBit doesn’t matter – it can spawn multiple new ones. LockBit is struggling to abandon a criminal campaign that has extorted over US $120 million.
LockBit’s secretive administrator, who uses the online handle “LockBitSupp”, acknowledged that the group’s infrastructure was likely compromised by computer crime-fighting authorities due to their failure to patch their PHP version because of “personal negligence and irresponsibility.”
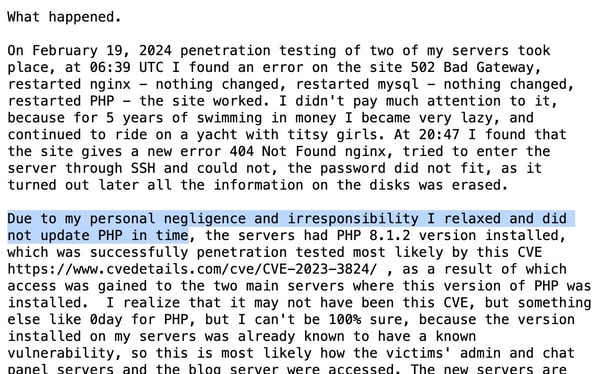
Yes, a reckless and sloppy attitude to computer security is a problem for both companies falling victim to ransomware attacks and those attacking them.
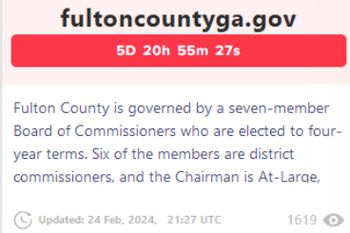
According to LockBitSupp, the takedown of LockBit’s systems occurred as the group prepared to release sensitive information it had stolen in a crippling attack against government systems in Fulton County, Georgia.
Interestingly, Fulton County restored its systems but county official Robb Pitts told press in the hours after LockBit’s infrastructure was seized, that the county had not paid a ransom:
“This was a ransomware incident carried out by criminals for their own financial gain. We could not, in good conscience, use Fulton County taxpayer funds to make a payment. We did not pay nor did anyone pay on our behalf.”
The LockBit gang claimed that information stolen from Fulton County included documents related to court cases against Donald Trump “that could affect the upcoming US election” if leaked.
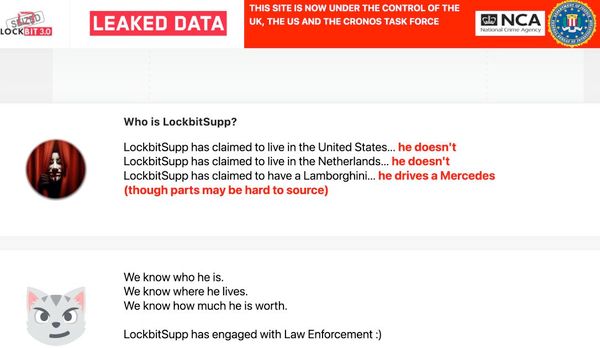
LockBitSupp went on to describe how “Personally I will vote for Trump.” It’s unclear if this is an attempt to mislead observers into believing that they are based in the United States or not.
After seizing the LockBit leak site, the UK’s National Crime Agency (NCA) stated that it does not believe LockBitSupp is based in the USA.
Meanwhile, LockBit’s new site is threatening once again to release data previously stolen from Fulton County’s computer systems.
LockBitSupp’s admission about their security failing should be a wake-up call for all. If your organisation hasn’t done a thorough security assessment lately, it’s time. Vulnerability patching isn’t a luxury, it’s a necessity. Secure backups and security awareness training for all staff are crucial.
Rewards of up to US $15 million are being offered for the identification or location of key individuals in the LockBit gang, and the arrest and/or conviction of anyone involved in its ransomware activities.
The fight against ransomware is ongoing.
Original Post URL: https://www.bitdefender.com/blog/hotforsecurity/the-lockbit-ransomware-gang-rears-its-ugly-head-again-after-law-enforcement-takedown/
Category & Tags: Data loss,Guest blog,Law & order,Malware,Ransomware,data breach,Lockbit,ransomware – Data loss,Guest blog,Law & order,Malware,Ransomware,data breach,Lockbit,ransomware




















































