Source: securityboulevard.com – Author: Michael Toback
Introduction
In today’s interconnected world, understanding the OWASP Top 10 IoT vulnerabilities is crucial, especially for small businesses striving to maintain a secure environment. The Internet of Things (IoT) is revolutionizing how small businesses operate, offering innovative solutions and opportunities for efficiency and growth. However, with the myriad of benefits comes a host of vulnerabilities, making it imperative for small business managers and IT personnel to be well-versed in securing their IoT devices.
The Open Web Application Security Project (OWASP) is a nonprofit organization focused on improving software security. Their compilation of the Top 10 IoT vulnerabilities serves as a comprehensive guide for organizations to understand and mitigate the most critical security risks associated with IoT devices.
Understanding IoT in Small Businesses
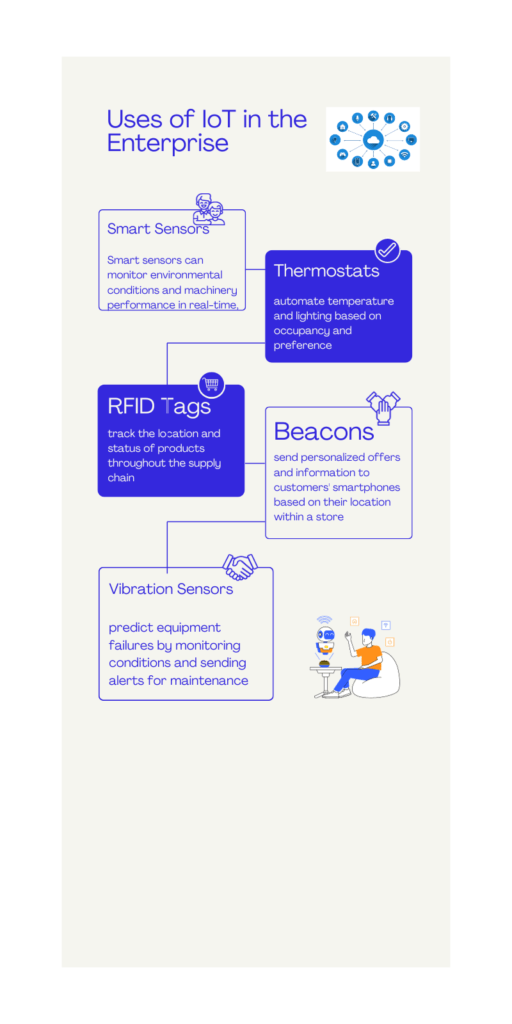
Internet of Things (IoT) refers to the network of physical devices connected to the internet, collecting and sharing data. For small businesses, IoT can range from smart thermostats controlling the office temperature to advanced manufacturing equipment. These devices, while enhancing operational efficiency, also open doors to potential security threats, making the knowledge of IoT security paramount.
In small businesses, IoT devices are often implemented to streamline operations, improve customer experiences, and reduce costs. For instance, a small retail store might use IoT sensors to track inventory levels and customer foot traffic, enabling better inventory management and customer service.
Why Small Businesses are Targets of the OWASP Top 10 IoT Vulnerabilities: The Risks
Small businesses are increasingly becoming lucrative targets for cybercriminals due to the perceived lack of adequate security measures. The integration of IoT devices in business operations exacerbates the risks, as each connected device is a potential entry point for cyberattacks.
The risks associated with IoT in small businesses are multifaceted, encompassing data breaches, unauthorized access, and disruption of business operations. A single vulnerability can lead to the compromise of sensitive business and customer data, resulting in financial losses and damage to reputation.
Therefore, small businesses must be proactive in addressing IoT security risks, implementing robust security measures, and fostering a culture of cybersecurity awareness among employees. By doing so, they can safeguard their operations and maintain the trust of their customers and stakeholders.
Diving into OWASP’s Top 10 IoT Vulnerabilities
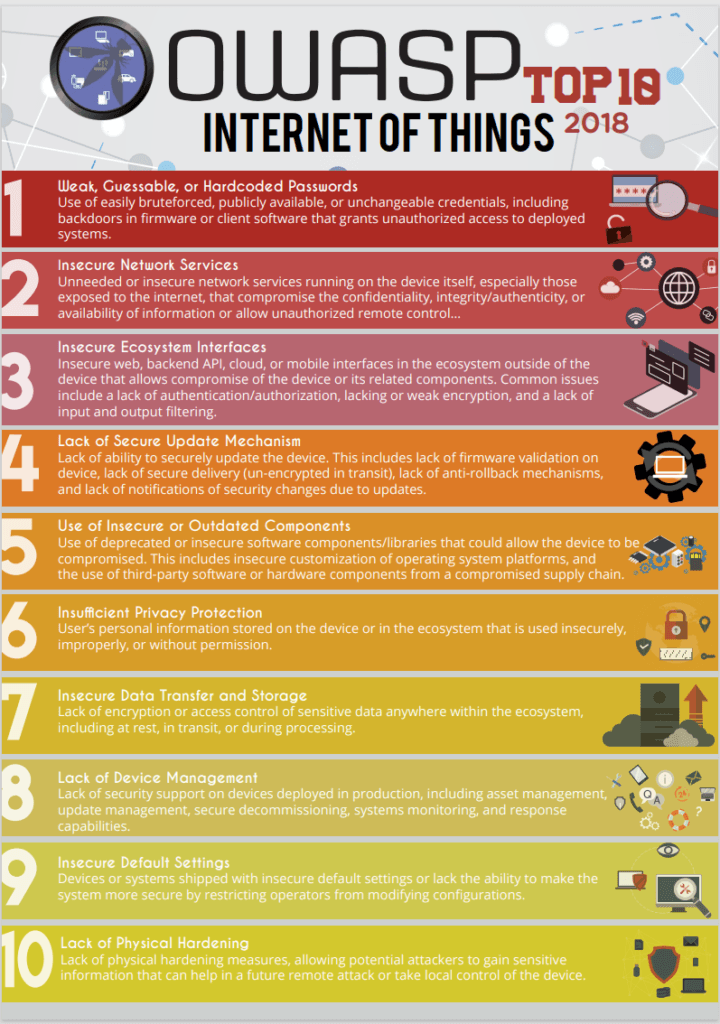
Source: OWASP-IoT-Top-10-2018-final.pdf
Understanding the OWASP Top 10 IoT vulnerabilities is pivotal for securing the myriad of interconnected devices prevalent in small businesses. These vulnerabilities, if not properly mitigated, can allow cybercriminals to exploit insecure devices, gain unauthorized access, and potentially compromise the entire business network. The implications of such breaches can be severe, impacting not only the business operations but also customer trust and business reputation.
In this section, we will delve deeper into each of these vulnerabilities, exploring their intricacies and providing practical solutions to secure your IoT devices against them. By addressing these vulnerabilities, small businesses can fortify their defenses, safeguarding their operations and sensitive data against potential cyber threats.
1. Weak, Guessable, or Hardcoded Passwords
One of the most prevalent vulnerabilities in IoT devices is the use of weak, guessable, or hardcoded passwords. This vulnerability can allow unauthorized users to gain control of the device, access sensitive data, and potentially launch attacks on other devices within the network.
Mitigation Strategies:
- Regularly update passwords, using strong and unique combinations.
- Avoid using default passwords and ensure all passwords are encrypted.
- Implement multi-factor authentication where possible.
- Explanation of the vulnerability and its risks.
- Practical advice and solutions on how to mitigate this vulnerability.
2. Insecure Network Services
Insecure network services pose a significant risk, as they can be exploited to perform unauthorized actions, disrupt device operations, and access or alter sensitive information. This vulnerability emphasizes the need for secure and properly configured network services to prevent potential breaches.
Mitigation Strategies:
- Regularly update and patch network services to address known vulnerabilities.
- Disable unnecessary services and restrict access to essential services only.
- Monitor network traffic for suspicious activities and configure firewalls to block unauthorized access.
3. Insecure Ecosystem Interfaces
The interfaces that IoT devices use to interact with different ecosystems can also be insecure, leading to unauthorized access and data breaches. Securing these interfaces is crucial to prevent cybercriminals from exploiting them to gain access to sensitive data and systems.
Mitigation Strategies:
- Regularly update and secure all ecosystem interfaces.
- Implement robust authentication and authorization mechanisms.
- Monitor interface interactions and restrict access to trusted entities only.
4. Lack of Secure Update Mechanism
A lack of secure update mechanisms can leave IoT devices vulnerable to attacks, as outdated software and firmware can be exploited by cybercriminals. Ensuring that devices can be securely updated is essential to protect against known vulnerabilities and threats.
Mitigation Strategies:
- Implement secure and authenticated update mechanisms.
- Regularly update devices with the latest security patches.
- Verify the integrity of updates before installation.
5. Use of Insecure or Outdated Components
Utilizing insecure or outdated components can expose IoT devices to various security risks, including unauthorized access and data breaches. It is crucial to use secure and up-to-date components to build a robust defense against cyber threats.
Mitigation Strategies:
- Regularly update all components and replace outdated ones.
- Conduct security assessments to identify and address component vulnerabilities.
- Ensure the secure configuration of all components.
6. Insufficient Privacy Protection
Inadequate privacy protection can lead to the exposure of sensitive user data, violating user privacy and potentially resulting in legal repercussions. It is imperative to implement sufficient privacy protection measures to safeguard user data.
Mitigation Strategies:
- Anonymize and encrypt sensitive user data.
- Implement strict data access and sharing policies.
- Regularly audit data handling and storage practices to ensure compliance with privacy laws.
7. Insecure Data Transfer and Storage
The transfer and storage of data in an insecure manner can expose it to unauthorized access and alterations. Secure data transfer and storage are crucial to maintain the integrity and confidentiality of data.
Mitigation Strategies:
- Encrypt data during transfer and at rest.
- Use secure protocols for data transfer.
- Implement secure data storage solutions and regularly backup data.
8. Lack of Device Management
Without proper device management, it becomes challenging to address vulnerabilities and ensure the security of IoT devices. Effective device management is essential to monitor and control devices securely.
Mitigation Strategies:
- Implement a comprehensive device management solution.
- Regularly monitor device status and manage device configurations securely.
- Ensure the ability to remotely disable or wipe devices if compromised.
9. Insecure Default Settings
IoT devices often come with insecure default settings, which can be easily exploited by attackers. Changing default settings to secure configurations is crucial to protect devices from unauthorized access.
Mitigation Strategies:
- Change default usernames and passwords during device setup.
- Configure device settings to the highest security level by default.
- Regularly review and update device configurations to maintain security.
10. Lack of Physical Hardening
Physical vulnerabilities can allow attackers to gain unauthorized access to devices and their data. Physical hardening is essential to protect devices from tampering and unauthorized access.
Mitigation Strategies:
- Implement physical security measures to protect devices from unauthorized access.
- Design devices with tamper-evident and tamper-resistant features.
- Regularly inspect devices for signs of tampering or physical damage.
Practical Steps for Small Businesses to Mitigate the OWASP Top 10 IoT Vulnerabilities
Small businesses can significantly enhance their IoT security by implementing the following practical steps:
- Educate employees about IoT security and promote a culture of cybersecurity awareness.
- Regularly update and patch all IoT devices and related components.
- Implement robust authentication and authorization mechanisms.
- Monitor network traffic and device interactions for suspicious activities.
- Restrict access to essential services and trusted entities only.
Conclusion
Understanding and mitigating the OWASP Top 10 IoT vulnerabilities is crucial for small businesses to secure their interconnected devices. By implementing robust security measures and fostering a culture of cybersecurity awareness, small businesses can safeguard their operations and sensitive data against potential cyber threats. The journey to a secure IoT environment begins with knowledge and proactive action, enabling small businesses to reap the benefits of IoT innovations without compromising security.
The post OWASP Top 10 IoT Vulnerabilities: How to Avoid Them! appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/owasp-iot-top-10-vulnerabilities/?utm_source=rss&utm_medium=rss&utm_campaign=owasp-iot-top-10-vulnerabilities
Original Post URL: https://securityboulevard.com/2023/09/owasp-top-10-iot-vulnerabilities-how-to-avoid-them/
Category & Tags: IoT & ICS Security,Security Bloggers Network,iot – IoT & ICS Security,Security Bloggers Network,iot