Source: www.darkreading.com – Author: Yuliya Novikova, Head of Digital Footprint Intelligence, Kaspersky
Data leaks pose a significant and escalating challenge for companies globally, particularly due to the increasing prevalence of ransomware and the growing sophistication of cyberattacks. This challenge is further complicated by the emergence of fake data leaks. Threat actors are now often seeking to capitalize on the creation of fakes. The repercussions of such fabricated leaks are far reaching. They can substantially harm the reputation of the organizations involved. Even if the leaked data is eventually proven to be false, the initial spread of misinformation can provoke unfavorable publicity.
A closer look at the nature of fake leaks can help provide guidance on how businesses can effectively mitigate the associated risks.
What Motivates Cybercriminals to Fabricate Data Leaks?
Blogs of cybercriminal groups, such as LockBit, Conti, Cl0p, and others, are a constant focus of media attention. In a way, these “bloggers” can rival celebrities or Instagram stars in terms of their publicity. Their blogs are hosted on the Dark Web and other shadow websites, while some threat actors also have their own pages on the X platform (formerly Twitter). This is where malicious actors publish information about victim companies and attempt to blackmail them, demanding ransom and setting a countdown for the release of sensitive data, such as private business correspondence, login credentials for corporate accounts, and information about employees or clients. Additionally, criminals may put data up for sale, as other threat actors might be interested in purchasing such information for further attacks.
Lesser-known cybercriminals also want to grab a piece of the attention, which pushes them to create fake leaks. These leaks not only generate hype and provoke a worried reaction from the targeted business but also serve as a fruitful way to deceive “colleagues” on the black market and sell other cybercriminals something that is not actually a leak. Novice cybercriminals are much more likely to fall for this trick.
Parse and Amass: Manipulating Databases to Pass Off as Newly Discovered Leaks
A fake data leak can take the form of a parsed database, which involves extracting information from open sources without sensitive data. Internet parsing, also known as Web scraping, refers to the extraction of text, images, links, tables, or other information from websites. With the help of parsing, threat actors can gather information for malicious purposes, including fake leaks.
In 2021, a well-known business networking platform encountered such a case when an alleged set of its users’ data was reportedly put up for sale on the Dark Web. However, subsequent investigation revealed that it was actually an aggregation of data sourced from publicly accessible user profiles and other websites, and not a data breach. This sparked a wave of attention in the media, as well as within the Dark Web community.
Whenever Dark Web offers arise claiming to provide leaked databases from popular social networks like LinkedIn, Facebook, or X, it is highly likely that these are fake leaks containing information already available publicly online. Such databases can circulate in the Dark Web for years, occasionally triggering new publications and causing alarm among targeted companies.
According to Kaspersky Digital Footprint Intelligence, between 2019 and mid-2021 there was an average of 17 posts a month about social media leaks on the Dark Web, while starting from the summer of 2021, when the aforementioned case occurred, the number of posts increased to 65 per month on average. However, many of these messages, based on our findings, may be reposts of the same database.
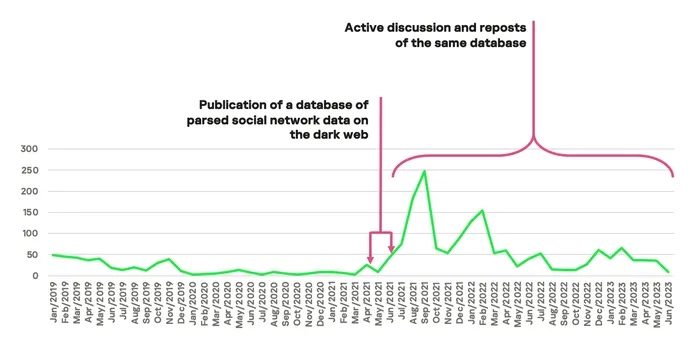
Old Is Gold: Reposting Outdated Databases
Old leaks, even if they are genuine, can also serve as a basis for creating fake leaks. When old data leaks are presented as new, it creates the illusion that cybercriminals have widespread access to sensitive information and are actively engaged in cyberattacks. This tactic can help them build a reputation among potential buyers or other criminals within underground markets.
Similar cases constantly occur within the shadow community, where even very old or unverified leaks are exposed. Data that is several years old is continuously reuploaded on Dark Web forums, sometimes offered for free and other times for a fee, masquerading as a new database. This not only poses reputational risks but also jeopardizes customer security.
Mitigating Fake Leaks: Guidance For Businesses
When faced with a fake leak, the natural response is often panic, due to the public attention it causes. However, promptly identifying and responding to fake leaks is crucial. The first steps those who are in the middle of a storm should take are to avoid contacting attackers and thoroughly investigate the reported leak. This can be done by verifying the source, cross-referencing internal data, and assessing information credibility. In other words, a company needs to collect evidence to confirm the attack and compromise.
In general, data leaks for large businesses, including fake leaks, are not a matter of if but when. Transparency and preparation are key when dealing with such significant challenges. It is useful to prepare a communication plan in advance for interacting with clients, journalists, and government agencies. Additionally, proactive monitoring of the Dark Web on a constant basis will allow for the detection of new posts about both fake and real leaks, as well as tracking spikes in malicious activity. Since Dark Web monitoring requires automation, and internal teams may not have the resources or time, external experts are often responsible for this.
Furthermore, developing comprehensive incident response plans with designated teams, communication channels, and protocols helps to promptly address these cases if they occur.
In an era where data leaks pose a constant threat to businesses, swift and proactive action is essential. By promptly identifying and responding to these incidents, conducting thorough investigations, engaging with cybersecurity experts, and collaborating with law enforcement, companies can mitigate risks, protect their reputation, and safeguard customer trust.
Original Post URL: https://www.darkreading.com/vulnerabilities-threats/how-why-cybercriminals-fabricate-data-leaks
Category & Tags: –