Source: securityboulevard.com – Author: Corey Sinclair
On 22 January, Fortra issued an advisory stating that versions of its GoAnywhere Managed File Transfer (MFT) product suffer from an authentication bypass vulnerability. GoAnywhere MFT is, as the name suggests, an enterprise solution for encrypting and transferring data within an organization and to external customers.
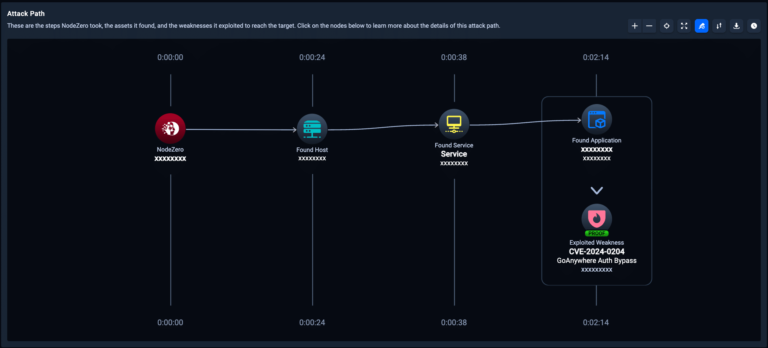
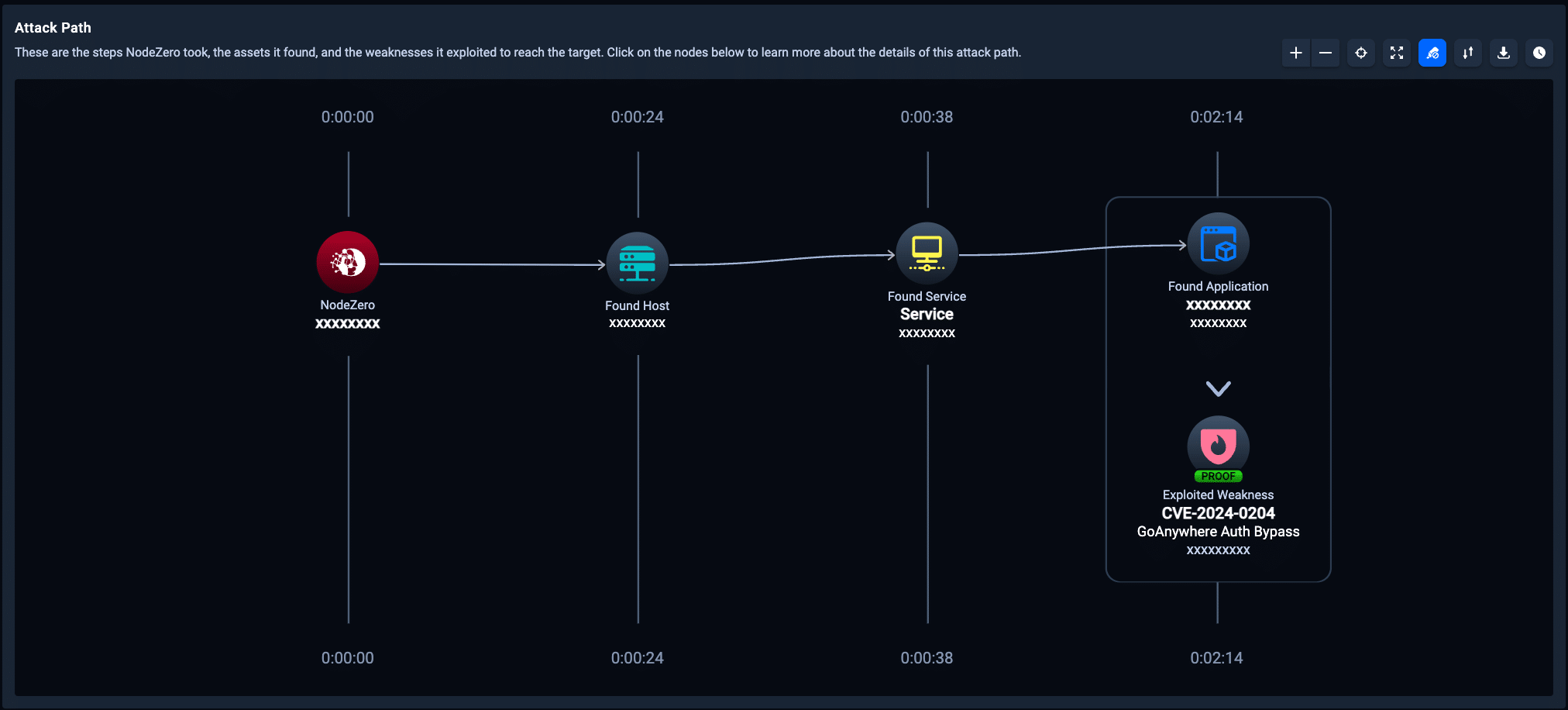
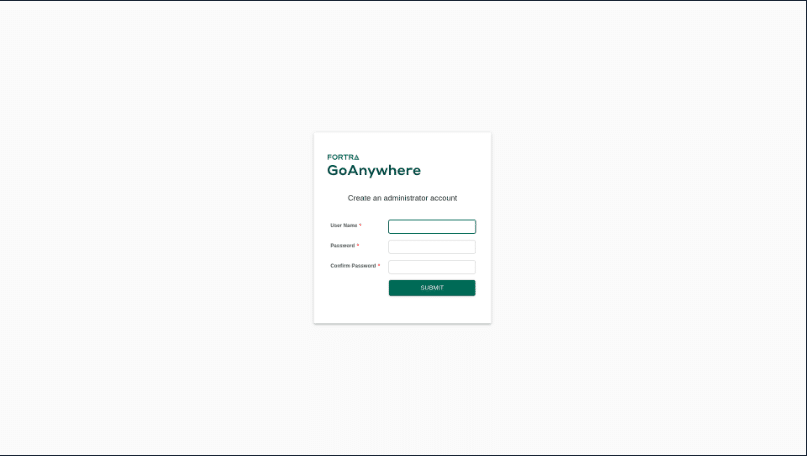
This critical vulnerability (CVSS 9.8) is tracked as CVE-2024-0204 and only affects versions of GoAnywhere MFT prior to 7.4.1. Unauthorized individuals can exploit this vulnerability to create an admin user via the administration portal.
Fortra patched the GoAnywhere vulnerability on 7 December 2023 with the release of GoAnywhere MFT 7.4.1. Fortra then publicly disclosed the vulnerability on 22 January after giving customers several weeks to patch.
While Fortra is not aware of any attacks in the wild exploiting this vulnerability, we anticipate that cyber threat actors will likely attempt to take advantage of any unpatched instances of GoAnywhere MFT now that it has been publicly acknowledged.
Who Is Affected?
Anyone who runs a version of Fortra’s GoAnywhere MFT prior to 7.4.1 may be impacted by this vulnerability. According to Fortra, GoAnywhere is the #1 secure file transfer solution and serves 4,000+ customers in 100+ countries. Organizations in healthcare, finance, insurance, transportation, government, real estate, and other industries use the solution and could be at risk of exploitation if they are not running the patched version.
How Do I Fix It?
Fortra recommends upgrading to version 7.4.1 or higher. According to Fortra, this vulnerability may also be eliminated in non-container deployments by deleting the InitialAccountSetup.xhtml file in the install directory and restarting the services. For container-deployed instances, replace the file with an empty file and restart.
How Can NodeZero™️ Help?
As of today, all users running NodeZero™️ can run an autonomous pentest to determine if their systems are vulnerable, reachable, and exploitable due to this vulnerability. We also recommend running a follow-on pentest to determine that any remediation steps taken are effective.
To read more about this vulnerability and how it works, please see the Horizon3.ai Attack Team blog titled, “CVE-2024-0204: Fortra GoAnywhere MFT Authentication Bypass Deep-Dive.”
The post CVE-2024-0204: Check Critical Fortra GoAnywhere MFT Authentication Bypass with NodeZero™️ Now! appeared first on Horizon3.ai.
*** This is a Security Bloggers Network syndicated blog from Horizon3.ai authored by Corey Sinclair. Read the original post at: https://www.horizon3.ai/cve-2024-0204-check-critical-fortra-goanywhere-mft-authentication-bypass-with-nodezero/
Original Post URL: https://securityboulevard.com/2024/01/cve-2024-0204-check-critical-fortra-goanywhere-mft-authentication-bypass-with-nodezero%EF%B8%8F-now/
Category & Tags: Security Bloggers Network,Blog,Industry Insights – Security Bloggers Network,Blog,Industry Insights