Source: securityboulevard.com – Author: Julie Peterson
CI/CD Pipeline Security
Given the demand for rapid innovation and the adoption of agile methodologies, Continuous Integration/Continuous Deployment (CI/CD) pipelines have become the foundation on which all DevOps processes are built. They are the backbone of efficient delivery.
In fact, according to to the State of Continuous Delivery report, using CI/CD tools correlates with better software delivery performance across all metrics.
These pipelines represent an incredible security risk to organizations, and the consequences can be severe. A seemingly harmless code change that makes its way through a compromised pipeline could lead to security breaches, system compromise, and significant operational disruptions. That’s why it’s essential for DevSecOps teams to follow best practices to protect every stage of the delivery process.
In this article, we’ll delve into the intricacies of CI/CD pipeline security, explore risks and vulnerabilities, and offer tips and tools to help you fortify your CI/CD pipeline against potential threats.
What Is a CI/CD Pipeline?
A CI/CD pipeline is a series of automated processes that streamline the journey from code commit to production, and eliminates manual handoffs. It’s a tightly orchestrated dance between automation and control, helping DevOps teams deliver reliable software at lightning fast speed.
Imagine a conveyor belt for software updates. Every time a developer makes a change, it automatically hops on the belt. The belt whisks the change through a series of checkpoints, like building the code, running tests, and fixing any bugs. If everything passes, the update gets delivered to users – fast and smooth!
That’s basically a CI/CD pipeline in a nutshell. CI stands for Continuous Integration, where changes are constantly merged and tested. CD stands for Continuous Delivery/Deployment, where working changes are rolled out to users.
Here’s the magic: Everything is automated. This saves developers time and effort while catching problems early. Think of it as a quality control system for software updates, making sure only the best reaches your users. So, the next time you hear CI/CD pipeline, remember that it’s just a fancy way of saying automatic software update conveyor belt.
Continuous integration acts as the first checkpoint, automatically merging code changes and triggering automated tests to ensure the new code integrates seamlessly with the existing codebase. This helps ensure errors and regressions are identified and addressed early in the development process.
Continuous delivery then takes over, packaging and staging tested code for deployment. Continuous Deployment, an extension of Continuous Delivery, goes a step beyond by automatically deploying code changes directly into production, provided they pass all necessary tests.
Importantly, the CI/CD pipeline is a crucial component of the software supply chain, and plays a significant role in the “build and release” stages.
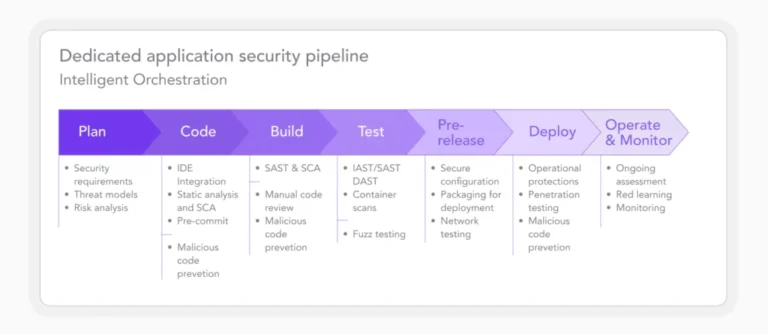
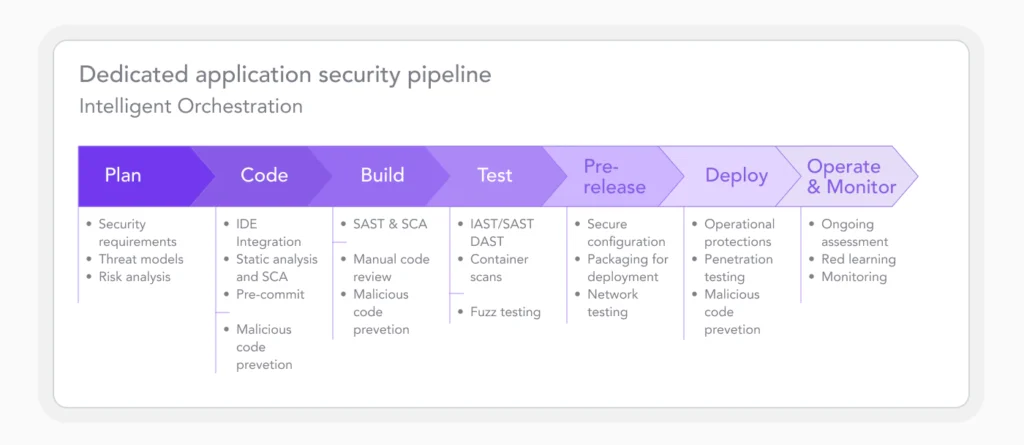
CI/CD Pipeline Stages
CI/CD pipelines have several distinct stages. Each stage plays a crucial role in the software development lifecycle (SDLC). If you want to implement robust security measures throughout the pipeline, you first have to understand the stages.
Why Is CI/CD Security Important?
CI/CD pipelines are attractive targets. Malicious actors often target CI/CD pipelines to gain access to sensitive data or manipulate code to target downstream customers. From code commit to production, every stage is a possible target. Even the most secure code is vulnerable if the pipeline itself is compromised, potentially leading to the injection of malicious code into the software as was the case with the Codecov breach in 2021. Thousands of Codecov customers were affected after attackers exfiltrated data from the CI of a build.
These breaches cost organizations millions, erode customer trust, and have a long-lasting negative impact on a brand’s reputation.
Let’s explore a few other common CI/CD security vulnerabilities before identifying solutions to help you protect your end-to-end SDLC.
Common CI/CD Security Risks
Secret Leaks
Sometimes developers inadvertently commit code containing secrets like API keys, passwords, or cryptographic keys. Attackers can exploit these exposed secrets and gain unauthorized access to critical systems and services.
This happened in 2017 to Uber, when their GitHub repository was accidentally exposed. The repository contained access credentials. Attackers discovered and exploited these credentials to gain unauthorized access to Uber’s AWS account, compromising the personal data of nearly 60 million users.
Supply Chain Attacks
Supply chain attacks target the dependencies and components used in the CI/CD pipeline. For example, an attacker might inject malicious code into a commonly used library or compromise a package manager, leading to the distribution of tainted software. That means it’s not just the targeted organization that’s affected. Customers, suppliers, partners, and other third-parties are too.
When organizations unknowingly incorporate these compromised dependencies into their CI/CD pipelines, attackers gain a foothold and can wreak havoc.
One of the most notable recent examples of a supply chain attack happened in 2020 when malicious actors compromised the SolarWinds software build process, injecting a backdoor into their Orion software updates. Organizations then unknowingly installed the compromised updates, leading to widespread breaches and unauthorized access to sensitive networks.
Misconfigurations
Misconfigurations in CI/CD tools, scripts, or infrastructure settings can expose vulnerabilities that attackers can exploit. This may include improperly configured access controls, insecure default settings, or mismanaged permissions. This may allow unauthorized users to view or modify sensitive code and configurations, compromising the overall security of the pipeline.
Code Injection
Code injection involves the introduction of malicious code into the CI/CD pipeline, potentially leading to unauthorized code execution or the introduction of vulnerabilities into the software being developed.
This is exactly what happened in 2021 when a malicious script was injected into Codecov’s CI/CD process. The compromised script exposed credentials, enabling attackers to exfiltrate sensitive information from the CI/CD environment and compromise the code repositories of multiple organizations.
Insufficient Access Controls
Weak or insufficient access controls can lead to unauthorized access to critical components of the CI/CD pipeline. This could enable them to modify code, insert malicious scripts, or compromise the pipeline’s integrity, posing a significant security risk.
This happened to LastPass in 2022 when attackers gained access to portions of their source code and proprietary technical information in their development environment. They then used this information to launch a series of attacks, including one targeted at a senior DevOps engineer with high-level security authentication.
Eventually, they stole the engineer’s master password, and gained access to encrypted secure notes and decryption keys, which opened the door to critical database backups.
This list is just a few examples of the thousands of attack paths that could lead to a compromised CI/CD pipeline. Hungry for more? The research team at NCC Group shares 10 examples of sophisticated attacks they’ve executed in this article.
CI/CD Pipeline Security Best Practices
The following best practice tips will help reduce the likelihood of a breach. Note: It’s important to consistently reevaluate your posture to keep up with evolving security standards and emerging threats.
For more tips, check this joint memo from the NSA and CISA.
Access Control
Proper access controls (including roles, permissions, and authentication mechanisms) are critical in preventing unauthorized access and manipulation of CI/CD pipelines. By limiting access to only those people who need it and enforcing the principle of least privilege, organizations can reduce the risk of malicious activities.
Code Scanning
By integrating automated code scanning into the CI/CD pipeline, issues like known vulnerabilities or common application security risks can be detected and addressed before vulnerable code is deployed. This reduces the risk of introducing vulnerabilities into the production environment.
Vulnerability Management
Stay ahead of potential threats and ensure your pipeline remains resilient by proactively identifying, prioritizing, and mitigating security vulnerabilities in software and infrastructure components. This includes regularly scanning for vulnerabilities, assessing their severity, and implementing measures to remediate or mitigate the risks.
Secure Environment Configurations
Misconfigurations can lead to security vulnerabilities, as we saw with Uber. That means properly configuring the settings for servers, containers, databases, and other components is crucial for preventing potential exploits.
Some top tips to avoid misconfigurations:
- Limit access and permissions using least privilege policies
- Use a secure and centralized method for managing environment variables
- Keep all CI/CD components up-to-date with the latest security patches
Collaboration Between DevOps and Security Teams
Effective collaboration between DevOps and security teams ensures that security is not treated as an afterthought and is embedded throughout the CI/CD process. Unfortunately, 76% of security professionals find implementing a culture of collaboration between security and developer teams challenging.
So how can teams foster a better working relationship? Buy-in and commitment from the top, training, and incentivization all help. The best method is what we call controlled shift left.
Under this model, security teams remain laser focused on reducing vulnerabilities, while also being mindful of the impact that fixing defects has on developers. This way, the two teams work together to build processes and workflows that work for everyone. With controlled shift left, developers maintain velocity, while security protects pipelines, improving the organization’s security posture.
Tools/Technology
The right tools and technologies can automate security processes, streamline vulnerability detection, and enforce security policies. Integrating these tools into CI/CD pipelines enhances the efficiency of security measures.This enables organizations to identify and address security issues while maintaining the pace of continuous delivery.
While dozens of different tools (SCA, SAST, CI/CD Security Tools) can help your organization secure its CI/CD pipeline, only one offers complete protection and peace of mind: Complete Application Security Posture Management (ASPM).
Complete ASPM offers continuous security in and of the pipeline, ingesting data from multiple sources throughout the software lifecycle and giving security teams an ongoing, real-time view of their risk. Issues are faster and easier to detect, respond to, and remediate.
A complete ASPM solution is one that provides a suite of application security testing tools like SCA and SAST, delivers CI/CD security, and ingests data from other third-party scanners.
How Cycode Can Help
Cycode’s security-first, developer-friendly ASPM platform provides visibility, prioritization, and remediation for security, engineering, and DevOps teams at every stage of the CI/CD pipeline.
By offering a single, unified security platform that correlates pipeline security, secrets scanning, code leak detection, SAST, SCA, and IaC scanning, Cycode gives security teams and developers peace of mind.
Book a demo to see the platform in action.
The post CI/CD Pipeline Security: Best Practices Beyond Build and Deploy appeared first on Cycode.
*** This is a Security Bloggers Network syndicated blog from Cycode authored by Julie Peterson. Read the original post at: https://cycode.com/blog/ci-cd-pipeline-security-best-practices/
Original Post URL: https://securityboulevard.com/2024/01/ci-cd-pipeline-security-best-practices-beyond-build-and-deploy/
Category & Tags: Application Security,Security Bloggers Network,Blog,CI/CD pipeline,software supply chain security – Application Security,Security Bloggers Network,Blog,CI/CD pipeline,software supply chain security