Source: www.bitdefender.com – Author: Graham Cluley A data breach involving the Dutch city of Eindhoven left the personal information related to almost all of its citizens...
Day: May 24, 2024
UK Government ponders major changes to ransomware response – what you need to know – Source: www.exponential-e.com
Source: www.exponential-e.com – Author: Graham Cluley What’s happened? Recorded Future has reports that the British Government is proposing sweeping change in its approach to ransomware attacks....
CISO Cite Human Error as Top IT Security Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Human error is responsible for most cybersecurity risks, with nearly three-quarters (74%) of chief information security officers (CISOs) identifying it...
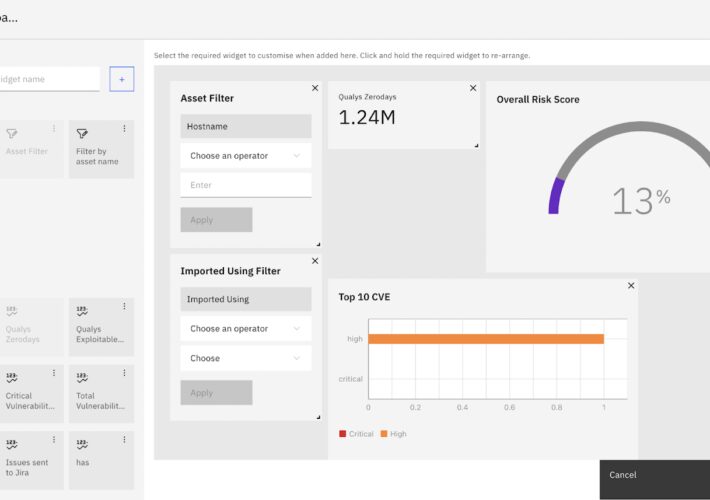
Customized Vulnerability Management Dashboard for CISOs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alibha CISOs require a central hub for visualizing critical security data. Strobes RBVM empowers you to construct impactful CISO dashboards, transforming complex...
What are the Hallmarks of Strong Software Security? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra Reading Time: 4 min Why is software security so important? Simply put, there are more threats these days and many...
Ekran System Enhances Privileged Access Management: New Workforce Password Management Feature – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ani Khachatryan At Ekran System, we constantly enhance the capabilities of our platform, ensuring that organizations have effective and up-to-date tools to...
What is Cloud Penetration Testing? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover The digital era is constantly evolving, and businesses are rapidly migrating towards cloud-based solutions to leverage the agility, scalability, and...
Guide: What is FedRAMP Tailored and What is The Difference? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh In the past, we’ve talked a lot about the various FedRAMP guidelines required to reach either a single Authority to...
Optimizing CI/CD Security: Best Practices for a Robust Software Delivery Pipeline – Source: securityboulevard.com
Source: securityboulevard.com – Author: Apurva Dave Tools Workload IAM automatically manages access. Secrets management tools such as AWS Secrets Manager or Microsoft Azure Key Vault can...
Ad Protect: Mastering the Detection of Bot-Driven Ad Fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lorenzo Vayno Digital ad fraud is taking billions out of marketing budgets, highlighting the need for precise detection tools that can identify...
Leading LLMs Insecure, Highly Vulnerable to Basic Jailbreaks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy There are significant security concerns in the deployment of leading large language models (LLMs), according to a study from U.K....
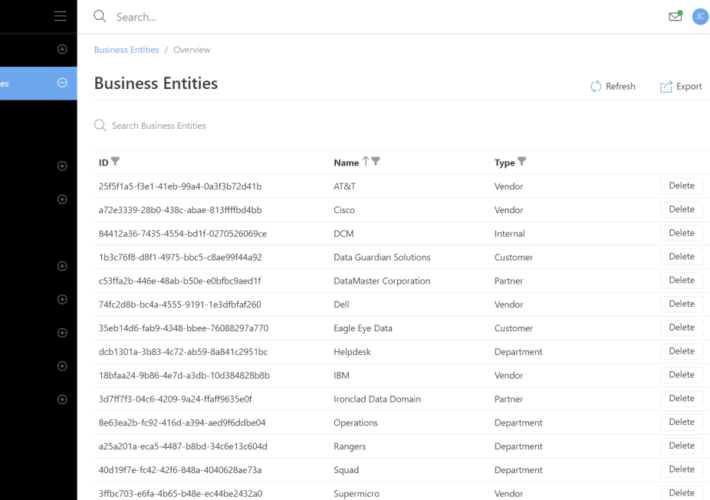
Business Entities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi We’ve introduced Business Entities, a game-changer for tracking customers, partners, and department associations with assets, connections, and circuits. Each entity...
Concentric AI to Unveil Data Security Remediation and Compliance Reporting Capabilities at Infosecurity Europe 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN MATEO, Calif., May 23, 2024 — Concentric AI, a leading vendor of intelligent AI-based solutions for autonomous data security posture management (DSPM), announced...
Seizing Control of the Cloud Security Cockpit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Bargury 3 Min Read Source: JLBvdWOLF via Alamy Stock Photo The image of a cockpit always struck me as overwhelming. So...
SOCRadar Secures $25.2M in Funding to Combat Multibillion-Dollar Cybersecurity Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEWARK, Del., May 22, 2024 /PRNewswire/ — SOCRadar, a leading provider of enterprise-grade, end-to-end threat intelligence and brand protection, today announced the successful...
Bugcrowd Acquires Informer to Enhance Attack Surface Management, Penetration Testing – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, May 23, 2024 — Bugcrowd, a leading provider of crowdsourced security, today announced it has acquired Informer, a leading provider...
Courtroom Recording Platform JAVS Hijacked in Supply Chain Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: David R. Frazier Photolibrary, Inc. via Alamy Stock Photo A Windows version of the RustDoor...
MIT Brothers Charged With Exploiting Ethereum to Steal $25 Million – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Carlos Castilla via Shutterstock Many cryptocurrency traders play fast and loose with the systems in place to...
Stalkerware App With Security Bug Discovered on Hotel Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Brian Jackson via Alamy Stock Photo A spyware app called pcTattletale was recently discovered tapping...
New Gift Card Scam Targets Retailers, Not Buyers, to Print Endless $$$ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Zoonar GmbH via Alamy Stock Photo A Moroccan threat group has upgraded the classic gift card scam...
2024: The Year of Secure Design – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Stephen de Vries, CEO, IriusRisk In 2023, we saw governments and global cybersecurity agencies begin to put the building...
6 Factors to Consider When Choosing a SIEM Solution – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Don’t Settle for Less | Make an Informed Decision By Krunal Mendapara, Chief Technology Officer, Sattrix Group In today’s world,...
Stark Industries Solutions: An Iron Hammer in the Cloud – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The homepage of Stark Industries Solutions. Two weeks before Russia invaded Ukraine in February 2022, a large, mysterious new Internet hosting...
Anthropic’s Generative AI Research Reveals More About How LLMs Affect Security and Bias – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Because large language models operate using neuron-like structures that may link many different concepts and modalities together, it can be...
IBM X-Force Report: Grandoreiro Malware Targets More Than 1,500 Banks in 60 Countries – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet A new report from IBM X-Force exposes changes in the Grandoreiro malware landscape. The banking trojan is now capable of...
Hiring Kit: GDPR Data Protection Compliance Officer – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: The European Union’s General Data Protection Regulation requires every business enterprise and public authority that collects personal data from EU customers and...