The Internet Organised Crime Threat Assessment (IOCTA) is a strategic report that provides a law enforcement-centric assessment of the latest online threats and the impact of...
Day: April 16, 2024
INCIDENT RESPONSE METHODOLOGIES
CYBER INCIDENT PLAYBOOKS This document provides several Incident Response Methodologies (IRM) aimed at helping a company with the handling of different types of cyber incidents. Compare...
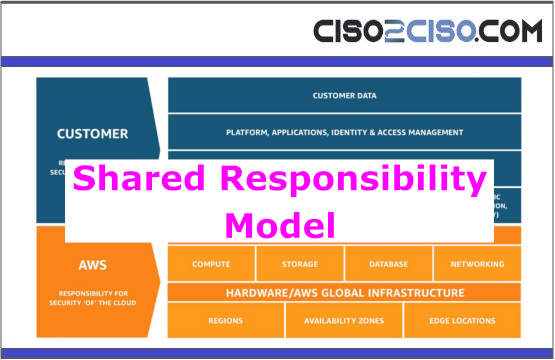
Shared Responsibility Model
The Shared Responsibility Model is crucial in cloud computing to ensure data and application security. It defines the security responsibilities between the Cloud Service Provider (CSP)...
X.com Automatically Changing Link Text but Not URLs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Brian Krebs reported that X (formerly known as Twitter) started automatically changing twitter.com links to x.com links. The problem is:...
Cyber Risk and CFOs: Over-Confidence is Costly
The document highlights the critical impact of cyber incidents on a company’s value and financial health, emphasizing the need for CFOs and CISOs to collaborate closely...
Cyber Kill Chain – A Comprehensive Overview
The document discusses the Cyber Kill Chain model developed by Lockheed Martin, which outlines the seven stages of a cyber attack: Reconnaissance, Weaponization, Delivery, Exploitation, Installation,...
Governing Through a Cyber Crisis
CYBER INCIDENT RESPONSE AND RECOVERY FOR AUSTRALIAN DIRECTORS KEY QUESTIONS Views: 2
Navigating the Cyber Typhoon: Safeguarding Data Amidst US-China Geo-Political Tensions. – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Nick Shevelyov, Senior Executive Reporter, Cyber Defense Magazine On February 7, 2024, the US Government Cybersecurity and Infrastructure Security Agency (CISA)...
CYBERSECURITY REPORT
CUJO AI’s report focuses on mobile device threats, particularly emphasizing safe browsing protection. From April to October 2023, mobile device threats were predominantly targeted at ports...
CI-CD with Docker and Kubernetes
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THE CYBER SECURITY FORUM INITIATIVE
The document outlines the CSFI Lab Validation Program, a six-month initiative aimed at enhancing computer lab operations and preparing individuals for complex cyberspace operations. It involves...
Who Stole 3.6M Tax Records from South Carolina? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over...
Crickets from Chirp Systems in Smart Lock Key Leak – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. government is warning that “smart locks” securing entry to an estimated 50,000 dwellings nationwide contain hard-coded credentials that can...
BUSINESS CONTINUITY PLAN & DISASTER RECOVERY PLAN TEMPLATE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Constructing a Robust Architecture for Digital Asset Trading Platforms
The document discusses the critical importance of the architecture of digital asset trading software in determining its success rate and attracting investors and users. It outlines...
Building a risk-resilient organisation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Credential Dumping Applications
This document outlines various methods for retrieving passwords from different applications using tools like Metasploit, LaZagne, and Mail PassView. It covers applications such as CoreFTP, FTP...
THE NEXT-GENERATION Building a Digital Central Bankfor a Digital Age
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Computer Security Incident Response Team (CSIRT)Services Framework
A Computer Security Incident Response Team is an organizational unit (which may be virtual) or a capability that provides services and support to a defined constituency...
Microsoft EntraID (Azure)ConditionalAccess
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
COMPUTER AND INFORMATION SECURITY
This comprehensive handbook serves as a professional reference to provide today’s most complete and concise view of computer security and privacy available in one volume. It...
AWS Security Incident Response Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A DETAILED GUIDE ON DIRBUSTER
The document provides an in-depth overview of DirBuster, a penetration testing tool. It covers various modes of usage such as default mode, GET request method, pure...
South Australian Cyber Security Framework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CLOUD SECURITY ENGINEER ROADMAP
The Cloud Security Engineer Roadmap provides a comprehensive guide for individuals looking to pursue a career in cloud security. It emphasizes key areas such as Linux...
Audit and Risk Assurance Committee Effectiveness Tool
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Is open source under siege? – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The recent discovery of a backdoor in XZ Utils, a core compression utility embedded in countless Linux systems, has...
MY TAKE: GenAI revolution — the transformative power of ordinary people conversing with AI – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido San Francisco, Calif. — The amazing digital services we have today wouldn’t have come to fruition without...
Five Key Takeaways from the 2024 Imperva Bad Bot Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Erez Hasson Bad bots continue to affect consumers and organizations across all sectors. For over eleven years, Imperva has been dedicated to...
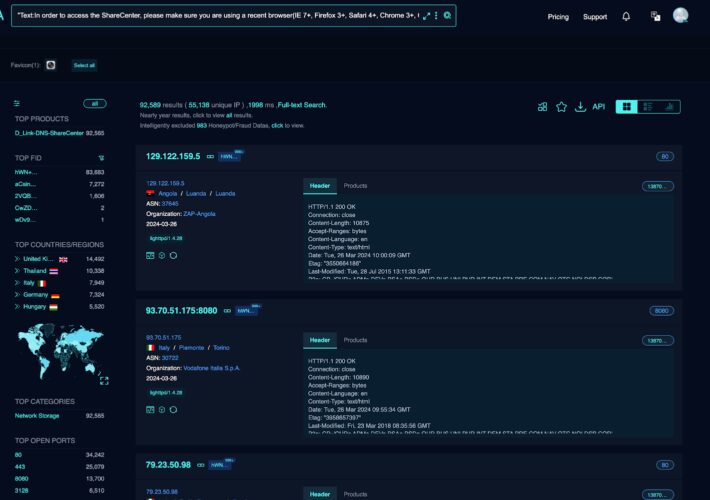
Critical RCE Vulnerability in 92,000 D-Link NAS Devices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover Cyber attacks have become increasingly prevalent. This has caused significant adverse impacts on businesses of all sizes. According to the...