The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: November 1, 2023
MANDIANT – M-Trends 2023 – Mandiant Special Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Talent Strategies for CISOs
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISOs-Practical Guide and Set of Worksheets for Building Insider Threat Program
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISOs Guide 3P Security Management
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How CEOs Can Leverage CISOs to Grow Revenue
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO PLAYBOOK: FIRST 100 DAYS Setting the CISO up for success
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Cost of Inaction – A CISOs guide for getting boards of directors to invest in cybersecurity by Microsoft Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO MIND MAP 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Modern CISO Network Board Book
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Free Book – CISO Guidance CRC Press
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Talent Strategies for CISO
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Types of AI Attacks CISOs Should Track
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
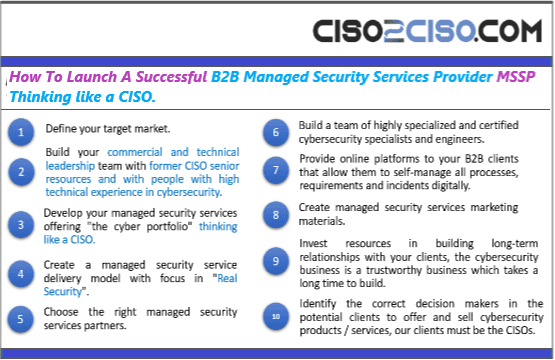
How To Launch A Successful B2B Managed Security Services Provider MSSP Thinking like a CISO
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The convergence of observability and security is critical to realizing DevSecOps potential. Dynatrace CISO report 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 Voice of the CISO – Global Insights into CISO challenges, expectactions and priorities report by proofpoint
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A CISOs Guide to Defender Alignment by exabean
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Reports – March 2023 by CISOs Club. You must see it!
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO Guidance Free Book by CRC Press
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CYBER SECURITY AWARENESS E-BOOK
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Zero Trust Architecture Model for Access Control
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The four main solutions for a Zero Trust approach
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Zero Trust Business Plan
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Zero Trust Architecture
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ChatGPT and Generative AI can strengthen Zero Trust
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Applying Zero Trust Principles to Enterprise Mobility
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
10 Ways CHATGPT and Generative AI can strenghthen ZERO TRUST by InstaSafe
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Zero Trust Security – An Enterprise Guide – Jason Garbis & Jerry Chapman – apress
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Verizon DBIR 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Boards Are Having the Wrong Conversations About Cybersecurity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...