Source: securityboulevard.com – Author: Michael Rothschild, VP of Product Marketing, HYPR

The global digital ecosystem finds itself facing a new breed of cyber threat actors: loosely organized groups with a penchant for extortion, chaos, and the desire to gain notoriety. The US Department of Homeland Security’s Cyber Safety Review Board (CSRB) recently released a comprehensive report detailing a series of cyberattacks carried out by a threat group known as Lapsus$. These attacks, which hit a zenith in 2022, targeted a range of high-profile companies and government agencies. They offer a textbook, real-world scenario highlighting systemic weaknesses and vulnerabilities in our interconnected digital infrastructure. Let’s delve into the key findings of the CSRB report and the implications they hold for organizations and individuals alike.
The Lapsus$ Watershed Moment
Lapsus$ was arguably a watershed moment because the group orchestrated a series of attacks that shook the cybersecurity community. These attacks were remarkable not because of their sophistication, but rather their effectiveness against even the most well-resourced and well-defended entities. The CSRB’s investigation revealed that Lapsus$ thrived on exploiting systemic weaknesses in the digital ecosystem, targeting vulnerabilities in downstream vendors, telecommunications providers, and even employees through social engineering tactics.
Lessons in Vulnerability
One of the most alarming findings from the report is the inadequate nature of current multi-factor authentication (MFA) implementations. Lapsus$ and similar groups were able to penetrate organizations by exploiting weaknesses in SMS and voice-based MFA methods. The attackers utilized SIM swapping attacks to intercept one-time passcodes and push notifications sent via SMS, rendering traditional MFA measures ineffective. The CSRB strongly advocates for a transition to more robust and secure passwordless authentication methods, specifically Fast IDentity Online (FIDO)2-compliant solutions, to mitigate these risks effectively. Robust FIDO2 solutions include synced passkeys for consumers and device-bound passkeys for workforce authentication.
Example of a Fraudulent SIM Swap
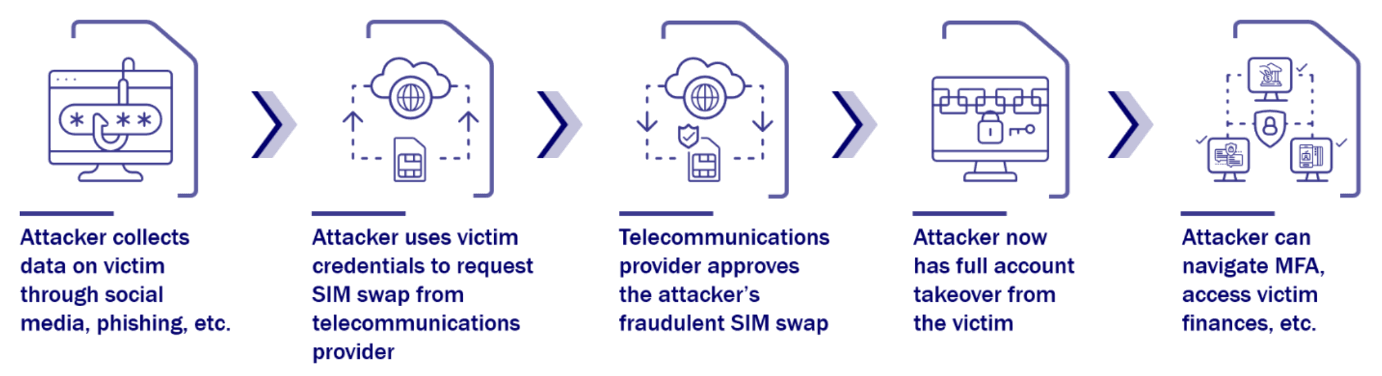
Source: Review of the Attacks Associated With Lapsus$ and Related Threat Groups, Cyber Safety Review Board, July 24, 2023
Access Controls & Third Party Connections
The report underlines the efficacy of initial access brokers (IABs) and information stealing malware, which allow cybercriminals to purchase valid login credentials for targeted organizations through the dark web. Lapsus$ leveraged these underground markets to gain entry not only to organizations themselves but also to their third-party servicers and business process outsourcers (BPOs). This highlights the importance of considering third-party risks in an organization’s risk management program, because attackers often exploit these relationships to infiltrate their ultimate targets.
Securing the Future
The CSRB report serves as a wake up call to organizations to bolster their cybersecurity defenses and prepare for the continued evolution of new and dynamic attacks which target authentication and identity-related attack vectors. Resilience against threat actor groups like Lapsus$ requires a multifaceted approach. This includes identity verification, continuous risk-based authentication, authentication that eliminates passwords and shared secrets, and well-established incident response procedures that can leverage and share insights from the extended security ecosystem.
Rounding Out The Response
The report acknowledges the crucial role of law enforcement in combating cyber threats but underscores chronic underreporting issues that hinder effective cybersecurity efforts. Furthermore, local law enforcement must have the funding, training and escalation procedures in place to investigate and react in a timely and appropriate manner in order to thwart attack attempts and minimize damage when attacks occur.
Conclusion
The lessons learned from Lapsus$ are invaluable: the need for stronger authentication methods, comprehensive access controls, a risk-based authentication approach and collaborative efforts involving both the public and private sectors. As we move forward, the report’s recommendations should serve as a roadmap to a safer and more resilient digital future.
The CSRB report on the Lapsus$ cyber threat actor group serves as a timely reminder of the vulnerabilities that persist within our interconnected digital infrastructure. While the attacks were not carried out by nation-state actors, their impact reverberated globally, highlighting the fragility of our cybersecurity defenses and the need for us all to “do better.”
![]()
*** This is a Security Bloggers Network syndicated blog from HYPR Blog authored by Michael Rothschild, VP of Product Marketing, HYPR. Read the original post at: https://blog.hypr.com/csrb-report-lessons-from-the-lapsus-threat-group
Original Post URL: https://securityboulevard.com/2023/08/unpacking-the-csrb-report-lessons-from-the-lapsus-threat-group/
Category & Tags: Identity & Access,SBN News,Security Bloggers Network,Authentication,Industry News,passwordless,Perspectives – Identity & Access,SBN News,Security Bloggers Network,Authentication,Industry News,passwordless,Perspectives






















































