Source: www.bleepingcomputer.com – Author: Sponsored by Flare

Many people associate only the dark web with drugs, crime, and leaked credentials, but in recent years a complex and interdependent cybercrime ecosystem has emerged across Tor and illicit channels on Telegram.
This trend can be exemplified by examining ransomware groups, affiliates, and the increasingly complex methods they are using to extort companies.
Ransomware has been an acute concern for organizations for more than a decade, but one of the more recent trends we see is that groups are now setting up infrastructure, but outsourcing actual infection (and in some cases negotiation) to “affiliates” who effectively act as contractors to the Ransomware as a Service (RaaS) group and split the profits at the end of a successful attacks.
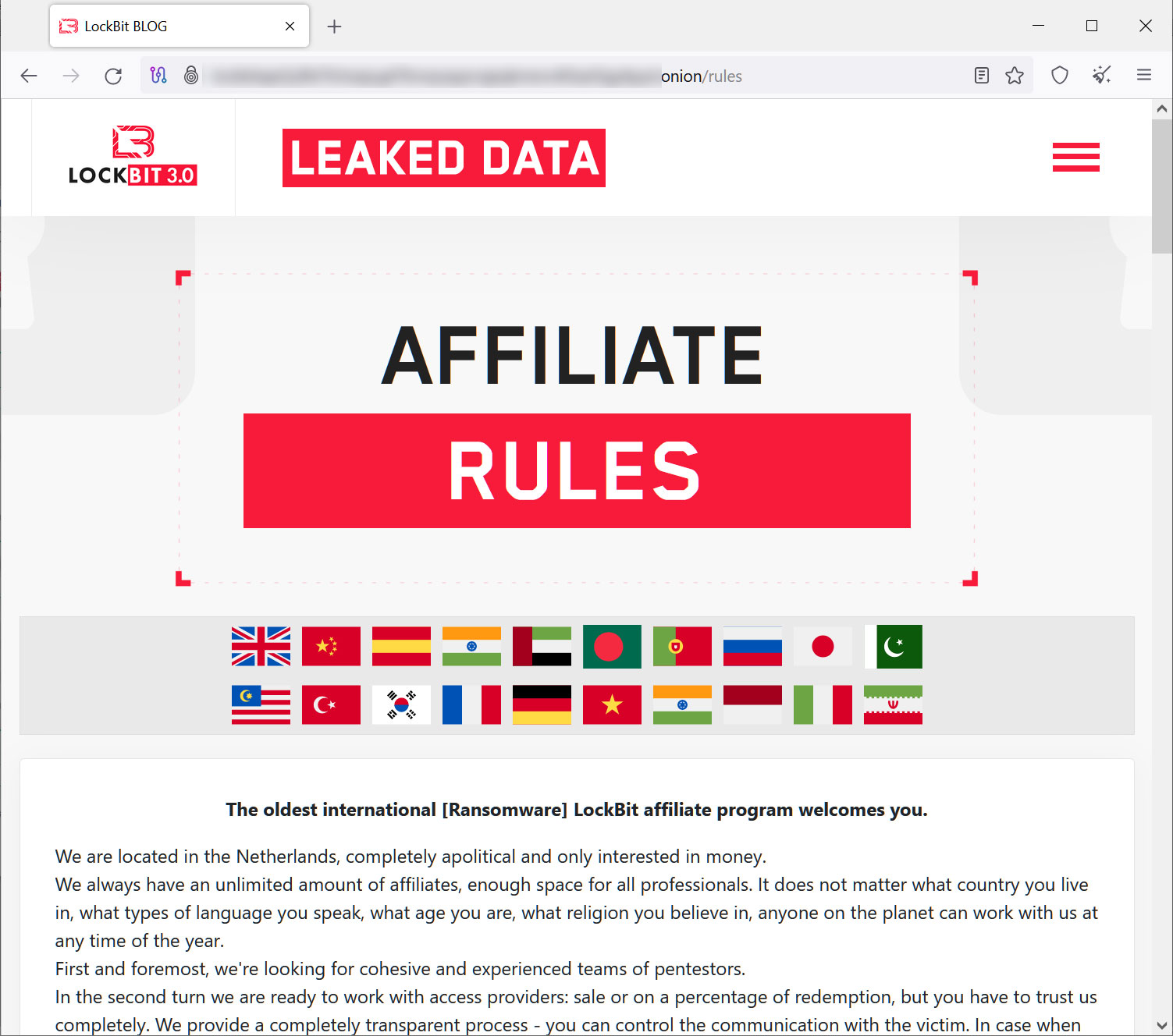
This enables role specialization and leveraging the economics principle of “economies of scale.” This “commodification of cybercrime” allows for more infections, more victims, and higher payouts.
At the same time we have seen groups resorting to increasingly sophisticated extortion tactics. A group only encrypting a company’s data is now a rarity (single extortion), with some groups entirely foregoing encryption and instead focusing on data exfiltration and employee blackmail.
Different Types of Ransomware Extortion
So what are single, double, and triple extortion attacks?
Single Extortion
This is your “traditional” ransomware attack in which a group encrypts a company’s data and requires payment for release of the data.
Double Extortion
A ransomware group encrypts a company’s data, but first exfiltrates data, which is posted on ransomware blogs on a certain date if the victim doesn’t pay.
Triple Extortion
The group not only encrypts and exfiltrates data, but also additionally attempts to:
- Target specific employees
- Conduct a DDoS attack on the company
- Notify third-parties of the company
or otherwise attempts to create additional leverage to force the victim to pay.
How Big is the Threat of Ransomware Attacks?
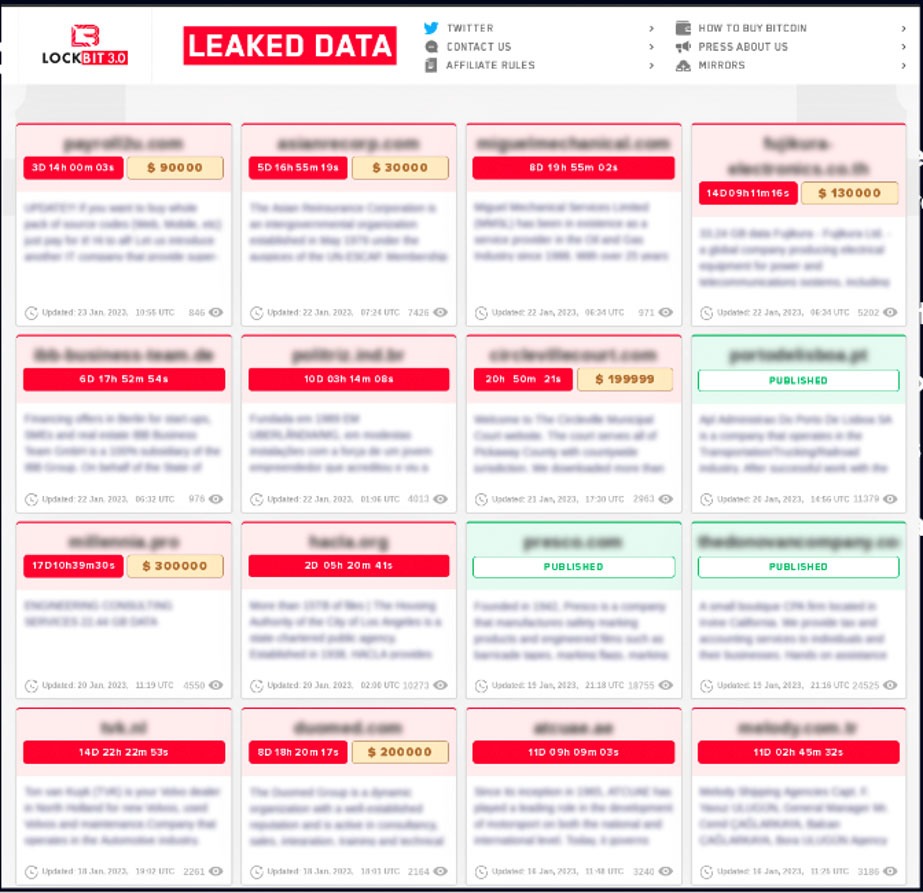
In 2022 we saw 2,947 companies’ data leaked on ransomware blogs. Undoubtedly hundreds or thousands more companies were victims and paid the ransom to avoid data disclosure.
In 2023, we’ve already seen more than 2,000 data leaks on ransomware blogs in the first six months of the year, making it likely 2023 will be a record year for ransomware data disclosure.
How Triple Extortion Ransomware Leverages the Cybercrime Ecosystem
The rise of triple extortion ransomware also directly coincides with another significant change in the threat landscape: the rise of infostealer malware.
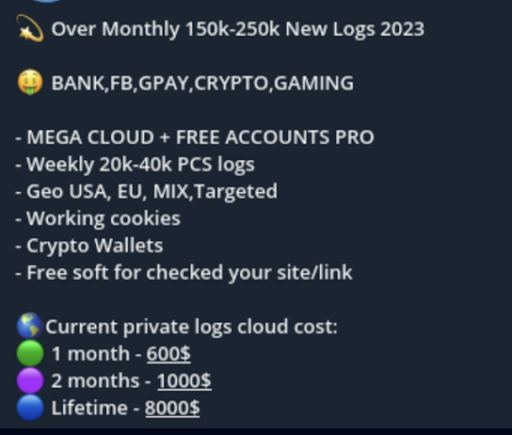
Infostealer variants such as Vidar, Redline, and Raccoon infect individual computers and exfiltrate the browser fingerprint, host data, and most importantly, all of the saved credentials in the browser.
Ransomware affiliates can easily shop for ransomware via specialized forums, then look for initial access via infected device logs posted to public Telegram channels or listed for sale on Russian or Genesis Markets.
What’s in a Stealer Log?
An individual log can contain credentials for:
- VPNs and business applications
- Online banks
- Retirement accounts
- Email addresses
- and more.
We estimate that there are a minimum of 20 million infected devices for sale across the dark web and Telegram, with a single digit percentage containing credentials to corporate environments.
Triple Extortion Attacks and Stealer Logs
Ransomware groups can also use stealer logs as part of triple extortion attacks.
We’ve seen affiliates using logs for initial access to corporate IT environments, as well as identifying already listed logs after a successful attack related to specific employees that can be exploited as a way to further pressure the organization.
Ransomware and Initial Access Brokers
Another interesting convergence we’ve seen is the rapid increase in “initial access brokers” who operate on dedicated dark web forums and specialize in establishing initial access to a company, which is then sold in auction style format to include a “buy it now price.”
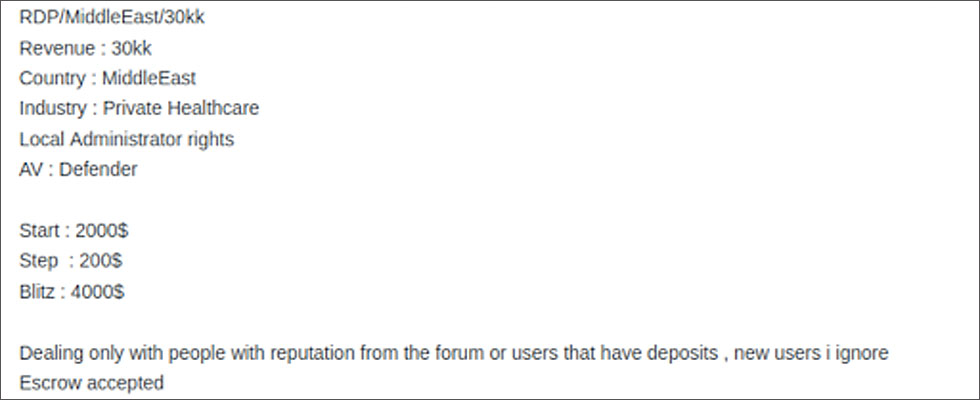
Initial access brokers further commoditize the process of infection, making it easy for threat actors to purchase access to targets prior to ransomware distribution and enabling them to do a certain amount of “shopping” for the right target.
What Does this Mean for Security Teams?
The increasing complexity of the cybercrime ecosystem is enabling an increasing number of even unsophisticated threat actors to launch sophisticated attacks against corporate environments. At Flare, we believe that building a continuous threat exposure monitoring process (CTEM) is the key to effective cybersecurity.
Gartner estimates that companies that leverage processes around CTEM will reduce the risk of a data breach by 66% in 2026.
All cyberattacks require an initial vector of access. This can be gained through traditional methods such as phishing emails and vulnerability exploits, but it can also come from developers leaking credentials onto public GitHub repositories, infostealer malware infecting employee computers, or credential stuffing attacks.
Protect Against Ransomware Attacks with Flare
Flare automatically detects company-specific threats across the clear & dark web and illicit Telegram channels, integrates into your security program in 30 minutes, and provides advanced notice of potential high-risk exposure in a single, easy-to-use SaaS platform.
We identify high-risk vectors that could enable threat actors to access your environment and provide continuous monitoring for infected devices, ransomware exposure, public GitHub secrets leaks, leaked credentials, and more.
Sign up for a free trial to learn more about protecting your organization.
Sponsored and written by Flare
Original Post URL: https://www.bleepingcomputer.com/news/security/ransomware-affiliates-triple-extortion-and-the-dark-web-ecosystem/
Category & Tags: Security – Security




















































