Source: securityboulevard.com – Author: Farah Iyer
The MITRE ATT&CK framework is a continually evolving resource, tracking the tactics, techniques, and procedures (TTPs) employed by adversaries across all phases of an attack. The recent v15 release brings valuable updates and Obsidian Security is honored to have contributed to a number of techniques contained in this release. This blog post dives into the latest additions, with a particular focus on how these changes pertain to the kill chain for SaaS identity compromise, a growing concern for all organizations.
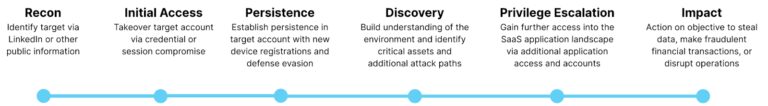
The kill chain for a SaaS identity compromise will involve several distinct stages that can be mapped to MITRE ATT&CK:
- Reconnaissance: The attacker gathers information about the target organization and its employees (T1589). This might involve techniques like obtaining IT Administrator names from LinkedIn (T1589.003) or exploiting publicly available data breaches to obtain credentials (T1589)
- Initial Access: Phishing emails with malicious links (T1598.003) remain a prevalent tactic. These links can steal login credentials or trick users into granting access to attacker-controlled resources, specifically via Adversary-in-the-Middle attacks (T1557) to intercept user’s session cookies (T1539). Attackers can also leverage built-in self-service password reset functionality to reset the target’s password to gain access to an account.
Additionally, help desk social engineering is a growing threat. These attacks involve impersonating (T1656) legitimate individuals or organizations over the phone (T1566.004), such as IT support staff, to manipulate victims into resetting passwords or disabling MFA (T1556.006), bypassing security controls.
- Persistence: After gaining initial access, attackers aim to establish persistence within the SaaS environment. This ensures continued control over compromised accounts and allows them to conduct malicious activities undetected. This may include techniques such as registering a new MFA device (T1098.005) during the initial compromise, weakening defensive postures by modifying access policies (T1556.009), creating inbox rules to avoid detection (T1564.008), and even deleting security notifications generated by the system in response to their activities (T1070.008)
- Discovery: After gaining initial access to a SaaS account, attackers transition to the discovery phase. Here, their objective is to gather valuable intel about the target organization and its systems. This information empowers them to navigate the environment, identify critical assets, and ultimately achieve their goals. Activity will include accessing all applications within the SSO dashboard (T1538), searching for passwords or password policies (T1201), identifying IT documentation containing system and network configurations (T1082), and discovering trust relationships within the authentication environment to further plan their next actions (T1482).
- Privilege Escalation: Lateral movement and privilege escalation occur and are enabled via similar tactics and techniques within the SaaS environments. Attackers will utilize native functions of the platform such as the Microsoft Graph API (T1021.007) or even modify authentication environments to federate trust to attacker-controlled domains (T1484.002) to allow for lateral movement across any valid account. In other instances, the attacker may send internal messaging via email or messaging apps (T1534) to further compromise users within the environment.
- Actions on Objectives: With access to compromised accounts, the attacker can achieve their objectives, which may involve stealing sensitive data (T1567), pivoting to internal resources via VPNs or virtual desktop environments (T1021), encrypting data via a ransomware attack (T1486), or perform fraudulent financial activity (T1657).
By documenting attacker TTPs, the MITRE ATT&CK framework empowers organizations to proactively defend against evolving threats. The latest v15 release provides invaluable insights, particularly regarding cloud and SaaS identity compromise. By aligning your security strategy to ATT&CK, you can significantly strengthen your defenses and stay ahead of the curve.
Obsidian Security is honored to have contributed to ATT&CK v15 and will continue to partner with MITRE to identify, document, and publish adversary tactics and techniques as they relate to SaaS identity compromise. You can learn more about Obsidian’s approach here.
The post MITRE ATT&CK v15: A Deeper Dive into SaaS Identity Compromise appeared first on Obsidian Security.
*** This is a Security Bloggers Network syndicated blog from Obsidian Security authored by Farah Iyer. Read the original post at: https://www.obsidiansecurity.com/blog/mitre-attack-v15-saas-identity-compromise/
Original Post URL: https://securityboulevard.com/2024/04/mitre-attck-v15-a-deeper-dive-into-saas-identity-compromise/
Category & Tags: Security Bloggers Network,FEATURED,SBN News – Security Bloggers Network,FEATURED,SBN News