Source: www.techrepublic.com – Author: Franklin Okeke
Logs and event data are becoming too labor intensive to analyze manually due to the growing cyber threat landscape. As a result, organizations now rely on Security Information and Event Management tools to collect and analyze these data types to gain actionable security insights. LogRhythm and Splunk are two prominent players in the SIEM market, and many organizations deploy them to monitor and manage security events, detect threats and ensure a robust security posture. But what distincts one from the other? This article provides a comprehensive comparison between LogRhythm and Splunk, examining their features, pricing, pros, and cons.
Jump to:
- What is LogRhythm?
- What is Splunk?
- LogRyhthm vs Splunk: comparison table
- LogRhythm and Splunk pricing
- Feature comparison: LogRythm vs Splunk
- LogRythm pros and cons
- Splunk pros and cons
- Methodology
- Should Your Organization Use LogRhythm or Splunk?
SEE: 6 SIEM myths (TechRepublic Premium)
What is LogRhythm?
LogRhythm is a software platform offering comprehensive security information and event management solutions to help organizations detect, respond, and remediate security incidents effectively. The platform combines advanced analytics, artificial intelligence, and machine learning to provide real-time monitoring, analysis, and correlation of security data from various sources. LogRhythm centralizes logs and event data management, enabling security teams to identify suspicious activities, investigate incidents, and mitigate potential risks on time.
What is Splunk?
Splunk is a unified security and observability platform designed to help organizations improve data accessibility, access to data insights, and remove data silos for better response to operational and security risks. Powered by artificial intelligence and designed with enterprise-level analytics and visualization capabilities, Splunk helps users automate investigations and respond faster to security events across their systems in real-time. Splunk’s applications span across various domains, including IT operations, security, compliance and business analytics.
LogRhythm vs Splunk: Comparison table
The following table outlines the key features found in LogRhythm and Splunk.
| Features | ||
|---|---|---|
| Real-time Monitoring | ||
| Advanced threat detection | ||
| Centralized management dashboards | ||
| Easy of deployment | ||
| Customizable dashboard | ||
| Threat remediation features | ||
| User and Entity Behavior Analytics (UEBA) | ||
LogRhythm and Splunk pricing
LogRhythm operates a flexible pricing and licensing structure that comes with unlimited log resources and users. Prices are also offered on perpetual, subscription and unlimited data basis.
For more details on LogRhythm’s pricing, contact the sales team.
Similar to LogRhythm, Splunk operates a flexible pricing model, which is captured under the following.
- Workload: Customers are charged based on the types of workload they run with the Splunk Platform.
- Ingest: Here, customers pay based on the amount of data they bring into the Splunk Platform.
- Entity: This plan is based on the number of hosts using Splunk.
- Activity-based: This is based on activities being monitored by Splunk.
Apart from the above pricing options, Splunk users also have the option to get an estimate of what they will be charged if they use Splunk.
Feature comparison: LogRythm vs Splunk
Below is a head-to-head comparison between LogRhythm and Splunk.
Deployment options
LogRythm users have flexible deployment options to match varying needs and goals. The deployment choices available to customers include self-hosting, infrastructure as a service (IaaS), or engagement with a managed security service provider. There is also a cloud deployment option with LogRhythm Cloud, which presents a software-as-a-service (SaaS) choice.
On the other hand, Splunk users can deploy the solution in a distributed search or single instance deployment. In addition, the software is also available as cloud, on-premise or multi-cloud.
Data analysis
When it comes to data analysis, LogRhythm’s Machine Data Intelligence (MDI) functionality helps users to make sense of their data. This functionality contextualizes and enriches data at the time of ingestion. It also helps to translate complex data into digestible chunks of information to enhance the accuracy of data analysis.
Splunk also has a data analytic engine designed to gather, index and manage large volumes of data, regardless of its format. Splunk’s data analytics can analyze data in real-time and dynamically generate schemas. This eliminates the need for users to have a deep understanding of the underlying data structure, as they can easily query and explore the data without any prior knowledge.
Customizable dashboard
LogRhythm allows users to customize their dashboards in ways that suit them. For instance, users can decide to customize the report template, create custom log detail reports, restore the default logo to a report, schedule and manage scheduled reports, rename a custom dashboard and decide which dashboard to make public or private.
Figure A: LogRhythm dashboard
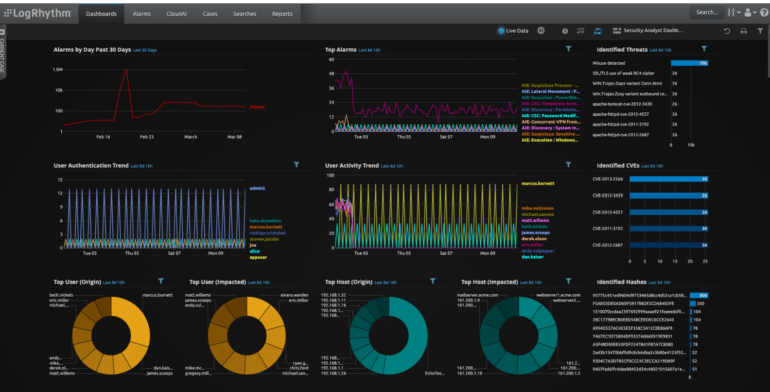
Splunk also offers a highly customizable dashboard. Users can choose from a range of charts and other virtualizations to act on their data. For instance, users can integrate reports, charts and re-usable panels to derive more insight from their data. In addition, there is also the option to tailor data for different use cases and users, such as business, security analysts, auditors, developers and operations teams, to facilitate their operations.
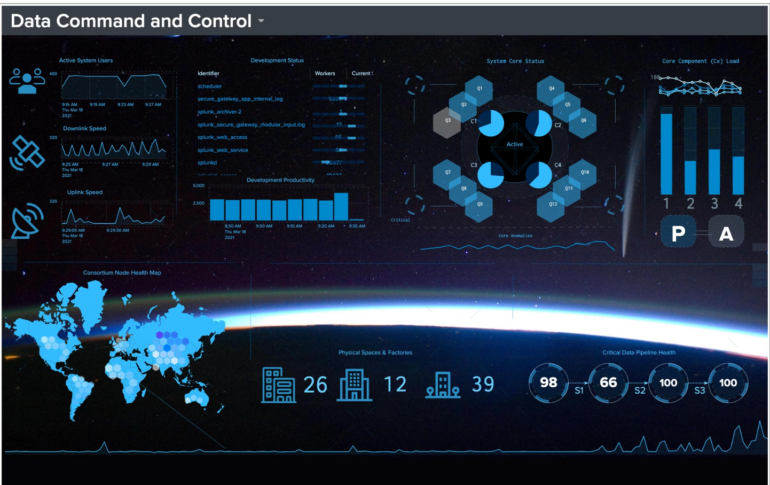
Figure B: Splunk data virtualization dashboard
Centralized log and incident management
LogRhythm offers centralized log and incident management that helps users to collect, store and analyze logs/events from various sources for auditing, compliance, and forensic purposes. There are also case management and playbooks, which offer incident management functionalities to facilitate log and incident management processes.
Similarly, Splunk also provides a central log management feature that allows users to collect and store logs from various sources in centralized storage. Users can also encrypt the logs collected to prevent unauthorized access.
Advanced threat detection
Both LogRhythm and Splunk provide users with advanced threat detection capabilities. LogRythm does this by combining machine analytics and search analytics. These functionalities offer users a risk-based monitoring strategy that can automatically identify and prioritize attacks and threats.
Splunk also rides on the power of machine learning to detect advanced threats and other 1300+ out-of-the-box detections for frameworks such as MITRE ATT&CK, NIST, CIS 20 and Kill Chain.
Figure C: Splunk executed playbook & actions
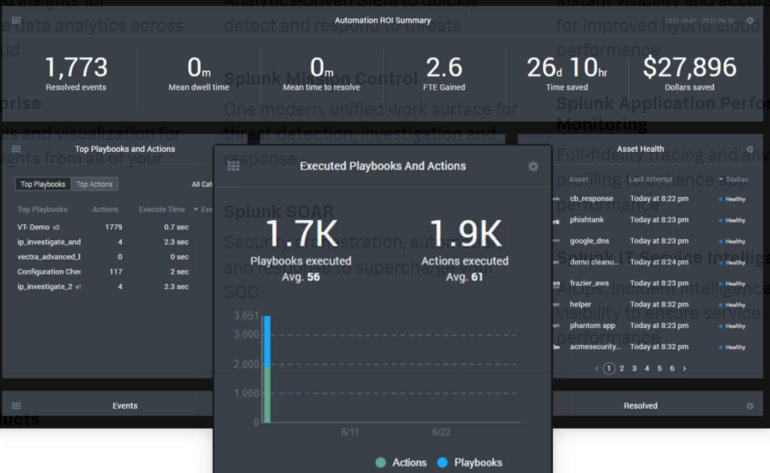
LogRythm pros and cons
Below are the key takeaways from the LogRythm SIEM solution.
Pros
- Users can map their security and IT operations to existing frameworks like MITRE ATT&CK and NIST.
- Offers real-time visibility across environments for easy identification and prioritization of potential threats.
- Centralized log management support.
- Offers User and Entity Behavior Analytics capabilities.
- Offers free training videos.
Figure D: LogRhythm UEBA
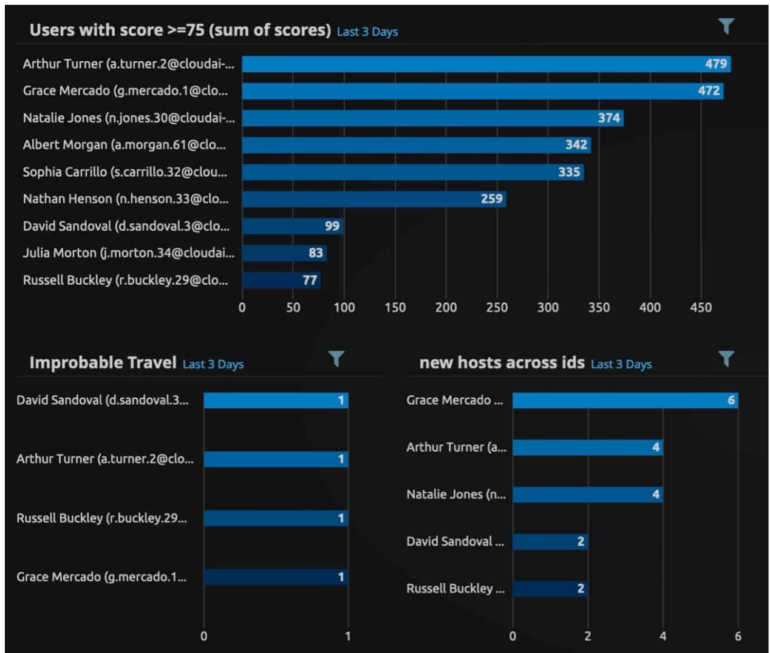
Cons
- Complicated pricing plans.
- The customization feature is not broad.
- No free trial.
Splunk pros and cons
Highlighted below are the pros and cons of Splunk.
Pros
- Powerful log analysis for log management and analysis.
- Offers a 60-day free trial.
- Advanced threat detection with machine learning and over 1300 advanced detections for popular frameworks like NIST, CIS 2, MITRE ATT&CK and Kill Chain.
- Availability of over 50 free training courses and certifications.
- Automatic security content updates for users delivered from the Splunk Threat Research Team.
- Risk-based alerting helps users to map incident alerts to cybersecurity frameworks and attribute risks to users and systems.
- Integration with popular cloud platforms, such as AWS, Azure, Google Cloud Platform.
Cons
- It is difficult to get started with Splunk.
- There is no pricing detail to give potential users a clue about what they’ll be charged.
SEE: Using Splunk in the financial services industry (TechRepublic Premium)
Methodology
This comparison is based on a comprehensive analysis of the features, capabilities, and pricing information provided by LogRhythm and Splunk, as well as insights from user reviews. It is important to note that the suitability of each SIEM tool may vary depending on your organization’s specific needs and requirements. Therefore, you should evaluate both solutions to determine their compatibility with your organization’s security strategy.
Should Your Organization Use LogRhythm or Splunk?
The choice between LogRhythm and Splunk depends on various factors, such as the organization’s size, budget, specific security needs, and expertise. LogRhythm’s comprehensive platform, UEBA capabilities, user-friendly interface and easy deployment makes it a suitable choice for organizations looking for an all-in-one SIEM solution with advanced threat detection capabilities.
On the other hand, Splunk’s powerful log management and analysis features, scalability, and customization options make it attractive for organizations seeking highly customizable and scalable log analytics capabilities. In addition, Splunk is more suitable for advanced technical users.
FEATURED PARTNERS:
1
ESET PROTECT Advanced
Protect your company computers, laptops and mobile devices with security products all managed via a cloud-based management console. The solution includes cloud sandboxing technology, preventing zero-day threats, and full disk encryption capability for enhanced data protection. ESET Protect Advanced complies with data regulation thanks to full disk encryption capabilities on Windows and macOS. Get started today!
2
Graylog
With Graylog, you get the key features you need to maintain a robust security posture. Graylog is a scalable, flexible log management and cybersecurity platform that combines SIEM, security analytics, industry-leading anomaly detection capabilities with machine learning. Built by practitioners for practitioners, Graylog Security flips the traditional SIEM application on its head by stripping out the complexity, alert noise, and high costs.
3
NINJIO Cybersecurity Awareness Training
NINJIO prepares organizations to defend against cyber threats through their engaging, video-based training courses. They earned the highest score among providers named “Customer’s Choice” in Gartner’s 2022 “Voice of the Customer” Security Awareness Computer-Based Training report. Teams love NINJIO because of their Hollywood-style microlearning episodes, each based on recent, real-world breaches. Click below to get the full Gartner report and 3 free episodes, and see why everyone loves NINJIO.
SEE: Checklist: Network and systems security (TechRepublic Premium)
Original Post URL: https://www.techrepublic.com/article/logrhythm-vs-splunk/
Category & Tags: Security,Software,cloud security,logrhythm,security identity event management,siem,splunk – Security,Software,cloud security,logrhythm,security identity event management,siem,splunk























































