- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
The Hacker News
Threat Post Cyber Security News
The Register News
Graham Cluley Security Cyber News
Databreachtoday.com
SOC Prime Cyber Security News
Welive Cyber Security News
Naked Security News
Krebs on Security Cyber News
Haxf4All Cyber Security News
Bleeping Computer Cybersecurity News
Info Security Magazine Cyber News
Cyber Talk Cybersecurity News
Security on Tech Republic News
CSO Online Cybersecurity News
Schneier on Security Cyber News
The Last Watchdog Cybersecurity News
Security Boulevard News
McAfee Security News
The Guardian Cybersecurity News
CSH Cyber Security Hub Cybersecurity News
Heimdal Security Cyber News
Security affairs Cyber News
Helpnet Security Cyber News
Cisco Security Blog Cyber News
Top Recommended Posts
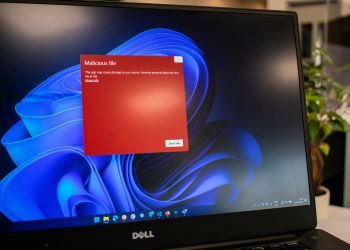
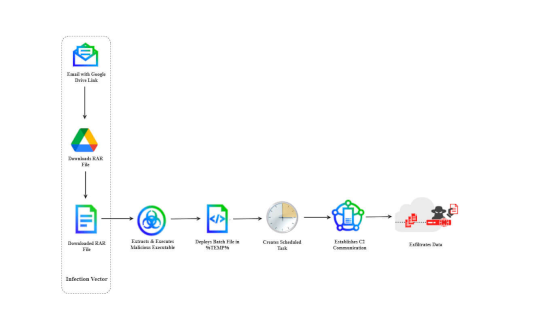
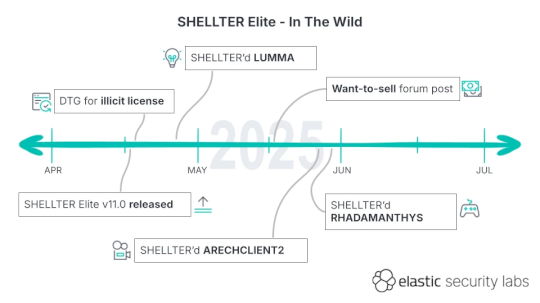
Views: 18