Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software

Our brains are incredibly good at pattern completion – it’s why we see animals in the clouds and remember entire songs from a single lyric. So, when it comes to passwords, users have a natural affinity for systems and patterns that are satisfying and easy to remember.
Even if it means circumventing an organization’s password policy. Attackers are well aware of this and have strategies in place to exploit the mistakes end users make (and the password policies that let them get away with it).
Despite being armed with modern tools and techniques, cracking passwords still essentially comes down to guessing. Any clues as to what makes up the structure of a password is very helpful to hackers.
We’ll walk through how hackers take advantage of four of the most common password mistakes users make, as well as ways to strengthen your Active Directory against these risks.
1. Common ‘base’ terms
Users tend to start with a base word when creating a password. The problem is this base word is rarely random, and usually holds some relevance to the person themselves or the company they work for. They’ll then incrementally tweak this base word during resets or expiries as a way around default password history and complexity settings in Active Directory. Most commonly, they’ll capitalize the first letter and add a special character to the end.
Attackers know they don’t need to crack the strongest passwords to get into an organization – only the weakest ones. They can exploit common base terms through dictionary attacks, where a pre-defined list of weak base terms and their common modifications are used to guess passwords or decryption keys. These attacks successfully prey upon the human tendency to opt for simplicity and familiarity when creating passwords.
The 2023 Specops Weak Password Report looked at 4.6 million passwords collected over several weeks, as well as those being used to attack RDP ports in live attacks. The most common base term? ‘password’.
You might have higher expectations in 2023, but the other most common base terms were ‘admin’ and ‘welcome.’ Social media also offers a goldmine for attackers who are targeting specific individuals, who can easily learn birthdays, family names, pets’ names, and places of significance to someone.
2. Short password length
Even with weak base terms, a hacker might still have a lot of variation to contend with. They use brute force techniques to rapidly iterate and try all potential password combinations through endless login attempts until the right one is found.
Brute force attacks are highly effective against short passwords – especially starting with common base terms found in dictionary lists in what’s known as a hybrid attack.
Specops research found that 88% of passwords used to attack RDP ports in live attacks are 12 characters or less. Many organizations only enforce an even shorter password length of eight characters through their Active Directory settings. And if a user is given the option to create a shorter password, they’re going to take it.
As the below table shows, enforcing longer password length is a highly effective defense against brute force attacks.
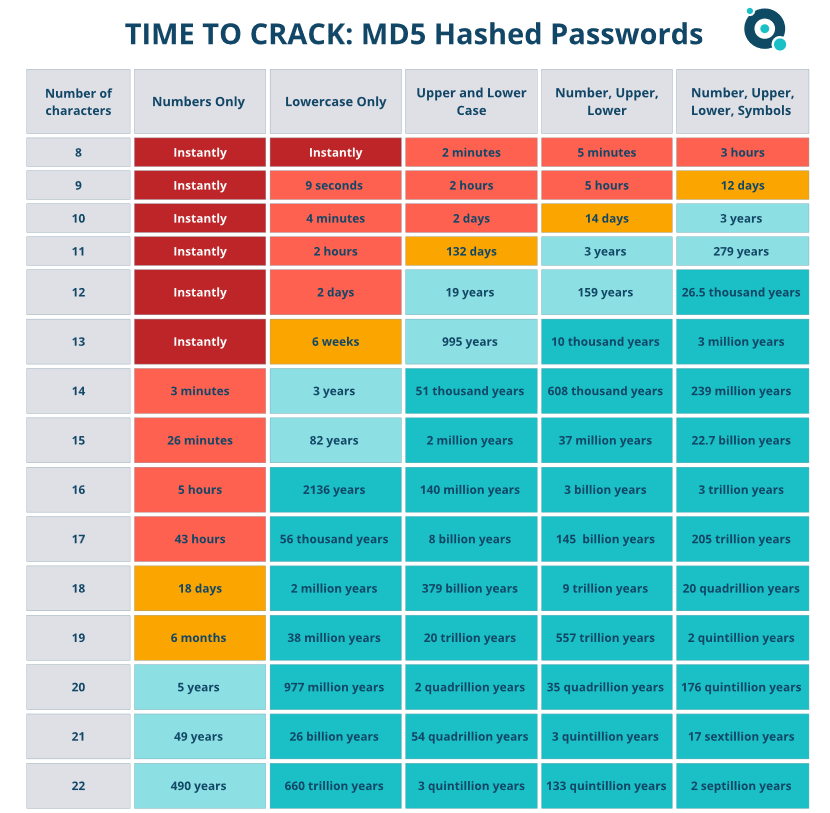
The best way to nullify the threat of brute force attacks is to encourage users to create longer passwords that are still memorable. For example, three random but memorable words strung together to create a passphrase, such as: Postbox-Throw-Calzone.
Substituting a few special characters would make this password very secure from both dictionary and brute force attacks. Another way to encourage users to create longer passwords is through length-based aging, where longer, stronger passwords can be used for a greater period of time before expiring.
3. Keyboard walk patterns
We usually think about weak, predictable passwords in terms of common base words, short length, and lack of complexity. But passwords inspired by the layout of a keyboard are just as predictable.
For example, P)o9I*u7Y^ might look like a complex password, and it would satisfy many organizations’ Active Directory password requirements. But look closer and these characters are all right next to each other, offering an easy-to-remember ‘keyboard walk’ for the end user.
The Specops team recently analyzed over 800 million passwords to find the top keyboard walk patterns among compromised passwords. The pattern ‘qwerty’ alone was found over 1 million times, emphasizing how commonly used these keyboard walks are.
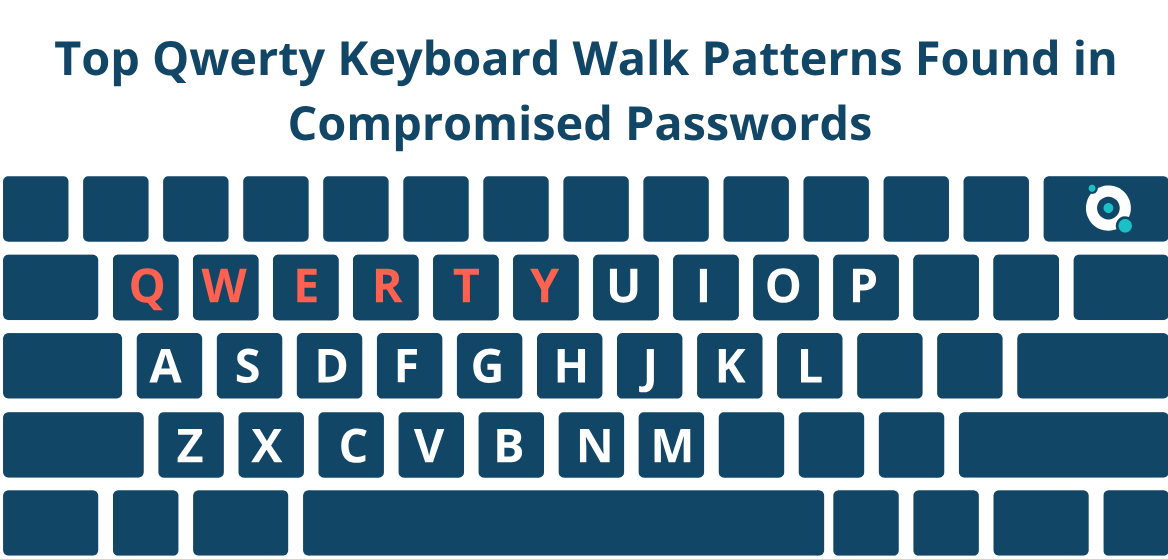
Even though patterns aren’t real words, they can still be used in dictionary attacks.
As always, attackers are ready to capitalize on the predictability of end users. They’re aware of ‘lazy fingers’ taking short keyboard walks when it comes to passwords, so they’ll add common keyboard walks to the lists of high-probability passwords used in dictionary attacks.
4. Password reuse
Strong passwords can still become compromised – and this likelihood is greatly increased if passwords are reused across applications and devices. For example, an organization might have a password manager in place, requiring the end user to only remember one very strong password.
But what if they’ve re-used that password for their Netflix, Facebook, and who knows what else? These passwords could easily be compromised by phishing attacks or other forms of data breach.
According to Google, 65% of people reuse passwords. This is partly why cybercriminals go to great lengths to steal credential information and sell it online – it’s likely a stolen password from one site could be exploited elsewhere too.
Meeting password requirements alone often isn’t enough. Specops research shows 83% of compromised passwords satisfy the length and complexity requirements of regulatory standards. You often can’t know if someone has reused their strong work password on personal sites or applications with weak security until it’s too late, so having a tool that can scan your Active Directory for compromised passwords is key.
How can organizations mitigate risks and prevent user mistakes?
A two-pronged approach is needed. First, an effective password policy that ensures users’ passwords are strong in the first place mitigates against dictionary and brute force attacks that prey on common base terms, short password length, and keyboard walk patterns.
Then a way to easily audit your Active Directory and make sure any strong passwords that become compromised through your own breach, or one elsewhere due to password reuse, are quickly changed.
Specops Password Policy allows organizations to create custom dictionaries to block base words related to their organization and industry, as well as blocking universally weak base terms, keyboard walk patterns, and short passwords.
It can also stop incremental changes to previous passwords. Essentially, you’re removing all the predictable patterns and substitutions that end users are naturally drawn to – and attackers love to exploit.
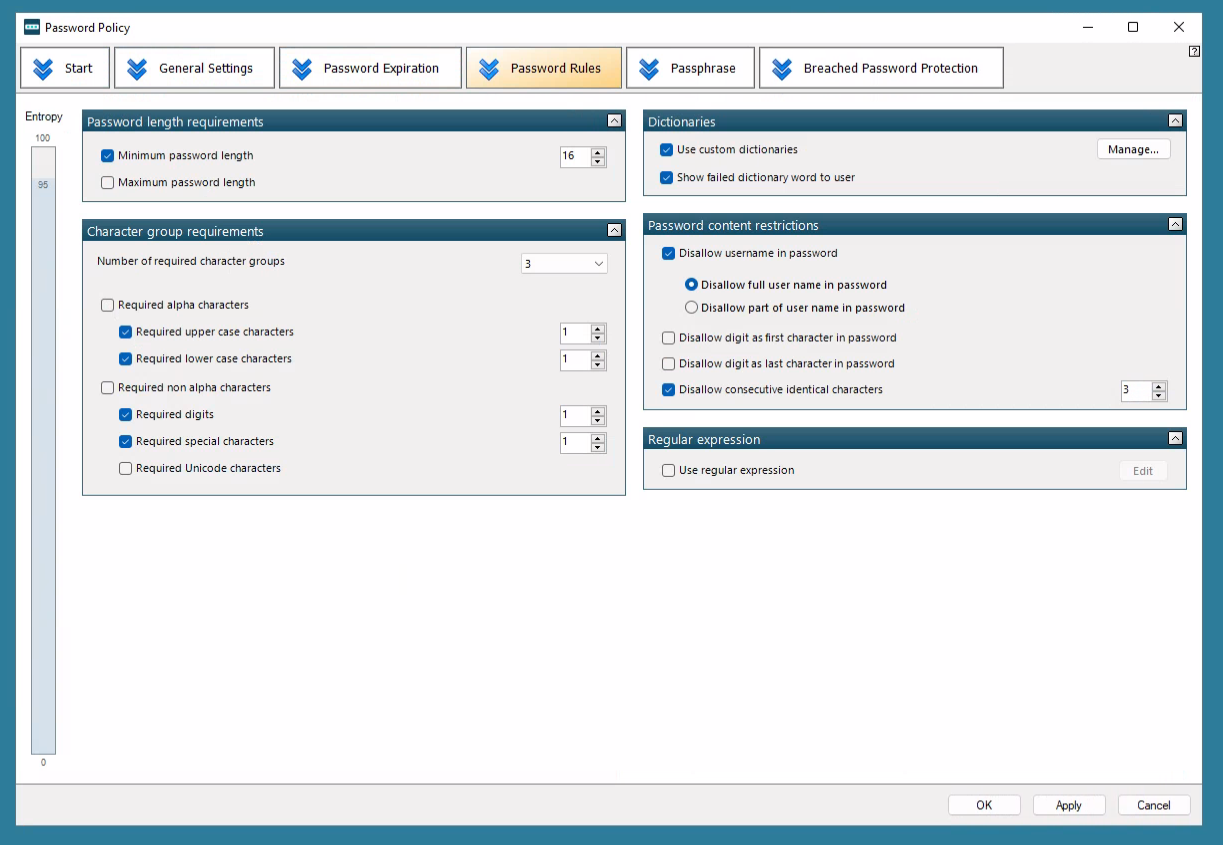
Industry regulations such as NIST and NSCSC also strongly recommend you have tools in place to detect compromised passwords. Specops Password Policy comes with a Breached Password Protection feature which checks your Active Directory against a list of over 3 billion unique compromised passwords.
The Specops’ research team updates the service daily, ensuring your users are protected from real password attacks happening right now.
Interested in taking away hackers’ favorite attack routes? Explore the capabilities with Specops Password Policy for free today.
Sponsored and written by Specops Software
Original Post URL: https://www.bleepingcomputer.com/news/security/four-common-password-mistakes-hackers-love-to-exploit/
Category & Tags: Security – Security




















































