Source: www.bleepingcomputer.com – Author: Sergiu Gatlan

Exploit code is now available for a critical authentication bypass vulnerability in Fortra’s GoAnywhere MFT (Managed File Transfer) software that allows attackers to create new admin users on unpatched instances via the administration portal.
GoAnywhere MFT is a web-based managed file transfer tool that helps organizations transfer files securely with partners and keep audit logs of who accessed all shared files.
While Fortra silently patched the bug (CVE-2024-0204) on December 7 with the release of GoAnywhere MFT 7.4.1, the company only publicly disclosed it today in an advisory offering limited information (more details are available in a private customer advisory).
However, Fortra also issued private advisories to customers on December 4 before fixing the flaw, urging them to secure their MFT services to keep their data safe.
Admins who haven’t yet and can’t immediately upgrade to the last version are advised to remove the attack vector by:
- Deleting the InitialAccountSetup.xhtml file in the installation directory and restarting the services.
- Replacing the InitialAccountSetup.xhtml file with an empty file and restarting the services.
The company told BleepingComputer on Tuesday that there have been no reports of attacks exploiting this vulnerability.
Today, almost seven weeks later, security researchers with Horizon3’s Attack Team published a technical analysis of the vulnerability and shared a proof-of-concept (PoC) exploit that helps create new admin users on vulnerable GoAnywhere MFT instances exposed online.
Their exploit takes advantage of the path traversal issue at the root of CVE-2024-0204 to access the vulnerable /InitialAccountSetup.xhtml endpoint and start the initial account setup screen (that shouldn’t be available after the server’s setup process) to create a new administrator account.
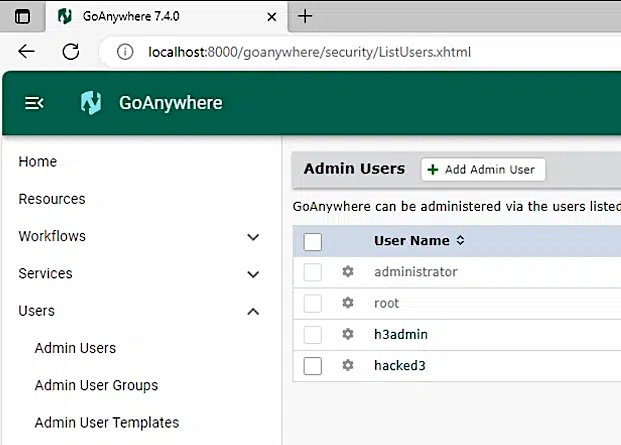
“The easiest indicator of compromise that can be analyzed is for any new additions to the ‘Admin users’ group in the GoAnywhere administrator portal Users -> Admin Users section,” said Zach Hanley, Chief Attack Engineer at Horizon3.
“If the attacker has left this user here you may be able to observe its last logon activity here to gauge an approximate date of compromise.”
However, now that Horizon3 has released a PoC exploit, it’s very likely that threat actors will start scanning for and compromise all GoAnywhere MFT instances left unpatched.
Clop’s GoAnywhere MFT breach campaign
The Clop ransomware gang breached over 100 organizations by exploiting a critical remote code execution flaw (CVE-2023-0669) in the GoAnywhere MFT software.
Clop’s attacks began on January 18, 2023, and Fortra discovered that the flaw was being weaponized to breach its customers’ secure file servers on February 3.
The list of victims who came forward after being breached and extorted by Clop includes but is not limited to healthcare giant Community Health Systems (CHS), Consumer goods giant Procter & Gamble, cybersecurity firm Rubrik, Hitachi Energy, fintech platform Hatch Bank, luxury brand retailer Saks Fifth Avenue, and the City of Toronto, Canada.
Clop’s involvement in last year’s data theft campaign is part of a much broader pattern of targeting MFT platforms in recent years.
Other instances include the breach of Accellion FTA servers in December 2020, SolarWinds Serv-U servers in 2021, and the widespread exploitation of MOVEit Transfer servers starting May 27, 2023.
Update January 23, 19:26 EST: Corrected start date for Clop’s MOVEit attacks.
Original Post URL: https://www.bleepingcomputer.com/news/security/exploit-released-for-fortra-goanywhere-mft-auth-bypass-bug/
Category & Tags: Security – Security




















































