Source: www.techrepublic.com – Author: Cedric Pernet

The Europol report reported on cybercriminals’ use of cryptocurrencies and how their techniques are more sophisticated. However, there was good cybersecurity news, too.
Europol, the European Union’s agency for law enforcement cooperation, released its yearly Internet Organised Crime Threat Assessment report, which provides key findings and emerging cybersecurity threats that impact governments, businesses and individuals in Europe; however, these threats can affect people worldwide. The main themes of the report are cybercriminals are increasingly codependent, the fundamentals of cybercrime, technically speaking, remain the same and there is a constant use of cryptocurrencies and an increased use of mixers.
Jump to:
- Increase in cybercriminals’ expertise makes them more codependent
- Modus operandi doesn’t change, techniques increase in sophistication
- Obfuscated cryptocurrencies movements
- Good news for fighting cybercrime
Increase in cybercriminals’ expertise makes them more codependent
According to Europol, the landscape of cybercrime has evolved into a complex web of interdependence among cybercriminals.
As computer security and defense evolves, cybercrime does, too. Different types of computer knowledge are needed for running fraud on the internet. For instance, depending on the fraud, a cybercriminal might need malware that isn’t detected by antivirus and security solutions, a secure internet connection that can’t be traced back to them, initial access to companies’ networks or mailboxes, efficient social engineering content, fraudulent content hosting and more.
All of those needs require deep knowledge in different fields, which is a reason why a number of cybercriminals have decided to sell their knowledge as a service to other cybercriminals.
Initial access brokers sell the compromised accesses they collect to other cybercriminals who use it for online fraud schemes. IABs are also “pivotal for ransomware attacks,” wrote Europol, as they sell initial access to ransomware groups who then use it to penetrate corporate systems to move inside their network before executing the ransomware.
Crypter developers hide malicious payloads and malware so they’re more difficult for security solutions to detect.
Counter AntiVirus services are very popular amongst cybercriminals. Malware developers and crypter services regularly use CAV services to scan their binaries against several antivirus solutions. This allows them to identify which parts of their code are flagged as malicious by antivirus engines.
Virtual private networks are provided by cybercriminals to avoid identification. Several VPN solutions are available in the cybercriminal underground market, offering anonymity by encrypting traffic from end-to-end and by not providing any cooperation with requests for information from law enforcement entities.
Bulletproof hosting is central to a lot of cybercrimes and is used by many criminals. Europol stated that those hosting services “… do not engage in extensive customer monitoring practices such as Know-Your-Customer procedures and storing of customer and metadata facilitating criminal activities.” Bulletproof hosting services don’t provide customer information to law enforcement except for an automated confirmation of an email address. Finally, hosting matters can be difficult, as it’s generally a complex international business where servers are often in multiple regions worldwide.
Andy Zollo, regional vice president for EMEA at cybersecurity company Imperva, talked with TechRepublic.
“The fact that so many cybercriminals are now operating co-dependent services is further evidence of how complex the cybercrime industry has become, and demonstrates the need for organisations to have cohesive security strategies in place that can protect applications, APIs, and their sensitive data. However, the flip side is that the growing co-dependency among cybercriminals means that if businesses are able to disrupt any part of the cybercrime supply chain, it can make a significant difference to their overall security posture. Even one solution or initiative, if well-targeted, can be enough to help break the cycle.”
Modus operandi doesn’t change, techniques increase in sophistication
All types of cybercriminals use the same methods of reaching their goals at some point. The most used technique is phishing; it’s generally always the starting point of financial fraud or cyberespionage operations.
From a technical point of view, the modus opérandi doesn’t change, but the way to achieve it gets more sophisticated and increases in volume. European Union regulatory developments have made fraud with compromised credit card information more difficult, which has the effect of turning cybercriminals more onto the users than the digital systems.
Remote Desktop Protocol brute-forcing and VPN vulnerability exploitation are the most common intrusion tactics used by cybercriminals, according to Europol. Phishing kits have also become increasingly available for cybercriminals, regardless of their level of organization and technical expertise.
SEE: TechRepublic Premium’s Brute Force and Dictionary Attacks: A Guide for IT Leaders
Obfuscated cryptocurrencies movements
When possible, cybercriminals use cryptocurrencies. Ransomware groups all request cryptocurrencies, paid directly on dedicated crypto wallets. Payments between cybercriminals for different services are also always made in cryptocurrencies.
An extensive use of several layers of obfuscation techniques is generally deployed by cybercriminals before finally cashing out their illegal profits. Cryptocurrency mixers, a service that blends the cryptocurrencies of many users together, are often used to obfuscate the origins and owners of the funds. These mixers make it difficult for investigators to trace the money trails effectively.
Another commonly employed method is cryptocurrency swappers, which allow for instant trading from one cryptocurrency to another, further complicating the process of identifying the origin of the funds. In addition, change of countries and decentralized exchanges are used for obfuscation. These cryptocurrency obfuscation techniques require highly skilled investigators to follow the money trails and conduct successful investigations.
Europol shows a complex cryptocurrency case where mixers, cryptocurrency switches and splits are heavily used (Figure A).
Figure A
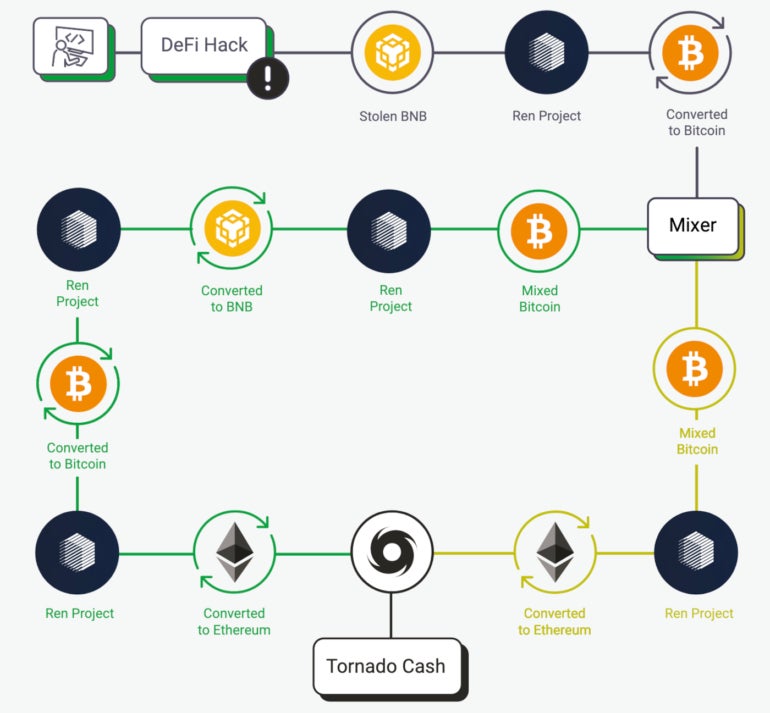
In the Decentralised Finance hack depicted in Figure A, the cryptocurrency, Binance Coin, is stolen and sent to Ren Project, a protocol that allows movement of values across blockchains. Then, it’s converted to Bitcoin before going into a mixer that splits the money in two, going back to Ren Project. It’s converted to BNB on one side and converted to Ethereum on the other side. The Ethereum amount goes through the Tornado Cash mixer before being reconverted to Ethereum.
Good news for fighting cybercrime
The time when a cybercriminal was running all of their fraud alone is coming to an end; cybercriminals want to be efficient, so they buy the services of more skilled peers rather than do it themselves. This is good news for the fight against cybercrime because arresting cybercriminals on one aspect of cybercrime generally affects others and stops a lot more fraud.
For example, Europol reported several successful international operations leading to arrests. One instance was the VPNLab takedown in 2022. Many users of VPNLab used the service to connect to domains of companies being compromised by a ransomware group. This takedown demonstrated how bringing down one service could help further investigations.
Another example is Operation Elaborate in 2022, which took down a full service that provided Automated Interactive Voice Response, interception of one-time passwords and live monitoring of calls, leading to the arrest of 142 suspects.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Original Post URL: https://www.techrepublic.com/article/europol-internet-organised-crime-threat-assessment/
Category & Tags: Developer,EU,International,Networking,Security,United Kingdom,cryptocurrencies,cybercrime,european union,europol,ransomware,supply chains – Developer,EU,International,Networking,Security,United Kingdom,cryptocurrencies,cybercrime,european union,europol,ransomware,supply chains




















































