Source: go.theregister.com – Author: Iain Thomson A judge has sentenced a disgruntled IT worker to more than seven months in prison after he wreaked havoc on...
Scattered Spider crime spree takes flight as focus turns to aviation sector – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones Just a few weeks after warning about Scattered Spider’s tactics shifting toward the insurance industry, the same experts now say...
Sinaloa drug cartel hired a cybersnoop to identify and kill FBI informants – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones A major Mexican drug cartel insider grassed on his fellow drug-peddlers back in 2018, telling the FBI that a cartel...
DragonForce actors target SimpleHelp vulnerabilities to attack MSP, customers – Source: news.sophos.com
Source: news.sophos.com – Author: gallagherseanm Ransomware actor exploited RMM to access multiple organizations; Sophos EDR blocked encryption on customer’s network Sophos MDR recently responded to a...
News alert: SquareX research finds browser AI agents are proving riskier than human employees – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido Palo Alto, Calif., Jun. 30, 2025, CyberNewswire–Every security practitioner knows that employees are the weakest link in an organization, but this...
Best Software Composition Analysis (SCA) Tools: Top 6 Solutions in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mend.io Team What you need to know about SCA tools Quick Answer: The top SCA tools in 2025 are Mend.io (best for...
Evaluating AI Solutions for the SOC: Why Centralized Autonomy Outperforms Agentic AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alex MacLachlan The cybersecurity industry is increasingly exploring AI-driven solutions to enhance Security Operations Centers (SOCs). Among these, agentic AI, comprising multiple...
The Rise of Agentic AI: Uncovering Security Risks in AI Web Agents – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sarit Yerushalmi In our first post, we introduced the world of AI web agents – defining what they are, outlining their core...
The Rise of Agentic AI: From Chatbots to Web Agents – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sarit Yerushalmi Disclaimer: This post isn’t our usual security-focused content – today we’re taking a quick detour to explore the fascinating world...
Improving NHIs Management in Your Organization – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Your Organization Harnessing the Full Power of Non-Human Identities? The increasing reliance on automation and cloud computing in industries...
Empower Your Team Through Efficient NHIs Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why Should Businesses Prioritize NHIs Management? While human identities have consistently held the limelight in cybersecurity, a lesser-known, yet equally...
Escaping SOC Burnout: State of Security 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alan Shimel Michael Fanning, CISO at Splunk, shares insights on cybersecurity challenges highlighted in the Splunk State of Security report. Key issues...
ICE’s Shiny New ‘AI’ Facial Recognition App: False Positives Ahoy! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Liberty’s existential threat, or sensible way to ID illegal immigrants? U.S. Immigration and Customs Enforcement (ICE) agents are using a new...
How 2 Ransomware Attacks on 2 Hospitals Led to 2 Deaths in Europe – Source:hackread.com
Source: hackread.com – Author: Waqas. Cybercrime is often seen as a threat to privacy or money, but recent years show it can cost lives too. Ransomware,...
SquareX Reveals that Employees are No Longer the Weakest Link, Browser AI Agents Are – Source:hackread.com
Source: hackread.com – Author: CyberNewswire. Palo Alto, California, June 30th, 2025, CyberNewsWire Every security practitioner knows that employees are the weakest link in an organization, but...
Scattered Spider Hacking Spree Continues With Airline Sector Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Hired Hacker Assists Drug Cartel in Finding, Killing FBI Sources – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Chinese Company Hikvision Banned By Canadian Government – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Airoha Chip Vulns Put Sony, Bose Earbuds & Headphones at Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
AI-Themed SEO Poisoning Attacks Spread Info, Crypto Stealers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Why Cybersecurity Should Come Before AI in Schools – Source: www.darkreading.com
Source: www.darkreading.com – Author: Crystal Morin Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
U.S. CISA adds Citrix NetScaler flaw to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Citrix NetScaler vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and...
Canada bans Hikvision over national security concerns – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Canada bans Hikvision over national security concerns, ordering the company to stop operations and barring its tech from government use....
Denmark moves to protect personal identity from deepfakes with new copyright law – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Denmark plans to let citizens copyright their face, body, and voice to combat deepfakes under a new law strengthening personal...
Ahold Delhaize data breach affected over 2.2 Million individuals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A ransomware attack on grocery giant Ahold Delhaize led to a data breach that affected more than 2.2 million people....
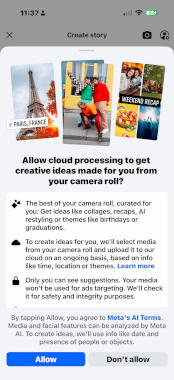
Facebook wants access to your camera roll for AI photo edits – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Facebook asks users to allow “cloud processing” to access phone photos for AI-generated collages and recaps, even if not uploaded....
U.S. Agencies Warn of Rising Iranian Cyberattacks on Defense, OT Networks, and Critical Infrastructure – Source:thehackernews.com
Source: thehackernews.com – Author: . U.S. cybersecurity and intelligence agencies have issued a joint advisory warning of potential cyber-attacks from Iranian state-sponsored or affiliated threat actors. ...
Europol Dismantles $540 Million Cryptocurrency Fraud Network, Arrests Five Suspects – Source:thehackernews.com
Source: thehackernews.com – Author: . Europol on Monday announced the takedown of a cryptocurrency investment fraud ring that laundered €460 million ($540 million) from more than...
Blind Eagle Uses Proton66 Hosting for Phishing, RAT Deployment on Colombian Banks – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actor known as Blind Eagle has been attributed with high confidence to the use of the Russian bulletproof hosting...
Leveraging Credentials As Unique Identifiers: A Pragmatic Approach To NHI Inventories – Source:thehackernews.com
Source: thehackernews.com – Author: . Identity-based attacks are on the rise. Attacks in which malicious actors assume the identity of an entity to easily gain access...