The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Report on the Biden Laptop by Marco Polo
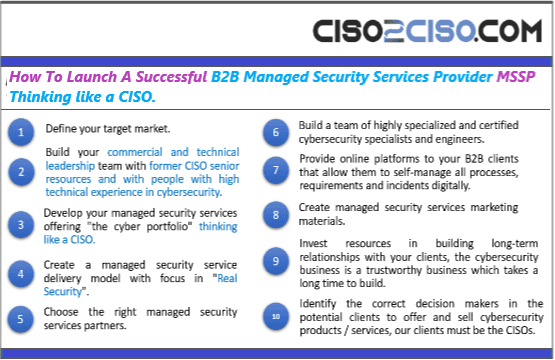
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Leaked Shellter Elite Tool Now Fueling Infostealer Attacks Worldwide – Source:hackread.com
Source: hackread.com – Author: Waqas. A new report details how the advanced hacking tool Shellter Elite was leaked and is now being used by cybercriminals. Learn...
FBI Seizes Major Sites Sharing Unreleased and Pirated Video Games – Source:hackread.com
Source: hackread.com – Author: Waqas. The Department of Justice and the FBI’s Atlanta Field Office confirmed today that they have seized and dismantled several notorious online...
New Study Shows Google Tracking Persists Even With Privacy Tools – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Google and its tracking of user activity is nothing now but a recent study by SafetyDetectives, conducted across the US,...
14 Arrested in Romania for £47 Million UK Tax Phishing Scam – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. A major international operation has led to the arrest of 14 individuals suspected of involvement in a large-scale phishing attack...
Magento 2 Shipping Automation: Cut Costs While Enhancing Customer Experience – Source:hackread.com
Source: hackread.com – Author: Owais Sultan. Imagine slashing shipping costs by 30% while speeding up deliveries, and watching 4-star reviews roll in. That is the power...
Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257) – Source:thehackernews.com
Source: thehackernews.com – Author: . Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary database...
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could allow...
Securing Data in the AI Era – Source:thehackernews.com
Source: thehackernews.com – Author: . The 2025 Data Risk Report: Enterprises face potentially serious data loss risks from AI-fueled tools. Adopting a unified, AI-driven approach to...
Critical Wing FTP Server Vulnerability (CVE-2025-47812) Actively Being Exploited in the Wild – Source:thehackernews.com
Source: thehackernews.com – Author: . A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come under active exploitation in the wild, according to...
Iranian-Backed Pay2Key Ransomware Resurfaces with 80% Profit Share for Cybercriminals – Source:thehackernews.com
Source: thehackernews.com – Author: . An Iranian-backed ransomware-as-a-service (RaaS) named Pay2Key has resurfaced in the wake of the Israel-Iran-U.S. conflict last month, offering bigger payouts to...
Taiwan NSB Alerts Public on Data Risks from Douyin, Weibo, and RedNote Over China Ties – Source:thehackernews.com
Source: thehackernews.com – Author: . Taiwan’s National Security Bureau (NSB) has warned that China-developed applications like RedNote (aka Xiaohongshu), Weibo, Douyin, WeChat, and Baidu Cloud pose...
Rowhammer Attack Demonstrated Against Nvidia GPU – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A team of researchers from the University of Toronto has demonstrated that Rohammer attacks against GPUs are possible and practical....
What is up with so many trying to hack TikTok? – Source:davinciforensics.co.za
Source: davinciforensics.co.za – Author: cyberpro. TikTok has become one of the most popular social media platforms on the net. As we have learned, the more the...
‘Hacking is assumed now’: experts raise the alarm about added risk of surveillance cameras in childcare centres – Source: www.theguardian.com
Source: www.theguardian.com – Author: Kate Lyons In the wake of horrifying reports last week alleging that eight children had been sexually abused by a worker in...
Louis Vuitton says UK customer data stolen in cyber-attack – Source: www.theguardian.com
Source: www.theguardian.com – Author: Mark Sweney Louis Vuitton has said the data of some UK customers has been stolen, as it became the latest retailer targeted...
Russian basketball player arrested in ransomware case despite being “useless with computers” – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A Russian professional basketball player has been arrested for allegedly acting as a negotiator for a ransomware gang. 26-year old...
Paddy Power and BetFair have suffered a data breach – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content The gambling firms Paddy Power and BetFair have suffered a data breach, after “an unauthorised third party”...
Tradecraft in the Information Age – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
McDonald’s AI hiring tool’s password? ‘123456’: Exposes data of 64M applicants – Source: www.csoonline.com
Source: www.csoonline.com – Author: A security flaw in McHire allowed access to sensitive applicant data via default admin credentials and a vulnerable API. The issue was...
Prorussische Hacker greifen Sachsen-Anhalts Landesportal an – Source: www.csoonline.com
Source: www.csoonline.com – Author: In Sachsen-Anhalt waren am Donnerstag mehrere Ministeriumsseiten wegen eines Cyberangriffs kurzzeitig nicht erreichbar. Nun ist klar, wer hinter dem Angriff steckt. Sachsen-Anhalts...
Anatomy of a Scattered Spider attack: A growing ransomware threat evolves – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis Jul 11, 20257 mins CyberattacksRansomwareThreat and Vulnerability Management The cybercriminal group has broadened its attack scope across several new industries,...
Customer, Employee Data Exposed in Nippon Steel Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Digital Fingerprints Tests Privacy Concerns in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
eSIM Bug in Millions of Phones Enables Spying, Takeover – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Ingram Micro Up and Running After Ransomware Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Agentic AI’s Risky MCP Backbone Opens Brand-New Attack Vectors – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
4 Arrested in UK Over M&S, Co-op, Harrods Hacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
2025 WE Local Prague Recap: Inspiring Women in Engineering and Technology
Revisit the highlights and impact of the 2025 WE Local Prague conference that inspired more than 530 women in STEM. Source Views: 0
2025 WE Local Bengaluru Recap: Advancing Women Engineers Across India and Beyond
Revisit the highlights, speakers, and photos from SWE’s 2025 WE Local Bengaluru conference. Source Views: 0
2025 WE Local U.S. Recap: Empowering Women Engineers to Rise Together
Revisit highlights from the 2025 WE Local conferences in San Jose, Cherry Hill, and Milwaukee. Source Views: 0