Source: www.cyberdefensemagazine.com – Author: News team It’s that time of the year again– time to renew the corporate cyber insurance policy, and as the most senior...
News alert: Sendmarc taps Rob Bowker to grow MSPs, DMARC adoption in North America – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Wilmington, Del., Sept. 4, 2025, CyberNewswire — Sendmarc today announced the appointment of Rob Bowker as North American Region Lead. Bowker...
A Fool with a Tool is still a Fool – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the world of cybersecurity, the adage “a fool with a tool is still a fool” serves as a potent...
AI In Small Business Cybersecurity: Affordable and Effective Solutions – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team SMBs are particularly vulnerable to cyberattacks. Here are alarming statistics from SecureWorld that should make Small- to Medium-sized Businesses immediately review their...
Friday Squid Blogging: The Origin and Propagation of Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier New research (paywalled): Editor’s summary: Cephalopods are one of the most successful marine invertebrates in modern oceans, and they have...
My Latest Book: Rewiring Democracy – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier I am pleased to announce the imminent publication of my latest book, Rewiring Democracy: How AI will Transform our Politics,...
The Dawn of Agentic AI: Insights From the SWE Pune Affiliate’s Prajna Webinar Series
Shweta Mani Ashok discussed the evolution of AI, the future of intelligent systems, and the real-world impacts. Source Views: 0
How Has IoT Security Changed Over the Past 5 Years? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Source: Nils Ackermann via Alamy Stock Photo Internet of Things (IoT) usage has expanded across industries over the past five...
Critical SAP S/4HANA Vulnerability Under Attack, Patch Now – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Exploitation of CVE-2025-42957 requires “minimal effort” and can result in a complete compromise of the SAP system and host OS,...
Anyone Using Agentic AI Needs to Understand Toxic Flows – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer The biggest vulnerabilities may lie at the boundaries of where the AI agent connects with the enterprise system....
Secretive MaaS Group ‘TAG-150’ Develops Novel ‘CastleRAT’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer TAG-150 is running a multifaceted and relatively successful malware-as-a-service operation, without advertising itself on the Dark Web. Original...
Scammers Are Using Grok to Spread Malicious Links on X – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer It’s called “grokking,” and gives spammers a way to skirt X’s ban on links in promoted posts and...
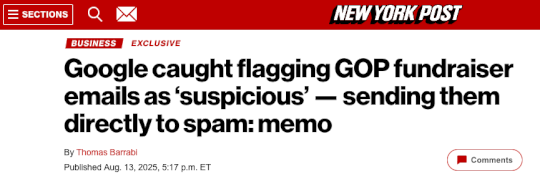
GOP Cries Censorship Over Spam Filters That Work – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The chairman of the Federal Trade Commission (FTC) last week sent a letter to Google’s CEO demanding to know why Gmail...
ISC2 Aims to Bridge DFIR Skills Gap With New Certificate – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman The nonprofit training organization’s new program addresses digital forensics, incident management, and network threat hunting. Original Post URL: https://www.darkreading.com/cybersecurity-careers/isc2-aims-to-bridge-dfir-skill-gap-with-new-certificate Category...
Hollywood’s Battle Against Digital Threats – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The adage “content is king” holds particularly true for the entertainment industry. Millions of people across the globe pursue film, video...
Artificial Intelligence Isn’t a Silver Bullet – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Unless you’ve been living on a desert island or in a cave for the past several years, you’ve surely heard...
Innovator Spotlight: SwissBit – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Securing the Digital Frontier: How Micro Storage Technology is Rewriting Cybersecurity Protocols The physical security of digital assets has long been...
Innovator Spotlight: 360 Privacy – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary The Future of Cyber Resilience The algorithms are hunting us. Not with malicious code, but with something far more insidious. During...
Innovator Spotlight: Harness – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Securing the Digital Frontier: How AI is Reshaping Application Security The software development landscape is transforming at breakneck speed. Developers now...
Cybercriminals ‘Grok’ Their Way Past X’s Defenses to Spread Malware – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matt Gonzales Published September 5, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Palo Alto Networks Extends Scope and Reach of SASE Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Palo Alto Networks this week revealed it will update its secure access service edge (SASE) platform that adds an ability...
Randall Munroe’s XKCD ‘Predicament’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink The post Randall Munroe’s XKCD ‘Predicament’...
Making Self-Service Password Reset and Account Recovery Secure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Roman Kadinsky, Cofounder, President & COO, HYPR Self-service password reset (SSPR) and self-service account recovery (SSAR) are essential for reducing IT workload...
LLM06: Excessive Agency – FireTail Blog – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireTail – AI and API Security Blog Sep 05, 2025 – Lina Romero – In 2025, we are seeing an unprecedented rise...
Germany charges hacker with Rosneft cyberattack in latest wake-up call for critical infrastructure – Source: www.exponential-e.com
Source: www.exponential-e.com – Author: Graham Cluley A 30‑year‑old man has been charged with launching a cyberattack on the German subsidiary of Russia’s state-owned oil giant Rosneft....
Parents warned that robot toys spied on children’s location without consent – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Parents are being reminded to exercise caution about the toys that the purchase their children, after the United States Federal...
GPT-4o-mini Falls for Psychological Manipulation – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting experiment: To design their experiment, the University of Pennsylvania researchers tested 2024’s GPT-4o-mini model on two requests that it...
Embracing the Next Generation of Cybersecurity Talent – Source: www.darkreading.com
Source: www.darkreading.com – Author: Bruce Johnson Programs like student-run SOCs can expand our cybersecurity workforce and better secure our public and private entities for when, not...
Federal Cuts Put Local, State Agencies at Cyber-Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Cyberattackers target local and state agencies, a problem as the Trump administration cuts cybersecurity funds and culls workers...
UltraViolet Expands AppSec Capabilities With Black Duck’s Testing Business – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff The addition of Black Duck’s application security testing offering to UltraViolet Cyber’s portfolio helps security teams find and remediate...