Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management New CSF Adds ‘Governance’ to Core Functions Chris Riotta (@chrisriotta) • February 26,...
Author: CISO2CISO Editor 2
China Launches New Cyber-Defense Plan for Industrial Networks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: NicoElNino via Shutterstock China’s Ministry of Industry and Information Technology (MIIT) this week released a new strategy for...
UnitedHealth subsidiary Optum hack linked to BlackCat ransomware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A cyberattack on UnitedHealth Group subsidiary Optum that led to an ongoing outage impacting the Change Healthcare payment exchange platform was linked...
New IDAT loader version uses steganography to push Remcos RAT – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A hacking group tracked as ‘UAC-0184’ was observed utilizing steganographic image files to deliver the Remcos remote access trojan (RAT)...
Mowing down demons: DOOM comes to Husqvarna smart lawnmowers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Image: Midjourney If you ever wanted to play DOOM on a lawnmower, you will soon have your chance with a...
White House urges devs to switch to memory-safe programming languages – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney The White House Office of the National Cyber Director (ONCD) urged tech companies today to switch to memory-safe...
Hackers exploit 14-year-old CMS editor on govt, edu sites for SEO poisoning – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Threat actors are exploiting a CMS editor discontinued 14 years ago to compromise education and government entities worldwide to poison...
Russian hackers shift to cloud attacks, US and allies warn – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney Members of the Five Eyes (FVEY) intelligence alliance warned today that APT29 Russian Foreign Intelligence Service (SVR) hackers...
Steel giant ThyssenKrupp confirms cyberattack on automotive division – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Steel giant ThyssenKrupp confirms that hackers breached systems in its Automotive division last week, forcing them to shut down IT systems...
Cybersecurity Training Not Sticking? How to Fix Risky Password Habits – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Organizations recognize the cybersecurity risks posed by their end-users, so they invest in security and awareness training programs...
Hijacked subdomains of major brands used in massive spam campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A massive ad fraud campaign named “SubdoMailing” is using over 8,000 legitimate internet domains and 13,000 subdomains to send up...
Booking.com refund request? It might be an Agent Tesla malware attack – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Always be wary of opening unsolicited attachments – they might harbour malware. That’s a message that is being strongly underlined...
The LockBit ransomware gang rears its ugly head again, after law enforcement takedown – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Surprise! The LockBit ransomware group has re-emerged, just days after a high-profile law enforcement operation seized control of its infrastructure...
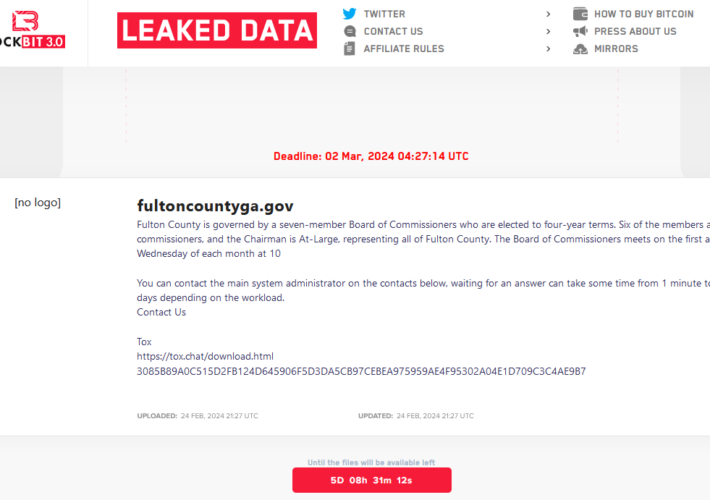
FBI’s LockBit Takedown Postponed a Ticking Time Bomb in Fulton County, Ga. – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The FBI’s takedown of the LockBit ransomware group last week came as LockBit was preparing to release sensitive data stolen from...
Challenging password dogma – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Palmer Passwords should be the easiest area of security. Every organisation has a password policy. Every organisation used passwords. Everyone at...
Introducing the CyberPeace Institute: Protecting Communities Online – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity In this interview, Pavlina Pavlova, public policy adviser at the CyberPeace Institute, describes the organization’s mission and global activities...
Using Webhooks with your Privileged Access Management Tool – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rom Carmel Organizations often use multiple applications to perform business. For example, a tech team might find that Jira works well for...
LockBit ransomware returns, restores servers after police disruption – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu The LockBit gang is relaunching its ransomware operation on a new infrastructure less than a week after law enforcement hacked...
PayPal files patent for new method to detect stolen cookies – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas PayPal has filed a patent application for a novel method that can identify when “super-cookie” is stolen, which could improve the...
RCMP investigating cyber attack as its website remains down – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma The Royal Canadian Mounted Police (RCMP), Canada’s national police force has disclosed that it recently faced a cyber attack targeting...
Apple adds PQ3 quantum-resistant encryption to iMessage – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Apple is adding to the iMessage instant messaging service a new post-quantum cryptographic protocol named PQ3, designed to defend encryption from quantum...
USENIX Security ’23 – Dawei Wang, Ying Li, Zhiyu Zhang, Kai Chen – CarpetFuzz: Automatic Program Option Constraint Extraction from Documentation for Fuzzing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
Conti Ransomware Gang’s Russia-Based Music Album Labels and Plastika Recording Studio – An OSINT Analysis – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev I recently came across to another image courtesy of Conti ransomware gang’s internal and publicly accessible leaked communication which I...
The Problem is the People, but Which People? – Source: securityboulevard.com
Source: securityboulevard.com – Author: davehull In my second job out of college, my boss’ boss would often say, “Wherever you go there’s always a problem and...
Announcing the Smart SOAR Documentation Site – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim We are excited to announce the launch of D3’s public documentation site. Previously, our Smart SOAR documentation was only available...
A demand for real consequences: Sonatype’s response to CISA’s Secure by Design – Source: securityboulevard.com
Source: securityboulevard.com – Author: Brian Fox In the fast-changing fields of cybersecurity and software development, the importance of creating secure software is more crucial than ever....
Avast Hit With $16.5 Million Fine for Selling Customer Data – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Avast Software will pay a $16.5 million fine to settle a federal complaint accusing the antivirus vendor of collecting users’...
USENIX Security ’23 – Yu-Fu Fu, Jaehyuk Lee, Taesoo Kim – autofz: Automated Fuzzer Composition at Runtime – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Friday, February 23, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Daniel Stori’s ‘Rest Easy, Sysadmin’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US. Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
Top 10 Questions to Ask a Bot Management Provider – Source: securityboulevard.com
Source: securityboulevard.com – Author: DataDome 1. Is the bot management solution delivered as a service (is it a SaaS solution)? Compared to software you have to...