Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Patch Management Gateway Maker Says Technique Won’t Succeed in Live Customer Environment Mihir...
Author: CISO2CISO Editor 2
Live Webinar | Proactive Protection: Mitigating Cyber Exposure with Actionable Insights – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Chris Poulin Director of Technology and Strategy and Deputy CTO, Bitsight Chris Poulin has over 35 years of experience in information...
Live Webinar | Innovate and Secure: How AI is Changing the Game in Secrets Scanning – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Joe Nicastro Field CTO, Legit Security Joe Nicastro is a seasoned cybersecurity expert with over a decade of experience in the...
Alert: Info Stealers Target Stored Browser Credentials – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Multi-factor & Risk-based Authentication , Security Operations Calls Grow to Block Browser-Based Password Storage as Malware Comes Calling Mathew J. Schwartz...
Strengthening OT Defense, Zero Trust: SSH’s Strategic Vision – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Operational Technology (OT) , Video Rami Raulas on Why SSH Plans to Invest in Zero Trust,...
Bolstering IoT Cybersecurity Amid an Evolving Landscape: A CEO’s Perspective – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Ron Konezny, President & CEO, Digi International The most cybersecurity-savvy members of an organization are typically not the key...
Wireless Peripheral Devices – Security Risk, Exploits and Remediation – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team This article covers the importance of Wireless Peripheral Device Security, the risks involved, and ways to remediate the security exploits....
With The World Distracted, China Stirs Trouble in The Asia Pacific – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Stan Vitek, Resident Geopolitical Analyst, Cyfirma Introduction – Thrilla in Manilla President Biden warned that “conflict and chaos could...
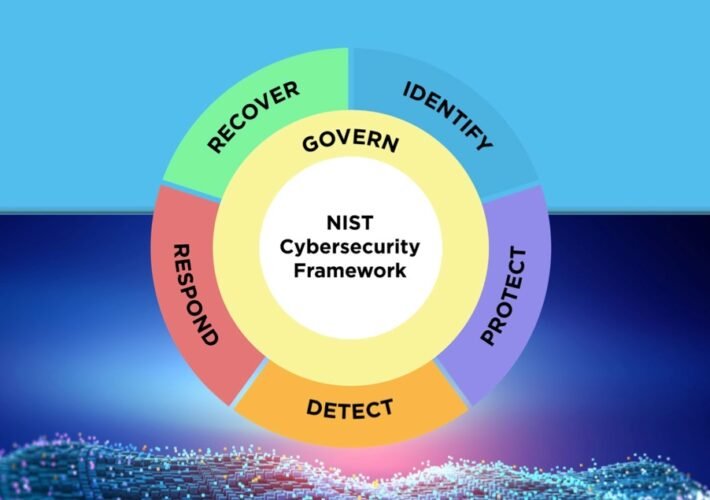
NIST Cybersecurity Framework: A Cheat Sheet for Professionals – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The National Institute of Standards and Technology has updated its Cybersecurity Framework for 2024. Version 2.0 of the NIST CSF,...
UK’s NCSC Issues Warning as SVR Hackers Target Cloud Services – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Owen Hughes Russian state hackers are adapting their techniques to target organizations moving to the cloud, an advisory from the UK National...
Someone is hacking 3D printers to warn owners of a security flaw – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Do you have an Anycubic Kobra 2 Pro/Plus/Max 3D printer? Did you know it has a security vulnerability? If you...
Act now to stop WordPress and Tumblr selling your content to AI firms – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley If you’ve spent the last umpteen years pouring blood, sweat, and tears into creating content for your Tumblr or WordPress.com...
The Week in Ransomware – March 1st 2024 – Healthcare under siege – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Ransomware attacks on healthcare over the last few months have been relentless, with numerous ransomware operations targeting hospitals and medical...
Taiwan’s Biggest Telco Breached by Suspected Chinese Hackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: BSTAR IMAGES via Alamy Stock Photo Taiwan’s Defense Ministry is urging Chunghwa Telecom, the the island’s largest telecom...
NIST Cybersecurity Framework 2.0: 4 Steps to Get Started – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: National Institute of Standards and Technology The US National Institute of Standards and Technology (NIST) has released...
CryptoChameleon Attackers Target Apple, Okta Users With Tech Support Gambit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo A phishing kit dubbed CryptoChameleon has been discovered...
Biometrics Regulation Heats Up, Portending Compliance Headaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Strom Source: Skorzewiak via Alamy Stock Photo This year might be a boon for biometric privacy legislation. The topic is heating...
Tips on Managing Diverse Security Teams – Source: www.darkreading.com
Source: www.darkreading.com – Author: Gourav Nagar Source: Sergey Pykhonin via Alamy Stock Vector COMMENTARY Long before I was a cybersecurity manager, I was an individual contributor....
Infrastructure Cyberattacks, AI-Powered Threats Pummel Africa – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: CG Alex via Shutterstock Most major economies in Africa experienced fewer overall cyber threats in 2023, but...
Hugging Face AI Platform Riddled With 100 Malicious Code-Execution Models – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: WrightStudio via Alamy Stock Photo Researchers have discovered about 100 machine learning (ML) models that have been...
MTTR: The Most Important Security Metric – Source: www.darkreading.com
Source: www.darkreading.com – Author: Harshil Parikh Source: Borka Kiss via Alamy Stock Photo COMMENTARY Reducing risk has long been the guiding principle for security teams. However,...
Ransomware-as-a-Service Spawns Wave of Cyberattacks in Middle East & Africa – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden, Contributing Writer Source: Audrey Popov via Shutterstock Ransomware-as-a-service (RaaS) affiliates are fueling a huge surge in ransomware attacks in the...
Echoes of SolarWinds in New ‘Silver SAML’ Attack Technique – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: shaneinsweden via Shutterstock After the threat actor behind the SolarWinds attack compromised the company’s Orion network management...
Cyber Threat Assessment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harman Singh In the digital landscape, what you don’t know can hurt you. The unseen threats lurking in the shadows of your...
Zscaler CEO: Palo Alto Playing Defense as Firewall Sales Ebb – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Network Firewalls, Network Access Control , SASE Jay Chaudhry Says Palo Alto Offering Free Products to...
Dashlane Free vs. Premium: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
NordPass Free vs. Premium: Is It Worth the Upgrade? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Proton VPN Free vs. Premium: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
RoboForm Free vs. Paid: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Free VPN vs Paid VPN: Which One Is Right for You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Nicole Rennolds We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...