Source: securityboulevard.com – Author: Wajahat Raja As per recent reports, threat actors are increasingly leveraging Facebook messages to distribute the Python Snake Info Stealer malware. Researchers...
Author: CISO2CISO Editor 2
CyRC Vulnerability Advisory: CVE-2023-7060 Missing Security Control in Zephyr OS IP Packet Handling – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kari Hulkko Exploitation IP address spoofing involves creating IP packets with a fake source IP address. This is typically done with the...
Aligning With NSA’s Cloud Security Guidance: Four Takeaways – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shelley Leveson, Director of Content Marketing, HYPR The National Security Agency (NSA), in conjunction with the Cybersecurity and Infrastructure Security Agency (CISA),...
Bridging the Gap: Integrating SOCs into Application Security for Enhanced Cyber Resilience – Source: securityboulevard.com
Source: securityboulevard.com – Author: Neatsun Ziv Historically, Security Operations Centers (SOCs) and Application Security (AppSec) programs have operated as distinct entities within the broader cybersecurity framework...
How to Build a Phishing Playbook Part 3: Playbook Development – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kartik Subramanian, Engineering Welcome the third part of our series on how to build an automated incident response playbook for phishing threats...
USENIX Security ’23 – How The Great Firewall Of China Detects And Blocks Fully Encrypted Traffic – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Mingshi Wu, Jackson Sippe, Danesh Sivakumar, Jack Burg, Peter Anderson, Xiaokang Wang, Kevin Bock, Amir Houmansadr, Dave Levin, Eric...
Why an Identity-First Security Strategy Is so Important – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Ramesh With the turn of the 20th century and the rise of the internet, transactions and services became increasingly digital –...
Dataproof Uses LogRhythm’s SOC Services to Deliver End-to-End Cyber Resilience in Africa – Source: securityboulevard.com
Source: securityboulevard.com – Author: LogRhythm Dataproof Communications is a leading IT Services and Consulting Company specializing in cybersecurity operations, best practices, and technologies. Based in Johannesburg,...
Five Key Findings from the 2023 FBI Internet Crime Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to...
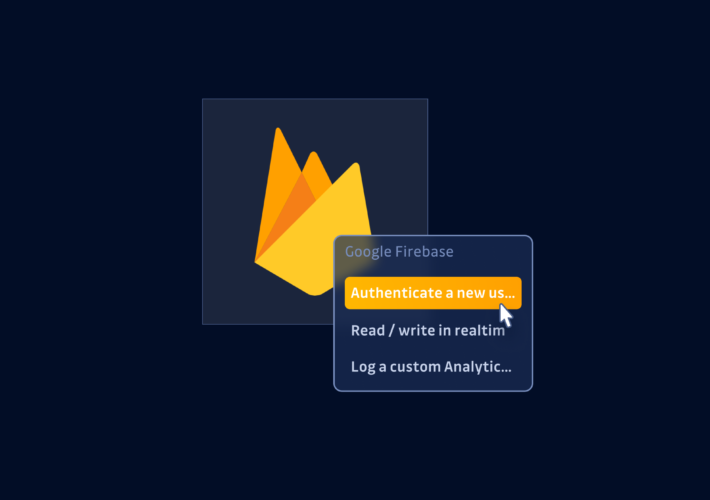
Misconfigurations in Google Firebase lead to over 19.8 million leaked secrets – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel On March 19th, news broke that researchers uncovered more than 19.8 million plaintext credentials publicly exposed through instances of Google’s...
US House Passes Bill Curbing Data Sales to Foreign Foes – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific The Vote to Restrict the Sale of Americans’ Sensitive Personal Data Is...
The Widening Career Opportunities for New College Graduates – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Recruitment & Reskilling Strategy , Training & Security Leadership New Grads Can Analyze IoT Data, Bring Talent and Innovative Thinking to...
Which Cyber Vendor Will Be First Off the IPO Starting Block? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Governance & Risk Management , IT Risk Management Cato Networks, Rubrik, Snyk Are Interested in Going Public, But...
US Sanctions ‘Key Actors’ in Russian Disinformation Campaign – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Media Treasury Department Sanctions Heads of Russian ‘Influence-for-Hire’ Firms Chris Riotta (@chrisriotta) • March 20,...
Webinar | Hackers’ Holy Grail: Insights into the Compromised Credentials Crisis – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 James Condon Director of Security Research, Lacework James Condon is Director of Security Research at Lacework, where he leads the Lacework...
Live Webinar | Attack Surface Management: Actionable Insights Against New, Known and Unknown Threats – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Chris Poulin Director of Technology and Strategy and Deputy CTO, Bitsight Chris Poulin has over 35 years of experience in information...
US CISA Urges Preventative Actions Against Volt Typhoon – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Make Sure You Have Logs, Five Eyes Alliance Says Mihir Bagwe (MihirBagwe)...
Email Bomb Attacks: Filling Up Inboxes and Servers Near You – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 DDoS Protection , Email Security & Protection , Fraud Management & Cybercrime HHS: Bot-Driven Attacks Can Overwhelm Email Servers, Networks and...
‘Fluffy Wolf’ Spreads Meta Stealer in Corporate Phishing Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Marco Arduino via Alamy Stock Photo An emerging and unsophisticated threat actor is spreading various types of...
Understanding Your Attack Surface: AI or bust – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aravind Iyengar Creating an accurate inventory of an organization’s assets and applications while ensuring no duplicates or omissions is essential for any...
Quantum Computing: A New Dawn for Encryption Vulnerabilities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Encryption & Key Management , Fraud Management & Cybercrime Expert Perspectives on Protecting Data and Developing Quantum-Safe Cryptography Michael...
Live Webinar | Identity Security in 2024: The Key to Compliance in Today’s Regulatory Landscape – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Jeff Purrington Advisory Strategist, SailPoint Jeff is an Identity Strategist with SailPoint with experience in Identity Security, as well as many...
AI Infused with XDR, SIEM, and Threat Intelligence Set to Reshape Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Microsoft Security Copilot , Next-Generation Technologies & Secure Development Information Security Media Group • March 18, 2024 Today’s security...
Ransomware Groups: Trust Us. Uh, Don’t. – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Review of Attacks Finds Inconsistent Data Leaks and Victim Naming, Broken Promises Mathew J. Schwartz...
A Career in Combating Cryptocurrency Scams – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cryptocurrency Fraud , Fraud Management & Cybercrime , Fraud Risk Management We Need Cryptocurrency Forensics Now More Than Ever Before Steve...
Planning for Healthcare IT Resiliency on a Regional Basis – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 It’s critical for hospitals and other firms to not only prepare for how they will respond to a cyberattack, but also...
Properly Vetting AI Before It’s Deployed in Healthcare – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , AI-Based Attacks , Artificial Intelligence & Machine Learning Attorney Lee Kim of HIMSS Discusses Evolving Tech...
Protecting Medical Devices Against Future Cyberthreats – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare organizations and makers of medical devices need to think about how to safeguard their critical medical gear against future cyberthreats,...
Transforming a Cyber Program in the Aftermath of an Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Incident & Breach Response , Next-Generation Technologies & Secure Development Mark Johnson, CISO of Hackensack Meridian Health, Describes...
Webinar | Compromised Credentials in 2024: What to Know about the World’s #1 Attack Vector – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 James Condon Director of Security Research, Lacework James Condon is Director of Security Research at Lacework, where he leads the Lacework...