Source: securityboulevard.com – Author: Shelley Leveson, Director of Content Marketing, HYPR

The National Security Agency (NSA), in conjunction with the Cybersecurity and Infrastructure Security Agency (CISA), recently released its “Top Ten Cloud Security Mitigation Strategies” for organizations to make their cloud environments more secure. The report contains a Cybersecurity Information Sheet (CSI) for each strategy, which includes MITRE ATT&CK and D3FEND mappings and cloud-specific mitigation guidance.
The agency emphasizes that these measures are critical for every company that uses cloud services as these environments are increasingly targeted by malicious cyber actors (MCAs). Earlier this year, the NSA, CISA and a host of international cybersecurity agencies issued a joint advisory analyzing the way that advanced persistent threat (APT) groups are evolving their tactics, techniques and procedures (TTPs) to focus on initial access and disruption of cloud services. The new guidance provides mitigation strategies to counter these threats.
Full strategy list:
- Uphold the cloud shared responsibility model
- Use secure cloud identity and access management practices
- Use secure cloud key management practices
- Implement network segmentation and encryption in cloud environments
- Secure data in the cloud
- Defending continuous integration/continuous delivery environments
- Enforce secure automated deployment practices through infrastructure as code
- Account for complexities introduced by hybrid cloud and multi-cloud environments
- Mitigate risks from managed service providers in cloud environments
- Manage cloud logs for effective threat hunting
NSA Cloud Security Guidance Takeaway #1: Cloud Security Starts With Identity Security
Much of the guidance centers on having a robust identity security program. Insufficiently secure identity systems leave organizations exposed to any number of threats including phishing, man-in-the-middle attacks, identity fraud, MFA bombing attacks and more. Last year saw a 71% spike in cyberattacks that exploited stolen or compromised credentials, according to IBM’s 2024 threat report, accounting for 30% of attacks. The report also revealed that 90% of the cloud assets for sale on the dark web were cloud account credentials.
Two of the top strategies directly relate to secure identity practices, and several others on the list call out the need to protect credentials and the threat posed by passwords and shared secrets. Specifically, the guidance recommends the use of phishing-resistant MFA as widely as possible. It defines phishing resistant methods as FIDO standards based public key cryptography or PKI-based CAC/PIV cards, pointing to the phishing-resistant MFA fact sheet issued earlier by CISA.
Example of phishing-resistant multi-factor authentication flow:
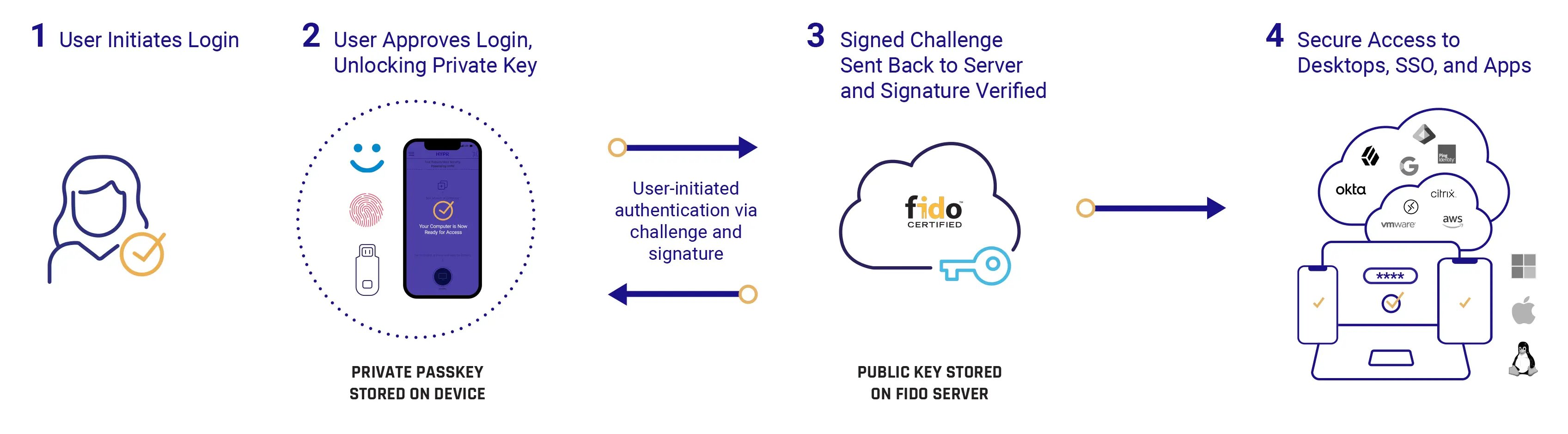
NSA Cloud Security Guidance Takeaway #2: Context Is King
Multiple measures in the guidance emphasize the need for detailed contextual information about the system’s activity and behavior. This data is critical to govern access and drive appropriate and timely responses to potential threats. For example, the report highlights the need for context-based authentication, using conditions such as geo location
The effectiveness of such context-based access controls depends on the fidelity of the information flow, which in turn depends on monitoring risk from a wide variety of sources. Ideally, an organization’s cloud identity control systems would leverage the same risk data being collected for threat hunting.
NSA Cloud Security Guidance Takeaway #3: Minimize Complexity
Before rolling out MFA and other cloud security solutions, it’s crucial to fully understand the range of scenarios they’ll be used in. The NSA guidance cautions against an uncoordinated approach, which can leave gaps in coverage and create complexity. Using multiple IAM systems and different authenticators can create confusion for users and hinder adoption. It also makes it harder to manage and monitor security effectively.
This becomes especially critical in multi-cloud and hybrid environments. Attackers move back and forth between on-prem and cloud environments. The guidance recommends the organizations implement identity solutions that can unify disparate systems and support all of their use cases. Authentication protocols should follow the NIST SP 800-63 Digital Identity Guidelines.
NSA Cloud Security Guidance Takeaway #4: Embrace Zero Trust Principles
Whether you’re of the camp that Zero Trust is a marketing buzzword, or if it’s your guiding north star, the principles behind Zero Trust are solid security best practices. A Zero Trust approach makes data, systems, and networks harder for attackers to compromise in the first place, and slows them down if they do manage to get a foothold. Much of the NSA Cloud Security guidance is, in effect, Zero Trust tenets made actionable, starting with Zero Trust authentication and least-privilege access control, to strong cryptographic protocols and network segmentation. Implicit in all of the guidance is to bake in Zero Trust best practices as you migrate to the cloud. It’s harder to re-architect already established systems, especially if there is not adequate segregation of duties. For example, your authentication systems should be separate from your IdP.
Tips for Implementing Phishing-Resistant MFA
The NSA recommendation for phishing-resistant MFA stands out as one of the simplest yet most effective strategies. Until now, it’s been the high-stakes sectors like financial services, insurance, and critical infrastructure leading the charge in adopting phishing-resistant controls. The NSA guidance makes clear that it’s time for security teams across the board to catch up. Here are some things to keep in mind:
- Prioritize a consistent experience. Users want a simple login process that is the same across cloud systems and resources as well as other channels. Employ independent, phishing-resistant authentication controls that work with multiple identity sources to provide a uniform experience.
- Take a phased approach. Start with critical systems and high-risk users to minimize disruption and maximize impact. As you troubleshoot and succeed, gradually extend the approach to wider systems and user groups.
- Beware of FIDO imitators. There is a vast difference between “FIDO-like” or “FIDO-compliant” and “FIDO Certified.” Verify vendors’ certifications on the FIDO website, ensuring all solution components, authenticators and servers, are certified.
How Organizations Can Meet NSA Cloud Security Provisions
The new guidance from NSA underscores the critical role identity plays in fortifying cloud security defenses. With malicious actors increasingly targeting cloud environments, and specifically identity systems, following recommended best practices becomes indispensable. The rapid weaponization of generative AI in attacks makes this even more critical.
HYPR’s Identity Assurance platform, which includes HYPR Authenticate, HYPR Adapt, and HYPR Affirm, ensures that identity security meets NSA standards. It combines advanced passkey-based authentication with adaptive identity risk management, automated identity verification, and a user-friendly experience.
HYPR Authenticate provides highly secure FIDO-based, phishing-resistant MFA. It ensures that biometric templates are linked to individual devices, addressing privacy and security concerns while following NSA guidelines. It covers all user groups and scenarios, from desktop to cloud environments.
HYPR Adapt provides real-time identity risk monitoring and mitigation. It collects and analyzes extensive, diverse data sources, including intelligence from your EDR and SIEM systems. Customizable policies can trigger step-up authentication, identity re-verification, or deny access, based on risk signals, aligning with Zero Trust Architecture principles.
HYPR Affirm integrates intelligent identity verification into an organization’s identity and authentication processes, covering daily as well as high-risk moments. It also maintains an auditable attestation trail in line with NSA guidance.
To learn more about the NSA cloud security strategies and how HYPR helps you meet them, get in touch with one of our identity security experts.
![]()
*** This is a Security Bloggers Network syndicated blog from HYPR Blog authored by Shelley Leveson, Director of Content Marketing, HYPR. Read the original post at: https://blog.hypr.com/nsa-cloud-security-guidance
Original Post URL: https://securityboulevard.com/2024/03/aligning-with-nsas-cloud-security-guidance-four-takeaways/
Category & Tags: Identity & Access,SBN News,Security Bloggers Network,Authentication,FIDO,Industry News,passwordless,risk compliance – Identity & Access,SBN News,Security Bloggers Network,Authentication,FIDO,Industry News,passwordless,risk compliance





















































