Source: securityboulevard.com – Author: Rohan Timalsina On May 2, 2024, the City of Helsinki announced the data breach targeting its Education Division. However, the breach was...
Author: CISO2CISO Editor 2
Don’t Expect Cybersecurity ‘Magic’ From GPT-4o, Experts Warn – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Open Questions: Degree to Which OpenAI’s Tool Hallucinates, Security of AI Model Rashmi Ramesh (rashmiramesh_) • May 27, 2024 ...
Will Australia Ever Dig Itself Out of the Cybersecurity Skills Shortage? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matthew Sainsbury Australia continues to grapple with the ramifications of a massive cyber security skills shortage, underscored by another recent large-scale data...
Top 5 Cloud Trends U.K. Businesses Should Watch in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson As business data demands increase, cloud providers and their customers find themselves having to consider the implications of increasing storage...
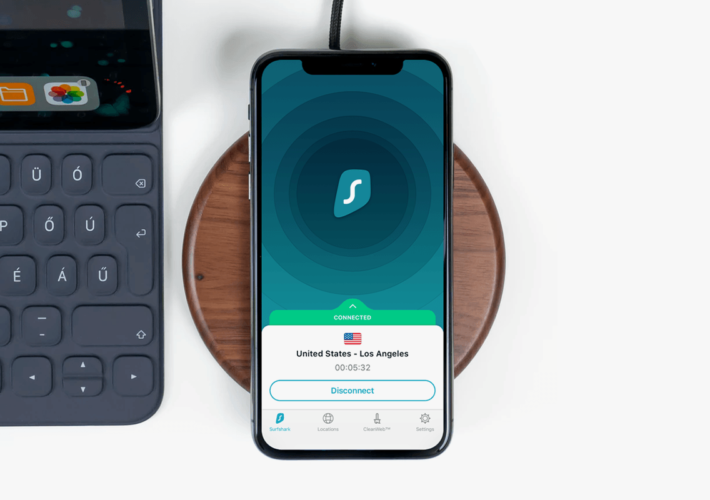
Get 3 Years of Rock-Solid Protection With Surfshark VPN for $67.20 by 5/31 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Surfshark VPN Fast facts Our rating: 4.6 stars out of 5 Pricing: Starts at $4.09 per month Key features: Servers...
Celoxis: Project Management Software Is Changing Due to Complexity and New Ways of Working – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Project management systems have become cornerstone tools for organisations in APAC to navigate the fast pace of business changes. Whether...
6 Best VPNs for Canada in 2024 (Free & Paid VPNs) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Kara Sherrer We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Trusted relationship attacks: trust, but verify – Source: securelist.com
Source: securelist.com – Author: Dmitry Kachan, Alina Sukhanova IT outsourcing market continues to demonstrate strong growth globally – such services are becoming increasingly popular. But along...
Can Cybersecurity Be a Unifying Factor in Digital Trade Negotiations? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alex Botting Alex Botting, Senior Director of Global Security and Technology Strategy, Venable & Coordinator of the Coalition to Reduce Cyber Risk...
OpenSSF Siren to Share Threat Intelligence for Open Source Software – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: MaximP via Shutterstock The Open Source Security Foundation (OpenSSF) has launched Siren, an email mailing...
Transforming CISOs Into Storytellers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Grant Gross, Contributing Writer Source: Panther Media GmbH via Alamy Stock Photo In an era when chief information security officers (CISOs) can...
NRECA Receives $4M in DOE Funding to Boost Electric Co-op Cybersecurity Preparedness – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE ARLINGTON, Va. – The National Rural Electric Cooperative Association has been awarded $4 million from the Department of Energy to launch...
Critical Bug Allows DoS, RCE, Data Leaks in All Major Cloud Platforms – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: George Ostertag via Alamy Stock Photo Researchers have discovered a severe memory corruption vulnerability inside of a...
Message board scams – Source: securelist.com
Source: securelist.com – Author: CFR team Marketplace fraud is nothing new. Cybercriminals swindle money out of buyers and sellers alike. Lately, we’ve seen a proliferation of...
Threat landscape for industrial automation systems, Q1 2024 – Source: securelist.com
Source: securelist.com – Author: Kaspersky ICS CERT Global statistics Statistics across all threats In the first quarter of 2024, the percentage of ICS computers on which...
70% of CISOs worry their org is at risk of a material cyber attack – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Chief information security officers around the globe “are nervously looking over the horizon,” according to a survey of 1,600 CISOs that...
Identity vulnerabilities a concern at Microsoft, outside researcher claims – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Top insights for IT pros From cybersecurity and big data to cloud computing, IT Brew covers the latest trends shaping business...
7 best practices for tackling dangerous emails – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Email is the #1 means of communication globally. It’s simple, affordable and easily available. However, email systems weren’t designed...
6 Facts About How Interpol Fights Cybercrime – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer Source: Olena Bartienieva via Alamy Stock Photo It takes a complex coordination of law enforcement, judicial processes, and...
Microsoft’s ‘Recall’ Feature Draws Criticism From Privacy Advocates – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Mojahid Mottakin via Shutterstock Microsoft’s plans to introduce a “Recall” feature powered by artificial intelligence in its...
AI Voice Generator App Used to Drop Gipy Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: OleCNX via Alamy Stock Photo Gipy, a newly discovered campaign using a strain of infostealer...
Google Discovers Fourth Zero-Day in Less Than a Month – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: dpa picture alliance via Alamy Stock Photo Google has released an update from its Chrome...
When ‘No’ & ‘Good Enough’ Challenge Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tyler Farrar 3 Min Read Source: Skorzewiak via Alamy Stock Photo COMMENTARY In the realm of cybersecurity, the path to securing necessary...
The SEC’s SolarWinds Case: What CISOs Should Do Now – Source: www.darkreading.com
Source: www.darkreading.com – Author: Scott H. Kimpel Source: Zhanna Hapanovich via Shutterstock COMMENTARY In October 2023, the Securities and Exchange Commission (SEC) dramatically altered the landscape...
Future-Proof Your Cybersecurity AI Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security 3 Min Read Source: Kittipong Jirasukhanont via Alamy Stock Photo With the constant onslaught of new attacks and emerging threats,...
CyberArk Goes All In on Machine Identity With Venafi Deal – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Mopic via Alamy Stock Photo Identity-based attacks aren’t just limited to breached credentials of people with rights...
Russia’s Turla APT Abuses MSBuild to Deliver TinyTurla Backdoor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Age Foto Stock via Alamy Stock Photo A Russia-linked advanced persistent threat (APT) group has been abusing...
Hacker defaces spyware app’s site, dumps database and source code – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A hacker has defaced the website of the pcTattletale spyware application, found on the booking systems of several Wyndham hotels...
Get 9 Courses on Ethical Hacking for Just $50 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published May 27, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
SentinelOne vs Palo Alto: Compare EDR software – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Devin Partida Perhaps you’re looking for an endpoint detection and response tool to enhance your cybersecurity efforts. SentinelOne and Palo Alto are...