Source: www.schneier.com – Author: Bruce Schneier Peter Gutmann and Stephan Neuhaus have a new paper—I think it’s new, even though it has a March 2025 date—that...
Year: 2025
How the Solid Protocol Restores Digital Agency – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The current state of digital identity is a mess. Your personal information is scattered across hundreds of locations: social media...
CVE-2025-8292: Use-After-Free Vulnerability in Google Chrome Leads to RCE and System Compromise – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk After Microsoft’s recent patch for two critical zero-day vulnerabilities in SharePoint (CVE-2025-53770, CVE-2025-53771), Google has followed with its own urgent...
SHARED INTEL Q&A: Inside the access mess no one sees — and the identity risk no one owns – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido For decades, identity and access management (IAM) and privileged access management (PAM) sat on the sidelines of...
3 Things CFOs Need to Know About Mitigating Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Raymond Daoud Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Russia’s Secret Blizzard APT Gains Embassy Access via ISPs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Getting a Cybersecurity Vibe Check on Vibe Coding – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
What the Coinbase Breach Says About Insider Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Verrion Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Dark Reading Confidential: Funding the CVE Program of the Future – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
Low-Code Tools in Microsoft Azure Allowed Unprivileged Access – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Tonic Security Harnesses AI to Combat Remediation Challenges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Palo Alto Networks Grabs IAM Provider CyberArk for $25B – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Inside the FBI’s Strategy for Prosecuting Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Ransomware up 179%, credential theft up 800%: 2025’s cyber onslaught intensifies – Source: www.csoonline.com
Source: www.csoonline.com – Author: A surge in infostealers, delayed vulnerability disclosures, and record ransomware attacks is overwhelming defenders, according to Flashpoint’s latest threat intelligence. In the...
Cyberkriminelle setzen Ingram Micro Ultimatum – Source: www.csoonline.com
Source: www.csoonline.com – Author: Zahlt der IT-Dienstleister bis 1. August kein Lösegeld, droht ein Mega-Leak. Ransomware-Gangster erpressen Ingram Micro. JHVEPhoto | shutterstock.com Anfang Juli 2025 wurde...
‘EDR-on-EDR Violence’: Hackers turn security tools against each other – Source: www.csoonline.com
Source: www.csoonline.com – Author: Researchers reveal how attackers exploit free trials of endpoint detection tools to disable existing security software, even with tamper protection enabled. Cybersecurity...
Mind the overconfidence gap: CISOs and staff don’t see eye to eye on security posture – Source: www.csoonline.com
Source: www.csoonline.com – Author: Security executives may be prone to believing cyber defenses are stronger than front-line staff see them to be, thereby distorting spending priorities...
GenAI als Security-Gamechanger? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Generative AI (GenAI) soll Daten und Infrastruktur vor ausgeklügelten Cyberbedrohungen schützen – soweit die Theorie. Doch wie sieht die Realität aus? Für...
Tangled in the web: Scattered Spider’s tactics changing to snare more victims – Source: www.csoonline.com
Source: www.csoonline.com – Author: The group has been impersonating employees to trick IT help desks into resetting passwords and transferring MFA tokens to attacker-controlled devices. Scattered...
Ransomware gang tells Ingram Micro, ‘Pay up by August 1’ – Source: www.csoonline.com
Source: www.csoonline.com – Author: Safepay gang says 3.5TB of stolen data will be released if Ingram doesn’t capitulate. The Safepay ransomware gang has given IT distributor...
Proofpoint Demonstrates Long-term Commitment to India with Local Data Centre and Strategic Regional Investments – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Indian public and private sector organisations can access Proofpoint’s leading email security and data protection solutions while meeting data residency requirements BANGALORE,...
Smashing Security podcast #428: Red flags, leaked chats, and a final farewell – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content The viral women-only dating safety app Tea, built to flag red flags, gets flagged itself – after...
Enterprise Kubernetes Management: What Is It & Do You Have It? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Adam Zahorscak Enterprise Kubernetes management is the cornerstone of modern cloud-native operations, enabling organizations to orchestrate, secure, and scale containerized workloads across...
Randall Munroe’s XKCD ‘Replication Crisis’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink The post Randall Munroe’s XKCD ‘Replication...
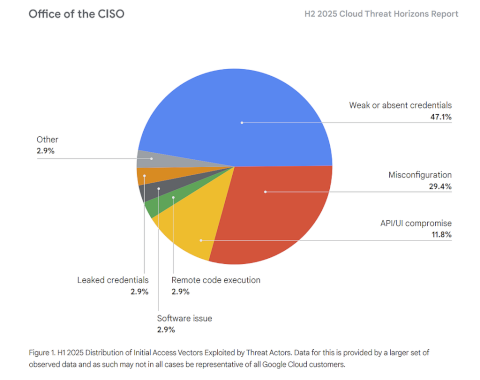
Google Cloud Security Threat Horizons Report #12 Is Out! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our next Threat...
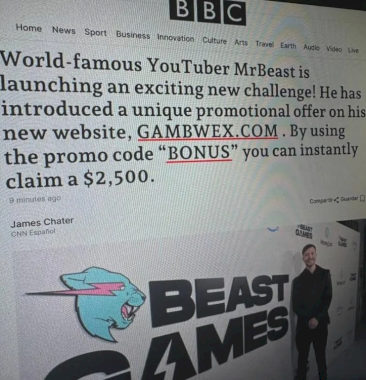
Scammers Unleash Flood of Slick Online Gaming Sites – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Fraudsters are flooding Discord and other social media platforms with ads for hundreds of polished online gaming and wagering websites that...
Senate Committee Advances Trump Nominee to Lead CISA – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A U.S. Senate committee voted Wednesday to advance President Donald Trump’s pick to lead the agency that secures the nation’s...
Cost of Data Breach in US Rises to $10.22 Million, Says Latest IBM Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend IBM’s Cost of a Breach Report shows that global costs are down, but US costs are up. More than anything...
Koreans Hacked, Blackmailed by 250+ Fake Mobile Apps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Silk Typhoon Linked to Powerful Offensive Tools, PRC-Backed Companies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...