Source: www.csoonline.com – Author: The cybercrime industry is largely organized around one motivation: to get the target person, company or organization to shell out a significant...
Month: August 2025
An Audit Isn’t a Speed Bump — It’s Your Cloud Co-Pilot – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ravi Sharma Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Proof-of-Concept in 15 Minutes? AI Turbocharges Exploitation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Apple Contends UK’s ‘EU-Style’ Antitrust Regulations Harm Users and Developers – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Image: misu/Adobe Stock Apple has warned the UK government against applying “EU-style rules” on technology companies. The iPhone maker argues...
58% of Organizations Are Unprepared for Cyberattacks – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Proofpoint has released its most recent Voice of the CISO report, surveying 1,600 CISOs across 16 countries to better understand their challenges, expectations...
Training Bank Employees on Cybersecurity – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Aug 26 2025 Security Annual cybersecurity training may help an organization stay compliant, but it doesn’t mean they’re more secure. Teta Alim...
AI website builder Lovable fuels rise in phishing & scams – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Cybercriminals are increasingly using the AI-driven website builder Lovable to rapidly create and host fraudulent sites for phishing, malware delivery, and financial...
CISOs grow more concerned about risk of material cyberattack – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: An article from A report by Proofpoint shows growing anxiety among security leaders about their companies’ cyber readiness. Published Aug. 26, 2025...
Illicit activity powered by Lovable website builder abuse on the rise – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Phishing, AI/ML More malicious websites, malware portals, and phishing pages have been created using the artificial intelligence-powered website creation and hosting platform...
Redmond High School SWENext Club Celebrates 2025 Coding Challenge Winners
Middle school students showcased their coding skills and creativity using the engaging “Mission Outer Space!” theme. Source Views: 2
SWENext Spotlight: Isabella T
Learn how starting up an international club in Brazil has been a transformative experience for Isabella. Source Views: 0
SWENext Spotlight: Haneyya S
Haneyya from Pakistan shares how to stay connected with SWE and build community, no matter your location. Source Views: 1
2025 SWE Awards Honor Outstanding Engineers and STEM Leaders
Celebrate the 2025 SWE awards recipients who are driving innovation and championing women in engineering! Source Views: 4
How attackers adapt to built-in macOS protection – Source: securelist.com
Source: securelist.com – Author: Alexander Chudnov If a system is popular with users, you can bet it’s just as popular with cybercriminals. Although Windows still dominates,...
Reduce Fraud Risk with Effective Identity Verification – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In a world where transactions occur smoothly across borders and platforms, the need for robust fraud and risk management strategies has become...
Innovator Spotlight: ManageEngine – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Unifying IT Management and Security with ManageEngine In today’s digital landscape, IT can feel like juggling flaming torches, one wrong move...
Affiliates Flock to ‘Soulless’ Scam Gambling Machine – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Last month, KrebsOnSecurity tracked the sudden emergence of hundreds of polished online gaming and wagering websites that lure people with free...
CISA, FBI, NSA Warn of Chinese ‘Global Espionage System’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Hackers Steal 4M+ TransUnion Customers’ Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
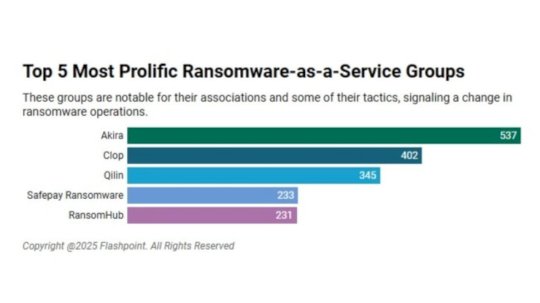
Akira, Cl0p Top List of 5 Most Active Ransomware-as-a-Service Groups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
1,000+ Devs Lose Their Secrets to an AI-Powered Stealer – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Dark Reading Confidential: A Guided Tour of Today’s Dark Web – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
CISA’s New SBOM Guidelines Get Mixed Reviews – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Gaps in California Privacy Law: Half of Data Brokers Ignore Requests – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Help Wanted: Dark Web Job Recruitment is Up – Source: securityboulevard.com
Source: securityboulevard.com – Author: Teri Robinson If you’re an industrious, persistent, English-speaking bad actor with a documented expertise in AI and a penchant for wreaking havoc...
Organized and Criminal, Ransomware Gangs Run Up Profits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Teri Robinson Move over, Michael Corleone and Tony Soprano, there’s a new godfather or two — or 200 — in town. Ransomware...
News alert: Halo Security’s custom dashboards give security teams control while streamlining workflows – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Miami, Aug. 28, 2025, CyberNewswire — Halo Security, a leading provider of external risk management solutions, today announced significant platform enhancements...
Inside the Salesloft Breach: A New Era of Salesforce Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog The spotlight has finally swung toward the integration layer, and what’s emerging should worry every SaaS security leader. Another...
BSidesSF 2025: Trust Engineering: Building Security Leadership At Early-Stage Startups – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Creator, Author and Presenter: Mike Privette Our deep appreciation to Security BSides – San Francisco and the Creators, Authors and...
El 60 % fracasa. ¿También usted? – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireMon Qué revela FireMon Insights sobre los riesgos de las políticas de firewall y cómo evitarlos La gestión del firewall es el...