Source: www.techrepublic.com – Author: J.R. Johnivan OneFlip could cause self-driving cars to crash, facial recognition systems to fail, and biometric ID authenticators to shut down. A...
Day: August 27, 2025
We Are Still Unable to Secure LLMs from Malicious Inputs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Nice indirect prompt injection attack: Bargury’s attack starts with a poisoned document, which is shared to a potential victim’s Google...
News alert: Global security leaders to convene at OpenSSL 2025 — final week for early-bird rates – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Newark, N.J., Aug. 25, 2025, CyberNewwire — Only 7 days left to secure the Early Bird registration at the OpenSSL Conference...
UNC6384 Attack Detection: China-Linked Group Targets Diplomats and Hijacks Web Traffic Spreading a PlugX Variant – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The China-backed hacking collective tracked as UNC6384 has been observed behind cyber-espionage attacks against diplomats in Southeast Asia and various...
Storm-0501 Hits Enterprise With ‘Cloud-Based Ransomware’ Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
AI-Powered Ransomware Has Arrived With ‘PromptLock’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
African Law Enforcement Agencies Nab Cybercrime Syndicates – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
When One Hospital Gets Ransomware, Others Feel the Pain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Philippines Power Election Security With Zero-Knowledge Proofs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Mercedes Cardona Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
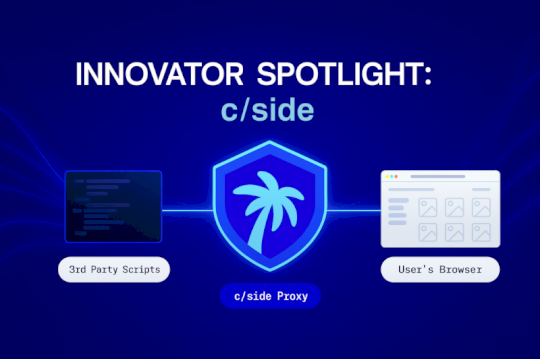
Innovator Spotlight: CSide – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary August 27, 2025 Securing the Browser’s Blind Spot By Victoria Hargrove, CDM Reporter What CSide Does Most security stacks fortify servers,...
Cross-domain Solutions: The Present and Future of a Growing Industry – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cross-domain solutions (CDS) consist of the secure exchange of information between security domains. This type of solution, which emerged as...
CMMC 2.0 Final Rule Released – Get Prepared Now! – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In a significant step to secure the defense industrial base (DIB), the Department of Defense (DoD) has officially released the...
How Engineer Kathleen Grover Returned to Work After an Eight-Year Career Break
Kathleen Grover shares what it was like to interview, secure a role, and transition back to the STEM workforce. Plus, learn about SWE’s reentry resources for...
Hands-On Technical Workshops Return to 2026 North American WE Locals
Have you heard the news? The wildly popular hands-on technical workshop sessions are returning to a WE Local conference near you! Have an idea for a...
Exploits and vulnerabilities in Q2 2025 – Source: securelist.com
Source: securelist.com – Author: Alexander Kolesnikov Vulnerability registrations in Q2 2025 proved to be quite dynamic. Vulnerabilities that were published impact the security of nearly every...
The AI Fix #65: Excel Copilot will wreck your data, and can AI fix social media? – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley In episode 65 of The AI Fix, a pigeon gives a PowerPoint presentation, Mark plays Graham a song about the...
Alleged mastermind behind K-Pop celebrity stock heist extradited to South Korea – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley South Korean authorities have announced the extradition from Thailand and arrest of a suspected hacker, believed to be the mastermind...
Yemen Cyber Army hacker jailed after stealing millions of people’s data – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley A 26-year-old hacker, who breached websites in North America, Yemen, and Israel, and stole the details of millions of people...
Only 49% of companies to increase cyber budget after a breach – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis Aug 27, 20255 mins CyberattacksData BreachIncident Response Increasing security spending after a cyber incident is falling out of fashion, as...
5 ways to improve cybersecurity function while spending less – Source: www.csoonline.com
Source: www.csoonline.com – Author: Government cutbacks, defunding of critical public resources, tariffs, and market uncertainty are impacting cybersecurity budgets. Here’s how you can do more with...
LLMs easily exploited using run-on sentences, bad grammar, image scaling – Source: www.csoonline.com
Source: www.csoonline.com – Author: Researchers continue to find vulnerabilities that dupe models into revealing sensitive information, indicating that security measures are still being bolted onto AI....
Attackers steal data from Salesforce instances via compromised AI live chat tool – Source: www.csoonline.com
Source: www.csoonline.com – Author: One of their goals was to access other credentials to compromise other environments. A threat actor managed to obtain Salesforce OAuth tokens...
Critical Docker Desktop flaw allows container escape – Source: www.csoonline.com
Source: www.csoonline.com – Author: Missing authentication on the Docker Engine management API for Docker Desktop on Windows and Mac allows attackers to break out from containers...
Big-Tech-Zulieferer meldet Ransomware-Attacke – Source: www.csoonline.com
Source: www.csoonline.com – Author: Mit Data I/O ist ein Zulieferer von Apple, Amazon, Microsoft und Google von einer Ransomware-Attacke betroffen, die erhebliche Störungen verursacht. Der Anbieter...
Rache am Arbeitgeber bringt Entwickler vier Jahre in den Knast – Source: www.csoonline.com
Source: www.csoonline.com – Author: Aus Wut über seine Degradierung hat ein Entwickler heimlich die Systeme seines Arbeitgebers sabotiert. Welche Konsequenzen es haben kann, wenn technisch versierte...
NIS2 und der Mittelstand: Zwischen Pflicht und Praxis – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die NIS2-Richtlinie verpflichtet eine Vielzahl an Unternehmen zur Cybersicherheit und digitalen Resilienz. Doch vor allem mittelständische Unternehmen tun sich mit der Umsetzung...
Proofpoint’s 2025 Voice of the CISO Report Reveals Heightened AI Risk, Record CISO Burnout, and the Persistent People Problem in Cybersecurity – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 76% of CISOs anticipate a material cyberattack in the next year, with human risk and GenAI-driven data loss topping their concerns SUNNYVALE,...
Broadcom Extends Reach and Scope of Cybersecurity Portfolio – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Broadcom today added a slew of cybersecurity updates, including a technology preview of an update to VMware vDefend that secures...
Microsoft’s New AI Risk Assessment Framework – A Step Forward – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist Microsoft recently introduced a new framework designed to assess the security of AI models. It’s always encouraging to see...
CVE-2025-7775: Citrix NetScaler ADC and NetScaler Gateway Zero-Day Remote Code Execution Vulnerability Exploited in the Wild – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Caveza Citrix has released patches to address a zero-day remote code execution vulnerability in NetScaler ADC and NetScaler Gateway that has...