Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: DD Images via Shutterstock North Korea’s Lazarus threat group has launched a fresh wave of attacks targeting...
Month: January 2025
OWASP’s New LLM Top 10 Shows Emerging AI Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Matias Madou Matias Madou, Co-Founder & CTO, Secure Code Warrior January 15, 2025 5 Min Read Source: Nils Ackermann via Alamy Stock...
1Password’s Trelica Buy Part of Broader Shadow IT Play – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz 1Password’s acquisition of software-as-a-service (SaaS) access management provider Trelica is the latest move in a race to broaden the scope...
7 Essential Security Operations Center Tools for 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Equipping your security operations center (SOC) team with the right tools is essential to their success. Without the right tools,...
News alert: Aembit announces speakers for NHIcon event, highlighting non-human identity security – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Silver Spring, MD, Jan. 15, 2025, CyberNewswire — Aembit, the non-human identity and access management (IAM) company, unveiled the full agenda...
News alert: Sweet Security’s LLM-powered detection engine reduces cloud noise to 0.04% – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Tel Aviv, Israel, Jan. 15, 2025, CyberNewswire — Sweet Security, a leader in cloud runtime detection and response, today announced the...
News alert: Wultra secures €3M funding to help financial firms mitigate coming quantum threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Prague, Czech Republic, Jan. 15, 2025, CyberNewswire — Quantum computing is set to revolutionize technology, but it also presents a significant...
DEF CON 32 – Small Satellite Modeling and Defender Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, January 15, 2025 Home » Security Bloggers Network » DEF CON 32 – Small Satellite Modeling and Defender Software...
FBI Deletes PlugX Malware From Computers Infected by China Group – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The FBI, with the help of French law enforcement and a private cybersecurity company, deleted a version of the PlugX...
Protecting the software supply chain: Insights from our expert panel – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens As software grows increasingly complex, ensuring the security of your software supply chain remains a critical priority. *** This is...
Randall Munroe’s XKCD ‘Chess Zoo’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Allstate Violates Drivers’ Privacy, Texas AG Alleges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings “We will hold all these companies accountable,” rants state attorney general Ken Paxton (pictured). Texas fires the next shot in lawmakers’ war...
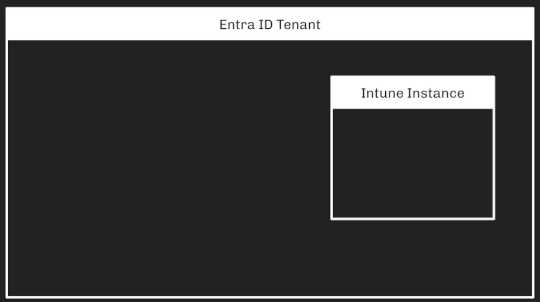
Intune Attack Paths — Part 1 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Intune Attack Paths — Part 1 Prior Work Several people have recently produced high-quality work around Intune tradecraft. I want to specifically mention:...
The AI Fix #33: AI’s deliberate deceptions, and Elon’s “unhinged” mode – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 33 of The AI Fix, our hosts watch a robot fall over, ChatGPT demonstrates that...
Phishing False Alarm – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Menu Blog Newsletter Books Essays News Talks Academic About Me HomeBlog Phishing False Alarm A very security-conscious company was hit...
Microsoft: Happy 2025. Here’s 161 Security Updates – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Microsoft today unleashed updates to plug a whopping 161 security vulnerabilities in Windows and related software, including three “zero-day” weaknesses that...
Die Top 10 Geschäftsrisiken in Deutschland 2025 – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Welt ist unruhig geworden. Dementsprechend wachsen auch in den Unternehmen die Sorgen vor drohenden Risiken aller Art. Cyberangriffe zählen nach wie...
Perfide Ransomware-Attacke gegen AWS-Nutzer – Source: www.csoonline.com
Source: www.csoonline.com – Author: Security-Forscher warnen vor einem Ransomware-Angriff, der auf AWS-Kunden abzielt. Bei Erfolg droht dauerhafter Datenverlust. Hacker haben kompromittierte AWS-Zugangsdaten genutzt, um S3-Buckets zu...
Cisco’s homegrown AI to help enterprises navigate AI adoption – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cisco AI Defense is the company’s proprietary AI tool that can validate enterprise AI models and protect them against attacks. As the...
CISA unveils ‘Secure by Demand’ guidelines to bolster OT security – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISA and global cybersecurity leaders have introduced a proactive framework for OT procurement, emphasizing security by design to counter evolving threats. The...
The CFO may be the CISO’s most important business ally – Source: www.csoonline.com
Source: www.csoonline.com – Author: Opinion 15 Jan 20256 mins BudgetBusiness IT AlignmentCSO and CISO Despite natural tensions, a CISO-CFO alliance can help CISOs become better business...
Stop wasting money on ineffective threat intelligence: 5 mistakes to avoid – Source: www.csoonline.com
Source: www.csoonline.com – Author: To prevent overspending in the wrong areas of cybersecurity and support ROI, here are five mistakes CISOs should avoid. Strong capabilities in...
International effort erases PlugX malware from thousands of Windows computers – Source: www.csoonline.com
Source: www.csoonline.com – Author: Solution from French authorities took advantage of self-delete command; US got a court order to use it. The US has again taken...
Fortinet confirms zero-day flaw used in attacks against its firewalls – Source: www.csoonline.com
Source: www.csoonline.com – Author: The advisory from the cybersecurity company follows a report from security researchers who observed exploits in the wild in early December as...
The Advent of Quantum Cryptography and Zero Trust: A New Era In The World Of Cybersecurity – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Short description The advancement of cybersecurity is propelled by adapting to new technologies and rising threats. From quantum cryptography to...
RSA Conference: 20th annual RSAC Innovation Sandbox and fifth annual Launch Pad contests are now open. – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary San Francisco, CA – January 14, 2025 – RSA Conference™, the world’s leading information security conferences and expositions, today announced that submissions for...
Exposure Management: A Strategic Approach to Cyber Security Resource Constraint – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Imagine being bombarded by a relentless barrage of alarms, each one clamouring for immediate attention. This is the daily reality...
Publisher’s Spotlight: Merlin Group – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Bridging the Gap Between Cyber Innovation and Regulated Markets Addressing the Challenge of Innovation Access in Regulated Markets In an era...
Proofpoint Named a Leader in 2025 Gartner® Magic Quadrant™ for Digital Communications Governance and Archiving Solutions – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Proofpoint evaluation as a Leader based on Completeness of Vision and Ability to Execute SUNNYVALE, Calif., January 9, 2025 – Proofpoint, Inc., a...
As Tensions Mount With China, Taiwan Sees Surge in Cyberattacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Andy.LIU via Shutterstock Using phishing emails and zero-day exploits, China’s cyber-operations groups targeted Taiwanese organizations — including...