Source: www.infosecurity-magazine.com – Author: The FBI has warned that North Korean IT worker schemes are stealing data to extort their victims as part of efforts to...
Month: January 2025
Ransomware Gangs Linked by Shared Code and Ransom Notes – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Two recently identified ransomware gangs are using payloads that contain almost identical code, suggesting that the groups’ affiliates are using shared infrastructure....
Chained Vulnerabilities Exploited in Ivanti Cloud Service Appliances – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Threat actors have been actively exploiting chained vulnerabilities in Ivanti Cloud Service Appliances (CSA), significantly amplifying the impact of their cyber-attacks. The...
Bookmakers Ramp Up Efforts to Combat Arbitrage Betting Fraud – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A growing wave of arbitrage betting fraud, driven by automation and advanced money laundering techniques, has been forcing bookmakers to adopt stricter...
The Power of Many: Crowdsourcing as A Game-Changer for Modern Cyber Defense – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team With the rapid technological advancement and the world entering the AI era, the cyber threat landscape has significantly evolved in...
Operational Security: The Backbone of Effective Police Communication – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the fast-paced and dynamic world of law enforcement, effective communication is essential for ensuring public safety and successful operations....
A K-12 Guide to the Digital Classroom – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexa Sander Digital tools have transformed how teachers and students engage in classroom activities, creating opportunities to enhance learning, communication, and organization....
Understanding the 3-Layers of Non-Human Identity (NHI) Security in TrustFour’s Posture and Attack Surface Management Framework – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jim Curtin In today’s interconnected digital ecosystems, securing Non-Human Identities (NHIs) has become a critical focus. NHIs—representing machines, applications, containers, and microservices—outnumber...
Safe Secrets Rotation: A Must for Modern Clouds – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Secrets Rotation Crucial for Cloud Security? Are you familiar with the concept of secrets rotation? Does it sound...
Boosting Confidence in Cloud-Native Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Confident in Your Cloud-Native Security? Navigating cybersecurity can be like walking through a maze filled with lurking threats....
Unlocking Innovation with Protected Machine Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your Organization Paying Enough Attention to Non-Human Identities? Organizations extensively utilize cloud services and automated systems. In doing so,...
How to Stop Layer 7 DDoS Attacks in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andrew Hendry Imagine your website humming with activity, traffic soaring, and your brand capturing the attention it deserves. But what if that...
6 Ways IT Can Help You Modernize Case Management Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Manish Mehta Article Your IT department can be a valuable ally in overcoming inevitable resistance to change Related Resources Modern and effective...
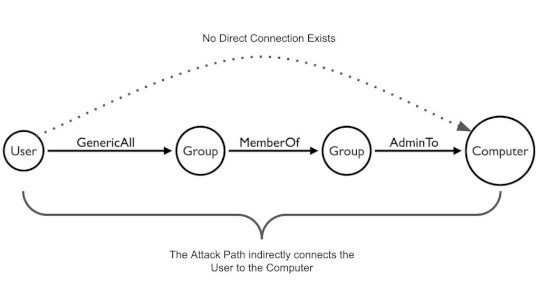
Insurance companies can reduce risk with Attack Path Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kirsten Gibson TL;DR Insurance companies host large amounts of sensitive data (PII, PHI, etc.) and often have complex environments due to M&A...
DEF CON 32 – The Wild And Wonderful World Of Early Microprocessors With A Focus On 6502 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, January 23, 2025 Home » Security Bloggers Network » DEF CON 32 – The Wild And Wonderful World Of...
SOC vs MSSP: Which is Right for Your Business? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rebecca Kappel One of the most pivotal decisions an organization faces is whether to build an in-house Security Operations Center (SOC) or...
Proofpoint and Ingram Micro Team to Radically Simplify and Accelerate Sales Cycles for Partners – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Channel partners benefit from an unparalleled agile procurement process to strengthen their business opportunities and close deals faster SUNNYVALE, Calif., January 23,...
Automating endpoint management doesn’t mean ceding control – Source: www.csoonline.com
Source: www.csoonline.com – Author: AEM can help solve persistent skills gaps, tool sprawl, and budget constraints. Beset with cybersecurity risks, compliance regimes, and digital experience challenges,...
Grohe AG mutmaßlich von Ransomware-Attacke betroffen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Cyber-Bande Ransomhub erpresst die Grohe AG mit gestohlenen Daten. Die Ransomware-Bande Ransomhub will 100 Gigabyte Daten von der Grohe AG erbeutet...
Cisco patches antivirus decommissioning bug as exploit code surfaces – Source: www.csoonline.com
Source: www.csoonline.com – Author: The flaw could allow remote attackers to shut down ClamAV scanning and compromise critical security workflows. Cisco has patched a denial-of-service (DoS)...
10 top XDR tools and how to evaluate them – Source: www.csoonline.com
Source: www.csoonline.com – Author: Extended detection and response tools provide a deeper and more automated means to identify and respond to threats. These are some of...
Python administrator moves to improve software security – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 23 Jan 20255 mins The popular programming language has added a way to check for malware-laded packages. The administrators of...
Geben Sie LLM-Alarmismus keine Chance! – Source: www.csoonline.com
Source: www.csoonline.com – Author: Generative KI wird Cyberkriminellen keinen Vorteil verschaffen – im Gegenteil. Die Mär von der Cybercrime-KI-Revolution? Overearth | shutterstock.com Cybersicherheitsexperten haben in den...
Auswirkungen auf IT-Fachkräfte: 10 Anzeichen für einen schlechten CSO – Source: www.csoonline.com
Source: www.csoonline.com – Author: Sind Mitarbeiter motiviert und werden gefördert, arbeiten sie effektiver, auch in der IT-Security. Schlechte Stimmung kann an den Vorgesetzten liegen. Sind IT-Mitarbeiter...
Mastercard’s multi-year DNS cut-and-paste nightmare – Source: www.csoonline.com
Source: www.csoonline.com – Author: What is frightening about this mistake is not how much damage cyberthieves could have done, but how easy it is to make...
Third Interdisciplinary Workshop on Reimagining Democracy (IWORD 2024) – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Last month, Henry Farrell and I convened the Third Interdisciplinary Workshop on Reimagining Democracy (IWORD 2024) at Johns Hopkins University’s...
CISA: Ivanti Vulns Chained Together in Cyberattack Onslaught – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Kristoffer Tripplaar via Alamy Stock Photo NEWS BRIEF Cyberattackers are using a new threat vector...
The Security Risk of Rampant Shadow AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Anuj Jaiswal Anuj Jaiswal, Chief Product Officer, Fortanix January 23, 2025 3 Min Read Source: LuckyStep48 via Alamy Stock Vector COMMENTARY The...
Black ‘Magic’ Targets Enterprise Juniper Routers With Backdoor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: LJSphotography via Alamy Stock Photo Dozens of organizations have been infected with router malware that uses a...
Doti AI Launches Platform to Securely Find Enterprise Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: YAY Media AS via Alamy Stock Photo NEWS BRIEF All organizations, regardless of size or industry, are experiencing...