Source: www.securityweek.com – Author: Associated Press Cybercriminals who hacked Rhode Island’s system for health and benefits programs have released files to a site on the dark...
Day: December 31, 2024
Cyberhaven Chrome Extension Hack Linked to Widening Supply Chain Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The supply chain attack in which cybersecurity firm Cyberhaven’s Chrome extension was compromised to steal users’ data appears to be...
Chinese Hackers Accessed US Treasury Workstations in ‘Major’ Cybersecurity Incident – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Chinese hackers remotely accessed US Treasury Department workstations and unclassified documents after compromising a cloud-based service operated by BeyondTrust, the...
Sumit Dhawan: Proofpoint’s Road Map for Unified Data Security – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: AI-Driven Cloud Security Services , Data Loss Prevention (DLP) , Endpoint Security Proofpoint CEO Dhawan Discusses DSPM, AI and Human-Centric Cybersecurity Solutions...
US Treasury Department workstations breached in attack attributed to China – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 31 Dec 20243 mins CyberattacksData BreachGovernment A key used by third party service provider BeyondTrust to secure cloud-based remote support was...
Top 12 ways hackers broke into your systems in 2024 – Source: www.csoonline.com
Source: www.csoonline.com – Author: Attackers came armed with a mix of creative and effective tactics, using whatever worked to punch through systems with precision. In 2024,...
The CSO guide to top security conferences – Source: www.csoonline.com
Source: www.csoonline.com – Author: Tracking postponements, cancellations, and conferences gone virtual — CSO Online’s calendar of upcoming security conferences makes it easy to find the events...
Vielen CISOs droht der Burnout – Source: www.csoonline.com
Source: www.csoonline.com – Author: Editor in Chief B2B COMPUTERWOCHE, CIO, CSO in Germany News 30 Dezember 20244 Minuten Wenn das Stresslevel über Gebühr steigt, leiden nicht...
U.S. Army Soldier Arrested in AT&T, Verizon Extortions – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Federal authorities have arrested and indicted a 20-year-old U.S. Army soldier on suspicion of being Kiberphant0m, a cybercriminal who has been...
Social Media Hackers: How They Operate and How to Protect Yourself – Source:davinciforensics.co.za
Source: davinciforensics.co.za – Author: cyberpro. The Rising Threat of Social Media Hackers Social media platforms are an integral part of daily life, but they are also...
Chinese State Hackers Breach US Treasury Department – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: trekandshoot via Alamy Stock Photo UPDATE: This story was updated on Dec. 30 to include...
Salt Typhoon’s Reach Continues to Grow – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier lurker • December 30, 2024 12:40 PM Neuberger said the episode highlighted the need for required cybersecurity practices in the...
Best of 2024: 30,000 Dealerships Down — ‘Ransomware’ Outage Outrage no. 2 at CDK Global – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Car and truck dealers fall back on pen and paper as huge SaaS provider gets hacked (again). CDK Global, by far...
DEF CON 32 – Warflying in a Cessna – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, December 30, 2024 Home » Security Bloggers Network » DEF CON 32 – Warflying in a Cessna Authors/Presenters: Matt...
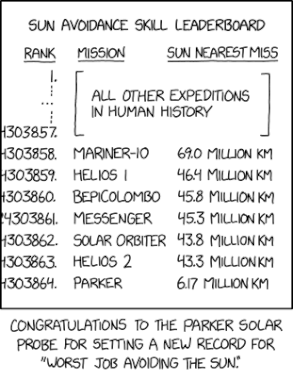
Randall Munroe’s XKCD ‘Sun Avoidance’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
VW Cars Leak Private Data of 800,000 — ‘Volksdaten’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Cariad, VW Group’s software arm, made this classic error. Personal data from hundreds of thousands of cars sat unsecured for about...
EF CON 32 – Winning the Game of Active Directory – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, December 31, 2024 Home » Security Bloggers Network » EF CON 32 – Winning the Game of Active Directory...
SquareX Researchers Expose OAuth Attack on Chrome Extensions Days Before Major Breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Palo Alto, Calif., USA, December 30th, 2024, CyberNewsWire SquareX, an industry-first Browser Detection and Response (BDR) solution, leads the way in...
Best of 2024: Microsoft Account Security Alert Email: Recognize the Scam – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra Reading Time: 5 min Are you worried about the legitimacy of the email alert you received from Microsoft? Your concern...
Reflecting on 2024 at Balbix + Looking Ahead to 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Courtney Goodman 2024 has been a transformative year for Balbix. By pushing boundaries in AI and teaming up with industry leaders like...
Navigating the SEC’s Cybersecurity Disclosure Rules: One Year On – Source: securityboulevard.com
Source: securityboulevard.com – Author: Steve Vintz In December 2023, as cyberattacks surged, the U.S. Securities and Exchange Commission (SEC)began enforcing new cybersecurity disclosure rules. This pushed...
Cybersecurity Resolutions for 2025: Prepare Your Business for What’s Ahead – Source: securityboulevard.com
Source: securityboulevard.com – Author: service Cybersecurity Resolutions for 2025: Prepare Your Business for What’s Ahead Cybersecurity Resolutions for 2025: Prepare Your Business for What’s Ahead As...