Source: www.darkreading.com – Author: PRESS RELEASE Dazz, the leader in security remediation, today announced new capabilities in the Dazz Unified Remediation Platform, including automated code-fixes for...
Month: May 2024
Palo Alto Networks Delivers Comprehensive SASE Capabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SANTA CLARA, Calif., May 2, 2024 /PRNewswire/ — Palo Alto Networks (NASDAQ: PANW), the global cybersecurity leader, announced its latest innovations to future-proof and...
Permira to Acquire Majority Position in BioCatch at $1.3B Valuation – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE New York and Tel Aviv, May 2, 2024 – BioCatch (the “Company”), the global leader in digital fraud detection and financial crime prevention...
Paris Olympics Cybersecurity at Risk via Attack Surface Gaps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Svet foto via Shutterstock Web applications and other Internet-facing assets related to the 2024 Summer Olympics in...
GAO: NASA Faces ‘Inconsistent’ Cybersecurity Across Spacecraft – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: dotted zebra via Alamy Stock Photo NASA has gone some way to addressing its cybersecurity challenges, according...
REvil Affiliate Off to Jail for Multimillion-Dollar Ransomware Scheme – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Ozrimoz via Shutterstock Ukrainian national Yaroslav Vasinskyi, affiliate of the REvil ransomware-as-a-service group, was sentenced...
Critical GitLab Bug Under Exploit Enables Account Takeover, CISA Warns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: simon de glanville via Alamy Stock Photo A critical security vulnerability in GitLab is under active attack,...
Innovation, Not Regulation, Will Protect Corporations From Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Marcotte 4 Min Read Source: Tenebroso via Alamy Stock Photo COMMENTARY In a recent open letter, high-profile names from across the...
New AI Security Startup Apex Secures AI Models, Apps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Ole CNX via Shutterstock The past two years have seen unprecedented interest in generative artificial...
North Korean Hackers Spoofing Journalist Emails to Spy on Policy Experts – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 North Korean threat actors are exploiting weak email policies to spoof legitimate domains during espionage phishing campaigns, a new US government...
Indonesia is a Spyware Haven, Amnesty International Finds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Indonesia has become a hub for spyware and surveillance tools that threaten citizens’ rights and privacy, Amnesty International has found. Building...
U.K., U.S. and Canadian Cyber Authorities Warn of Pro-Russia Hacktivist Attacks on Operational Technology Systems – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson The U.K.’s National Cyber Security Centre (NCSC) and other international cyber authorities, including the Federal Bureau of Investigation (FBI), have...
How Are APAC Tech Salaries Faring in 2024? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Working for a salary in tech has been somewhat of a wild ride in APAC in recent years. First, there...
My TED Talks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Rare Interviews with Enigma Cryptanalyst Marian Rejewski – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • May 3, 2024 8:00 AM @ ALL, Like many cryptographers that come eventually to public...
Streamline NIS2 Compliance with Automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Blackwell It’s no secret that NIS2 is around the corner, and that this directive is full of stringent rules, regulations and...
A Closer Look at Top 5 Vulnerabilities of April 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shubham Jha Keeping pace with the latest cybersecurity threats is vital for organizations of all sizes. Here at Strobes, our security team...
Insider Risk Digest: April – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lucas Seewald Dive into our latest Insider Risk Digest, where we unravel recent cases of espionage, insider betrayal, and security breaches across...
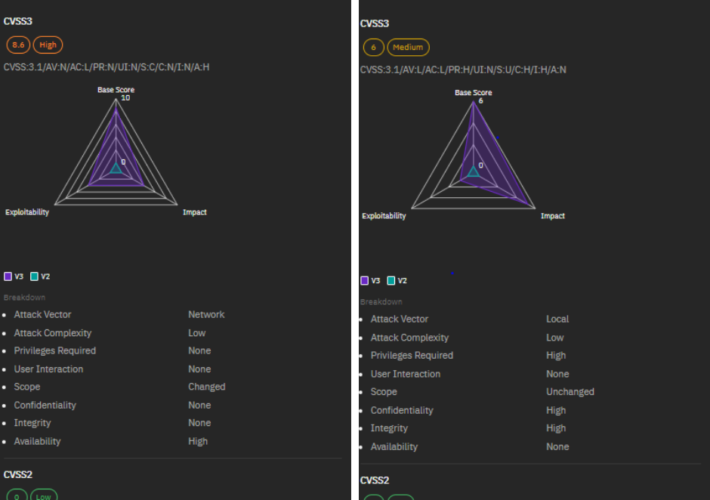
CVE-2024-27322 Should Never Have Been Assigned And R Data Files Are Still Super Risky Even In R 4.4.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr I had not planned to blog this (this is an incredibly time-crunched week for me) but CERT/CC and CISA made a...
The Persistent Threat of Path Traversal Vulnerabilities in Software Development – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nik Hewitt Path traversal vulnerabilities, or directory traversal, are now subject to a government advisory for obligatory consideration We live in an...
What is Proxmox VE – and Why You Should Live Patch It – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina Proxmox VE, like any software, is vulnerable to security threats. Patching helps address these vulnerabilities, protecting your virtual machines from...
GUEST ESSAY: A primer on how, why ‘dynamic baselining’ fosters accurate DDoS protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Ahmed Abdelhalim Businesses today need protection from increasingly frequent and sophisticated DDoS attacks. Service providers, data center operators, and enterprises...
FIN7 Cybercrime Group Strikes US Auto Sector Using Carbanak – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja Recent reports have highlighted that the notorious FIN7 cybercrime group has targeted the U.S. automotive industry through a sophisticated spear-phishing...
RSAC 2024 Innovation Sandbox | Aembit: An IAM Platform for Cloud Workloads – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has...
Proofpoint Announces Availability of its Human-Centric Security Solutions in AWS Marketplace – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 AWS customers worldwide can now deploy Proofpoint’s full stack of people and information protection that defend organizations’ human layer SUNNYVALE, Calif.,...
Billions of Android Devices Open to ‘Dirty Stream’ Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: rafapress via Shutterstock Researchers from Microsoft recently discovered many Android applications — including at least four with...
DPRK’s Kimsuky APT Abuses Weak DMARC Policies, Feds Warn – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Panther Media GmbH via Alamy Stock Photo North Korean hackers are taking advantage of weak DMARC configurations...
Software Security: Too Little Vendor Accountability, Experts Say – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Nick Lylak via Alamy Stock Photo While legal legwork is already in progress to hold...
Hacker Sentenced After Years of Extorting Psychotherapy Patients – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Taina Sohlman via Alamy Stock Photo Aleksanteri Kivimäki, a Finnish national, has been sentenced to...
Dropbox Breach Exposes Customer Credentials, Authentication Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Lina Images via Shutterstock Online storage service Dropbox is warning customers of a data breach by a...