Source: www.schneier.com – Author: Bruce Schneier Microsoft is trying to create a personal digital assistant: At a Build conference event on Monday, Microsoft revealed a new...
Day: May 23, 2024
How the Internet of Things (IoT) became a dark web target – and what to do about it – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Antoinette Hodes, Office of the CTO, Check Point Software Technologies. The dark web has evolved into a clandestine marketplace where...
RSAC Fireside Chat: Qwiet AI leverages graph-database technology to reduce AppSec noise – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido AppSec has never been more challenging. By the same token, AppSec technology is advancing apace to help...
ShrinkLocker: Turning BitLocker into ransomware – Source: securelist.com
Source: securelist.com – Author: Cristian Souza, Eduardo Ovalle, Ashley Muñoz, Christopher Zachor Introduction Attackers always find creative ways to bypass defensive features and accomplish their goals....
Cybercriminals Exploit Cloud Storage For SMS Phishing Scams – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have revealed a series of criminal campaigns that exploit cloud storage services such as Amazon S3, Google Cloud Storage,...
Indian Election Faces Cyber-Attacks, Data Leaks on Dark Web – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have reported a significant increase in cyber activity targeting the upcoming Indian general election. This surge, driven by various...
10 years in prison for $4.5 million BEC scammer who bought Ferrari to launder money – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley A scammer has been sentenced to 10 years in prison for laundering over US $4.5 million obtained by targeting businesses...
Smashing Security podcast #373: iPhone undeleted photos, and stealing Scarlett Johansson’s voice – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley iPhone photos come back from the dead! Scarlett Johansson sounds upset about GPT-4o, and there’s a cockup involving celebrity fakes....
Critical Flaw in Replicate AI Platform Exposes Proprietary Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Ole CNX via Shutterstock A critical vulnerability in the Replicate AI platform could have allowed attackers to...
New Mindset Needed for Large Language Models – Source: www.darkreading.com
Source: www.darkreading.com – Author: Vaibhav Malik Vaibhav Malik, Partner Solutions Architect, Cloudflare May 23, 2024 5 Min Read Source: Bakhtiar Zein via Alamy Stock Vector COMMENTARY...
China APT Stole Geopolitical Secrets From Middle East, Africa & Asia – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Rokas Tenys via Alamy Stock Photo A Chinese state-aligned threat group has been exfiltrating emails and files...
Iran APTs Tag Team Espionage, Wiper Attacks Against Israel & Albania – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: ASP Religion via Alamy Stock Photo Iranian state-backed threat actors have been working closely to spy on,...
YouTube Becomes Latest Battlefront for Phishing, Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: Andrea Danti via Alamy Stock Photo YouTube has turned into a new front for malicious...
EPA Puts Teeth Into Water Sector Cyber Efforts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Shahid Mehmood via Alamy Stock Photo Nearly 70% of the United States’ community drinking...
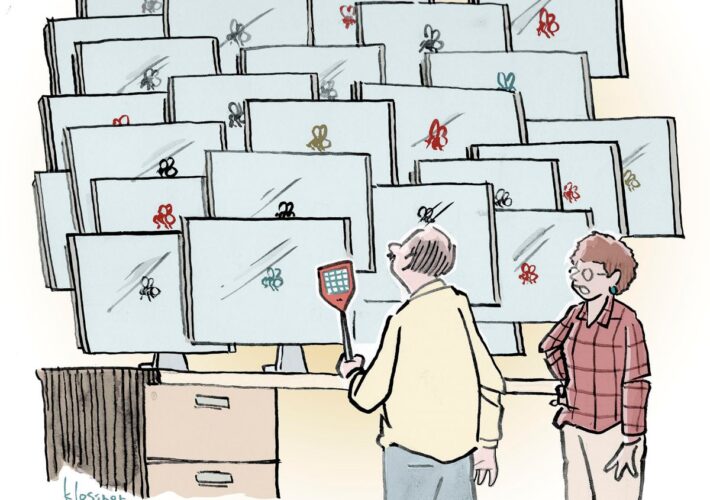
Name That Toon: Buzz Kill – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist 1 Min Read We’re gonna need a bigger … fly swatter? Come up with a clever cybersecurity-related caption to...
Picking the Right Database Tech for Cybersecurity Defense – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Eakrin Rasadonyindee via Shutterstock Modern cybersecurity technologies produce massive quantities of data, which requires rethinking how to...
Outsourcing Security Without Increasing Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: George V. Hulme, Contributing Writer 2 Min Read The growing number of cybersecurity incidents and wave of data privacy laws and regulations...
Beyond the Basics: Exploring Uncommon NTLM Relay Attack Techniques – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Murphy May 23, 2024 NTLM (NT LAN Manager) relaying is an attack technique that has been around for years yet is...
Hospitals Hacked: Urgent Care Needed – Source: securityboulevard.com
Source: securityboulevard.com – Author: Veriti Research In recent research by Veriti, a significant cyber security breach at Change Healthcare highlighted severe vulnerabilities in healthcare data security,...
RSAC Fireside Chat: Qwiet AI leverages graph-database technology to reduce AppSec noise – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido AppSec has never been more challenging. By the same token, AppSec technology is advancing apace to help...
BTS #30 – Systems Of Trust – Robert Martin – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Bob Martin comes on the show to discuss systems of trust, supply chain security and more! Show Notes Watch Subscribe...
Human Error and AI Emerge as Key Challenges in Survey of CISOs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley The 2024 Proofpoint “Voice of the CISO” report is a useful barometer for understanding the current cybersecurity landscape, providing valuable...
Prompt Injection Threats Highlight GenAI Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Prompt injection attacks, where individuals input specific instructions to trick chatbots into revealing sensitive information, are a growing risk as...
Responsible AI Licenses (RAIL): Here’s What You Need to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: AJ Starita Responsible AI Licenses (RAIL) are a class of licenses created with the intention of preventing harmful or unethical uses of...
USENIX Security ’23 – PET: Prevent Discovered Errors from Being Triggered in the Linux Kernel – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – PET: Prevent Discovered Errors from Being Triggered...
Security Compliance 101: What It Is and How to Master It – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Kelly Talk to any compliance officer today, and they will all agree that modern security compliance — fulfilling your organization’s regulatory...
CFO Deepfake Redux — Arup Lost $26M via Video – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Construction giant Arup Group revealed as victim of January theft: 10% of net profit lost. A poor peon in the finance...
A journey into forgotten Null Session and MS-RPC interfaces – Source: securelist.com
Source: securelist.com – Author: Haidar Kabibo A journey into forgotten Null Session and MS-RPC interfaces (PDF) It has been almost 24 years since the null session...
Webinar | Level Up Your Security Stack: EDR vs Endpoint Privilege Management – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Chip Gandy Lead Endpoint Engineer, Cox Communications Chip Gandy is the Lead Endpoint Engineer for Cox Communications. He has been in...
Live Webinar | Adversary Analysis of Ransomware Trends – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Ray Umerley Field CISO, Coveware Ray Umerley is the Field CISO for Coveware. With more than 20+ years of experience in...