Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The CISO career path is as exciting as it is fraught with perils. Modern CISOs exist at the intersection...
Day: May 22, 2024
News analysis Q&A: Shake up of the SIEM, UEBA markets continues as LogRhythm-Exabeam merge – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido It’s easy to compile a checklist on why the announced merger of LogRhythm and Exabeam could potentially...
News alert: AI SPERA integrates its ‘Criminal IP’ threat intelligence tool into AWS Marketplace – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Torrance,Calif., May 22, 2024, CyberNewsWire — AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced today that its proprietary...
US Pumps $50M Into Better Healthcare Cyber Resilience – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: Olekcii Mach via Alamy Stock Photo The Advanced Research Projects Agency for Health (ARPA-H) pledged...
GitHub Authentication Bypass Opens Enterprise Server to Attackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Igor Golovnov via Alamy Stock Photo A max-critical security vulnerability in GitHub’s Enterprise Server could...
Trends at the 2024 RSA Startup Competition – Source: www.darkreading.com
Source: www.darkreading.com – Author: Paul Shomo 5 Min Read Source: Aleksia via Alamy Stock Photo COMMENTARY Artificial intelligence (AI) security, automation’s nonhuman identity problem, and the...
Snowflake's Anvilogic Investment Signals Changes in SIEM Market – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Data service provider Snowflake deepened its strategic partnership with cybersecurity-analytics provider Anvilogic this week with a joint offering...
Novel EDR-Killing 'GhostEngine' Malware Is Built for Stealth – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Jack Maguire via Alamy Stock Photo A novel malware that targets vulnerable drivers to terminate and thus...
Preparing Your Organization for Upcoming Cybersecurity Deadlines – Source: www.darkreading.com
Source: www.darkreading.com – Author: Karl Mattson 5 Min Read Source: vska via Alamy Stock Vector COMMENTARY As our world becomes increasingly digitized, malicious actors have more...
Chinese 'ORB' Networks Conceal APTs, Render Static IoCs Irrelevant – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Porntep Lueangon via Alamy Stock Photo Chinese threat actors have been quietly and gradually revolutionizing anti-analysis techniques...
Critical Netflix Genie Bug Opens Big Data Orchestration to RCE – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: batjaket via Shutterstock A critical vulnerability in the open source version of Netflix’ Genie job orchestration engine...
Unredacting Pixelated Text – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Winter • May 22, 2024 7:33 AM I assume that pixelation is chosen to give an impression of...
WitnessAI Launches With Guardrails for AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: krot studio via Shutterstock Despite the interest in AI tools and AI-enhanced technologies, many organizations...
SAGE Cyber Launches CISO Planning Tool – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: ronstik via Alamy Stock Photo SAGE Cyber broke off from parent company HolistiCyber to become...
Proofpoint’s 2024 Voice of the CISO Report Reveals that More than Four in 5 Canadian CISOs Identify Human Error as Leading Cybersecurity Risk – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 To mitigate this area of vulnerability, 86% of CISOs in Canada are turning to AI-powered technology to protect against human error...
Proofpoint’s 2024 Voice of the CISO Report Reveals that Three-Quarters of CISOs Identify Human Error as Leading Cybersecurity Risk – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 To mitigate this area of vulnerability, 87% of CISOs are turning to AI-powered technology to protect against human error and block...
Report Reveals 341% Rise in Advanced Phishing Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security experts have reported a 341% increase in malicious phishing links, business email compromise (BEC), QR code and attachment-based threats in...
UserPro Plugin Vulnerability Allows Account Takeover – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UserPro plugin, a popular community and user profile tool for WordPress developed by DeluxeThemes, has been found to have a...
Fortifying Digital Health Against Cyber Attacks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Nissim Ben-Saadon, Director of Innovation, CYREBRO In today’s digital era, the healthcare industry stands at the forefront of technological...
A Consolidated Approach to Fraud: Bringing Together Risk Insights, Organizations and Technology – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Kimberly Sutherland, vice president, fraud and identity strategy, LexisNexis® Risk Solutions Digital fraud has seen a substantial increase in...
Cybersecurity or Cyber Resilience: Which Matters More? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Planning Beyond an Enterprise Security Posture and Toward Reliable Business Continuity By Amanda Satterwhite, Managing Director of Cyber Growth &...
23-year-old alleged founder of dark web Incognito Market arrested after FBI tracks cryptocurrency payments – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The United States Department of Justice has dealt a blow to dark web drug traffickers by arresting a man alleged...
Arrests made after North Koreans hired for remote tech jobs at US companies – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley US businesses are believed to have recruited thousands of North Korean IT workers, sending earnings (and potentially data) to North...
Criminal IP: Enhancing Security Solutions through AWS Marketplace Integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Torrance, United States / California, May 22nd, 2024, CyberNewsWire AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced today...
Lasso Security Data Protection Tool Aimed at GenAI Applications – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Lasso Security has released a custom policy wizard designed to help companies prevent data and knowledge leaks when they use...
Exploring the Role of ISO/IEC 42001 in Ethical AI Frameworks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ronan Grobler, Compliance Success Manager, Scytale Understanding ISO/IEC 42001 ISO/IEC 42001 provides guidance on building trust in AI systems. It offers a...
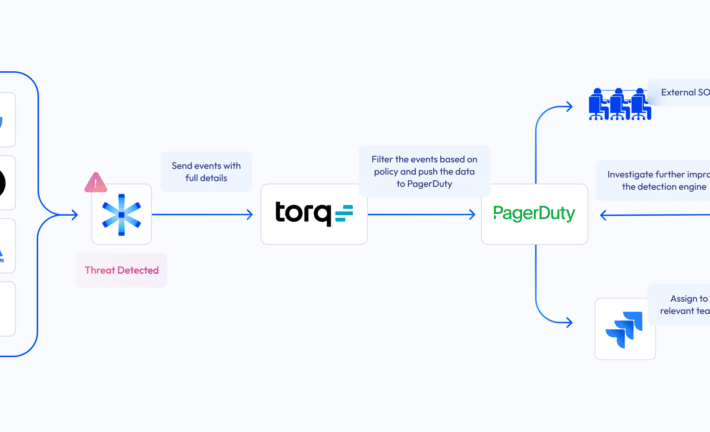
Bridging the NHI security gap: Astrix and Torq partner up – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Guetta While zero-trust policies and identity-centric programs excel at protecting user identities and login credentials with IAM policies and security tools...
Hackers Leverage AI as Application Security Threats Mount – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Threat actors increasingly are targeting monitored applications with active protection as they leverage low-code techniques and AI-powered tools to target...
Securing the Gateway: Why Protecting Build Systems Is Crucial in Modern Software Development – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joe Nicastro Understand why securing build systems is as important as securing production systems. Most organizations want to innovate quickly and efficiently....
FUD: How Fear, Uncertainty, and Doubt can ruin your security program – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden The role of fear Fear drives irrational and panicked decision-making, often leading individuals to prioritize short-term solutions over long-term security...