Source: www.techrepublic.com – Author: Nicole Rennolds We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Day: May 15, 2024
What Is the Dark Web? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: The negative press, coupled with YouTube horror stories, has cemented the Dark Web’s reputation for illicit behavior. Today, the Dark Web is...
Quick Glossary: DevSecOps – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: The way software is developed has changed. DevSecOps is transforming the industry by incorporating security from the early stages and automating traditional...
5 key takeaways for CISOs, RSA Conference 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Last week, over 40,000 business and cyber security leaders converged at the Moscone Center in San Francisco to attend...
Why Is Hardware More Secure than Software? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The underlying differences between hardware and software when implementing critical cryptosystems. By Kimmo Järvinen, Co-founder and CTO, Xiphera The majority...
The Fusion of Fraud and IAM: An Event with Transmit Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Editor Next week our founder Simon Moffatt will be speaking at an event in London with leading customer identity and access management...
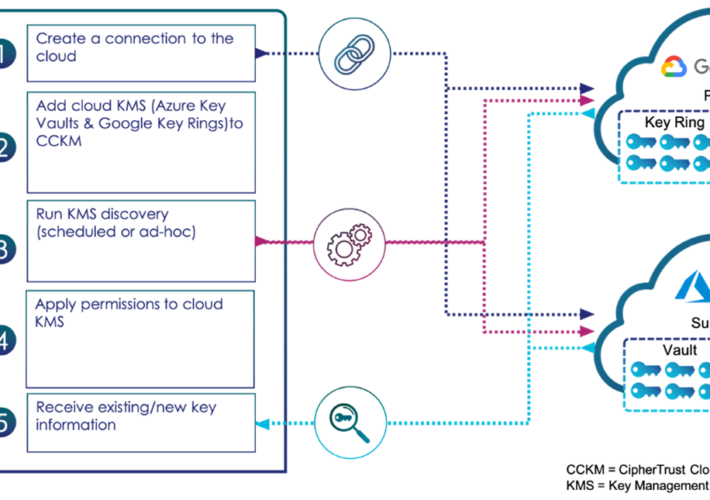
Systematically Bring to Light the Keys in Your Clouds – Source: securityboulevard.com
Source: securityboulevard.com – Author: madhav Systematically Bring to Light the Keys in Your Clouds madhav Wed, 05/15/2024 – 10:23 The cloud has enabled organizations to create...
Thunderbird Vulnerabilities Fixed in Ubuntu and Debian – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina In recent Ubuntu and Debian security updates, several vulnerabilities have been addressed in Thunderbird, the popular open-source mail and newsgroup...
5 Must-Haves to Get (and Stay) Compliant With Privacy and Security Frameworks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Adar Givoni, Director of Compliance, Scytale Achieving and maintaining compliance with data privacy and security frameworks is a complex undertaking that requires...
How an Intrusion Detection System Can Ensure End-User Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: TuxCare Team It’s never been more important for businesses to invest in the best security measures available to them. Hackers and cybercriminals...
CISA Alert: GitLab Password Exploit – Act Now For Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja In the realm of cybersecurity, vigilance is paramount. Recently, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) flagged a critical...
The Rise of AI and Blended Attacks: Key Takeaways from RSAC 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kellie Roessler The 2024 RSA Conference can be summed up in two letters: AI. AI was everywhere. It was the main topic...
A Guide to Cybersecurity Compliance in the Oil and Gas Industry – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sectrio When talking about industries, few are as critical to global infrastructure and economic stability as the oil and gas sector. In...
Unlock Your Cybersecurity Career: Exclusive Discounts on Top Training Courses! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist There are tremendous opportunities in cybersecurity and the industry needs many more qualified workers. Training plays an important part. That...
The Most Powerful Women Of The Channel 2024: Power 100 – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 The Power 100 is culled from the ranks of CRN’s Women of the Channel and spotlights the female executives at vendors...
10 Hot AI Cybersecurity Tools At RSAC 2024 – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Vendors including Palo Alto Networks, Trellix and Proofpoint debuted new AI-powered security tools and capabilities this week during the conference. Without...
Sumit Dhawan, CEO, Proofpoint on NightDragon: Live From RSA Conference – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 10,851 followers 1w Edited To wrap up this edition of NightVision, live from the RSA Conference in San Francisco, NightDragon CEO...
Singapore Cybersecurity Update Puts Cloud Providers on Notice – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: VideoFlow via Shutterstock Lawmakers in Singapore updated the nation’s cybersecurity regulations on May 7, giving more power...
Top 5 Most Dangerous Cyber Threats in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer Source: Stuart Miles via Alamy Stock Photo RSA CONFERENCE 2024 – San Francisco – Only five months into...
Microsoft Windows DWM Zero-Day Poised for Mass Exploit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Wim Wiskerke via Alamy Stock Photo A trio of zero-days headline Microsoft’s May Patch...
Unprotected Session Tokens Can Undermine FIDO2 Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: FrankHH via Shutterstock Many organizations that have implemented passwordless authentication via the FIDO2 standard may be undermining...
As the FBI Closes In, Scattered Spider Attacks Finance, Insurance Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Design Pics Inc via Alamy Stock Photo Scattered Spider hackers have been tearing through the finance and...
A Cost-Effective Encryption Strategy Starts With Key Management – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: NicoElNino via Shutterstock Companies have a problem with encryption: While many businesses duly encrypt sensitive data, there...
Dangerous Google Chrome Zero-Day Allows Sandbox Escape – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Kristoffer Tripplaar via Alamy Stock Photo Google has released an emergency security update for...
Current Market Forces Disincentivizing Cybersecurity, Says NCSC CTO – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The technology market needs to be better incentivized to build cyber secure products, argues the CTO of the National Cyber Security...
A Third of CISOs Have Been Dismissed “Out of Hand” By the Board – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Global CISOs are routinely belittled and dismissed as being overly negative by their board, according to new Trend Micro research highlighting...
Microsoft Fixes Three Zero-Days in May Patch Tuesday – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 System administrators have over 60 CVEs to address in the latest Microsoft Patch Tuesday, including three zero-day vulnerabilities. Of these three...
Microsoft Patches Zero-Day Exploited by QakBot – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Kaspersky Says It Spotted QakBot Operators Exploiting the Flaw in...
Impact of Ascension’s Cyberattack IT Outage Varies by Region – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Incident & Breach Response In Some Regions, ER Patients Still Diverted, Pharmacies Can’t Fill...
Live Webinar | What’s Missing in Your Identity First Security Strategy?: Lessons from an ISMG Survey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...