Source: krebsonsecurity.com – Author: BrianKrebs The United States joined the United Kingdom and Australia today in sanctioning 31-year-old Russian national Dmitry Yuryevich Khoroshev as the alleged...
Day: May 7, 2024
Does CISA’s KEV Catalog Speed Up Remediation? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Federico Caputo via Alamy Stock Photo RSA CONFERENCE 2023 – San Francisco – When the...
What’s the Future Path for CISOs? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Kjetil Kolbjørnsrud via Alamy Stock Photo Security professionals who rise through the corporate ranks and become chief...
City of Wichita Public Services Disrupted After Ransomware Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Freedomz via Shutterstock The City of Wichita is investigating a ransomware attack that happened over the weekend...
Feds: Reducing AI Risks Requires Visibility & Better Planning – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Deemerwha studio via Shutterstock When the US Department of Energy (DoE) analyzed the use of artificial intelligence...
Spies Among Us: Insider Threats in Open Source Environments – Source: www.darkreading.com
Source: www.darkreading.com – Author: Chris Lindsey Chris Lindsey, Application Security Evangelist, Mend.io May 7, 2024 3 Min Read Source: Brian Jackson via Alamy Stock Photo COMMENTARY...
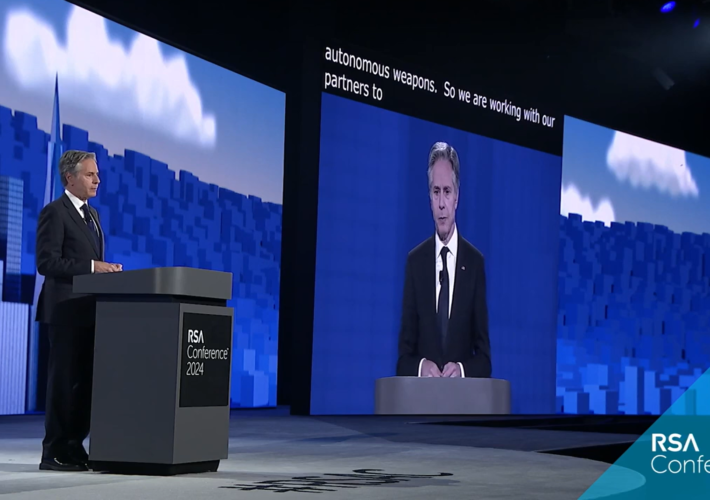
Blinken: Digital Solidarity Is ‘North Star’ for US Policy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Karen Spiegelman, Features Editor US Secretary of State Antony J. Blinken announced a new federal initiative to set up guardrails for digital...
Anetac Targets Service Account Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: Nico El Nino via Adobe Stock Photo Nearly every organization struggles to monitor service accounts,...
Exploits and vulnerabilities in Q1 2024 – Source: securelist.com
Source: securelist.com – Author: Alexander Kolesnikov, Vitaly Morgunov We at Kaspersky continuously monitor the evolving cyberthreat landscape to ensure we respond promptly to emerging threats, equipping...
Eclypsium Supply Chain Security Platform Protects GenAI Infrastructure with Addition of Hardware and Training Model Assessment Capabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Eclypsium is extending its digital supply chain security to cover GenAI hardware and training models SAN FRANCISCO – RSA Conference...
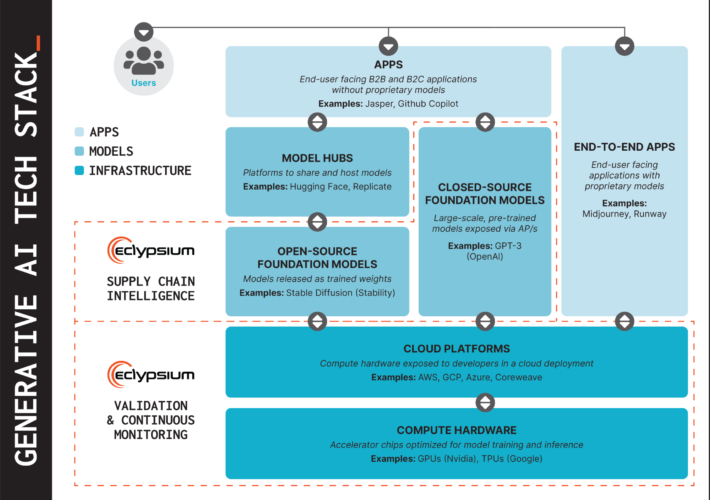
Securing Supply Chains for GenAI Hardware and Models – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Today, at RSA Conference 2024, we’re announcing new capabilities to help secure the fundamental layers of the GenAI tech stack....
Enabling GenAI with AI-infused API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Callahan GenAI has the promise to transform companies, and introduce a lot of security risk. One of the main benefits of...
API Vulnerabilities Found Across AI Infrastructure Projects at NVIDIA, Mercedes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Organizations are rushing to integrate AI-driven features into their operations. However, the reliance on application programming interfaces (APIs) poses significant...
Datacenter Proxies: Unveiling the Workhorse of the Proxy World – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra Reading Time: 4 min Proxies have become a cornerstone of online privacy and multifunctionality. Datacenter proxies, in particular, have established...
White House Cybersecurity Workforce Initiative Backed by Tech Titans – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy With more than half a million cybersecurity positions currently open across the country, there is a pressing need to encourage...
Tracking Illegal Pharmaceutical Sales on Social Media – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nisos Nisos Tracking Illegal Pharmaceutical Sales on Social Media Nisos continuously monitors mainstream and alternative social media platforms as well as other...
What are Cyber Essentials? Requirements, Preparation Process & Certification – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ronan Grobler, Compliance Success Manager, Scytale Let’s be honest: anything with the word ‘essentials’ in it is bound to grab our attention....
Can VPNs Be Tracked by the Police? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
RSA: Google Enhances its Enterprise SecOps Offerings With Gemini AI – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The RSA Conference, held in San Francisco from May 6-9, brings together cybersecurity professionals from across the world. This year’s...
Google Steps Up The Battle Against Gmail Spam – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Andy Wolber Starting in early 2024, Google tightened three enforcement efforts in the organization’s on-going fight against spam. First, bulk senders of...
10 Myths about Cybersecurity You Shouldn’t Believe – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: The first step to increasing your business’ cybersecurity is to educate yourself about any misconceptions so you understand the very real consequences...
ISMG Editors: Opening Day Overview of RSA Conference 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Fraud Management & Cybercrime Ransomware, AI Technology and the Art of the Possible...
Enterprise Technology Management: No Asset Management Silos – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 An enterprise has many different types of technology in its estate – including software, hardware and infrastructure – and historically each...
The Challenges in Keeping Medical Device Software Updated – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Updating software as new vulnerabilities are discovered persistently remains a top cybersecurity challenge involving medical devices, said David Brumley, a cybersecurity...
Microsoft Overhauls Security Practices After Major Breaches – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , IT Risk Management Company Plans to Link Executive Compensation to Achieving Security Milestones Chris Riotta (@chrisriotta)...
LevelBlue Leverages AI for Threat Intel Following AT&T Split – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development AI Investments and Global Expansion Set to Propel Growth After...
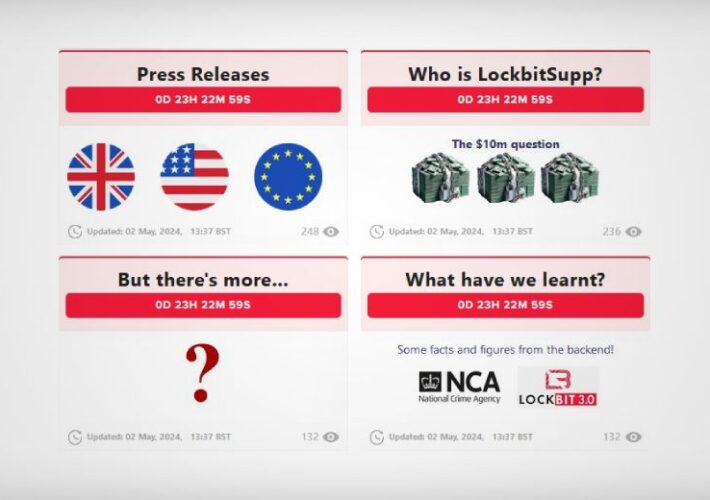
Operation Cronos Again Threatens to Reveal LockBitSupp – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware International Police Operation Revives Seized LockBit Dark Web Leak Site Prajeet Nair (@prajeetspeaks) • May...
Key strategies for building cyber resilience in 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Deryck Mitchelson, Field CISO EMEA, Check Point. This article was originally published via the World Economic Forum and reprinted with...
UK armed forces’ personal data hacked in MoD breach – Source: www.theguardian.com
Source: www.theguardian.com – Author: Tom Ambrose and agency The Ministry of Defence has suffered a significant data breach and the personal information of UK military personnel...
New Lawsuit Attempting to Make Adversarial Interoperability Legal – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Winter • May 6, 2024 8:30 AM The whole lawsuit hinges around this text in the law (c)(2)(B):...