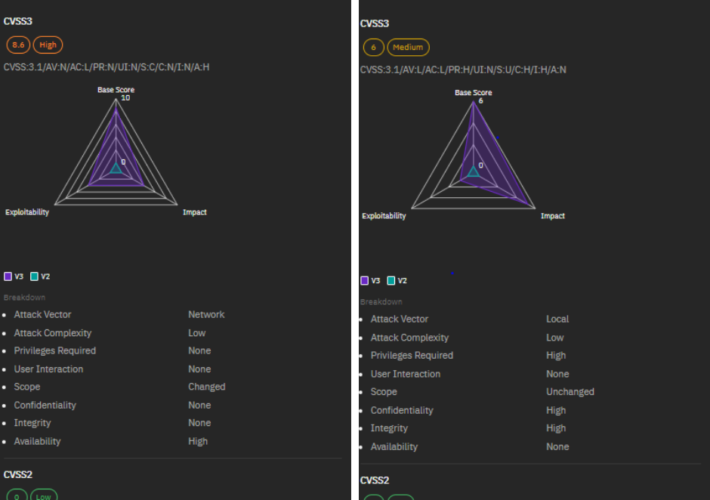
Source: www.infosecurity-magazine.com – Author: 1 North Korean threat actors are exploiting weak email policies to spoof legitimate domains during espionage phishing campaigns, a new US government...
Day: May 3, 2024
Indonesia is a Spyware Haven, Amnesty International Finds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Indonesia has become a hub for spyware and surveillance tools that threaten citizens’ rights and privacy, Amnesty International has found. Building...
U.K., U.S. and Canadian Cyber Authorities Warn of Pro-Russia Hacktivist Attacks on Operational Technology Systems – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson The U.K.’s National Cyber Security Centre (NCSC) and other international cyber authorities, including the Federal Bureau of Investigation (FBI), have...
How Are APAC Tech Salaries Faring in 2024? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Working for a salary in tech has been somewhat of a wild ride in APAC in recent years. First, there...
My TED Talks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Rare Interviews with Enigma Cryptanalyst Marian Rejewski – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • May 3, 2024 8:00 AM @ ALL, Like many cryptographers that come eventually to public...
Streamline NIS2 Compliance with Automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Blackwell It’s no secret that NIS2 is around the corner, and that this directive is full of stringent rules, regulations and...
A Closer Look at Top 5 Vulnerabilities of April 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shubham Jha Keeping pace with the latest cybersecurity threats is vital for organizations of all sizes. Here at Strobes, our security team...
Insider Risk Digest: April – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lucas Seewald Dive into our latest Insider Risk Digest, where we unravel recent cases of espionage, insider betrayal, and security breaches across...
CVE-2024-27322 Should Never Have Been Assigned And R Data Files Are Still Super Risky Even In R 4.4.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr I had not planned to blog this (this is an incredibly time-crunched week for me) but CERT/CC and CISA made a...
The Persistent Threat of Path Traversal Vulnerabilities in Software Development – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nik Hewitt Path traversal vulnerabilities, or directory traversal, are now subject to a government advisory for obligatory consideration We live in an...
What is Proxmox VE – and Why You Should Live Patch It – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina Proxmox VE, like any software, is vulnerable to security threats. Patching helps address these vulnerabilities, protecting your virtual machines from...
GUEST ESSAY: A primer on how, why ‘dynamic baselining’ fosters accurate DDoS protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Ahmed Abdelhalim Businesses today need protection from increasingly frequent and sophisticated DDoS attacks. Service providers, data center operators, and enterprises...
FIN7 Cybercrime Group Strikes US Auto Sector Using Carbanak – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja Recent reports have highlighted that the notorious FIN7 cybercrime group has targeted the U.S. automotive industry through a sophisticated spear-phishing...
RSAC 2024 Innovation Sandbox | Aembit: An IAM Platform for Cloud Workloads – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has...
Proofpoint Announces Availability of its Human-Centric Security Solutions in AWS Marketplace – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 AWS customers worldwide can now deploy Proofpoint’s full stack of people and information protection that defend organizations’ human layer SUNNYVALE, Calif.,...
Billions of Android Devices Open to ‘Dirty Stream’ Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: rafapress via Shutterstock Researchers from Microsoft recently discovered many Android applications — including at least four with...
DPRK’s Kimsuky APT Abuses Weak DMARC Policies, Feds Warn – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Panther Media GmbH via Alamy Stock Photo North Korean hackers are taking advantage of weak DMARC configurations...
Software Security: Too Little Vendor Accountability, Experts Say – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Nick Lylak via Alamy Stock Photo While legal legwork is already in progress to hold...
Hacker Sentenced After Years of Extorting Psychotherapy Patients – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Taina Sohlman via Alamy Stock Photo Aleksanteri Kivimäki, a Finnish national, has been sentenced to...
Dropbox Breach Exposes Customer Credentials, Authentication Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Lina Images via Shutterstock Online storage service Dropbox is warning customers of a data breach by a...
Name That Edge Toon: Puppet Master – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist 1 Min Read Ever feel like you need a little distance from the Internet? Come up with a clever cybersecurity-related...
Intel Harnesses Hackathons to Tackle Hardware Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: kawin ounprasertsuk via Alamy Stock Photo Ever since the first Hack@DAC hacking competition in 2017, thousands of...
Held Back: What Exclusion Looks Like in Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild, Contributing Writer Source: Jose Luis Stephens via Alamy Most of us do not want to be excluded at work –...
Palo Alto Updates Remediation for Max-Critical Firewall Bug – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 2 Min Read Source: SOPA Images Limited via Alamy Stock Photo Palo Alto Networks (PAN) is sharing updated remediation...
CISO Corner: Evil SBOMs; Zero-Trust Pioneer Slams Cloud Security; MITRE’s Ivanti Issue – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Welcome to CISO Corner, Dark Reading’s weekly digest of articles tailored specifically to security operations...
Critical Flaw in R Language Poses Supply Chain Risk – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Deserialization Vulnerability Allows for Remote Code Execution Akshaya Asokan (asokan_akshaya) • May 2, 2024...
Correlating Cyber Investments With Business Outcomes – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The new rules adopted by the Securities and Exchange Commission require organizations to report cyber incidents that have a material effect...
Rehab Hospital Chain Hack Affects 101,000; Facing 6 Lawsuits – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime At Least 33 Ernest Health Facilities in 12 States Are Reporting Breaches...
Breach Roundup: REvil Hacker Gets Nearly 14-Year Sentence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: Another Ivanti Zero-Day? And FBI Calls for Strengthening DMARC...