Source: securelist.com – Author: GReAT On March 29, 2024, a single message on the Openwall OSS-security mailing list marked an important discovery for the information security,...
Month: April 2024
CISA: Russian Hackers Stole Emails Between U.S. Agencies and Microsoft – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Russian state-sponsored hackers who broke into Microsoft’s corporate email accounts during the monthslong hack stole email messages between the enterprise...
NIPS Troubleshooting Steps for No Log – Source: securityboulevard.com
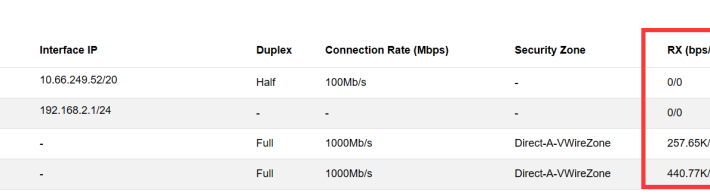
Source: securityboulevard.com – Author: NSFOCUS NIPS aims to accurately monitor abnormal network traffic, automatically blocking various types of aggressive traffic in real-time, particularly application layer threats....
Sisense Data Breach Notice for Hyperproof Customers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hyperproof Team At Hyperproof, safeguarding our customers’ data is our utmost priority. We understand the importance of trust and transparency, especially in...
Introducing the Aembit Kerberos Trust Provider – Source: securityboulevard.com
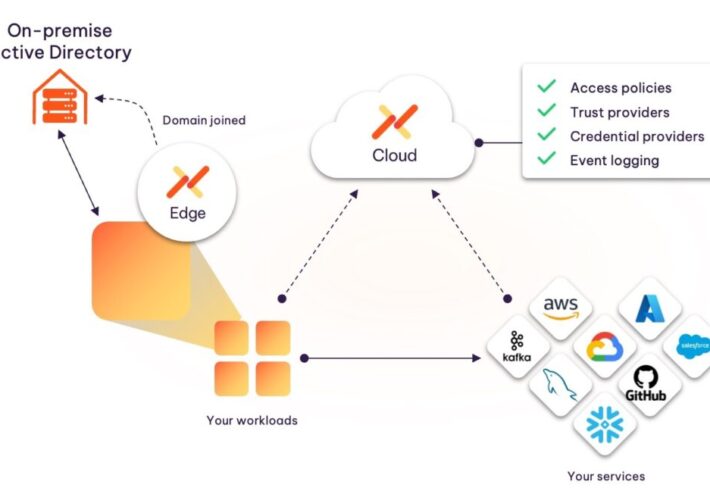
Source: securityboulevard.com – Author: Ashur Kanoon Today’s development environments have evolved greatly, with a high dependence on cloud-deployed SaaS tools. However, most organizations are still running...
Google Extends Generative AI Reach Deeper into Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Google this week extended its effort to apply generative artificial intelligence (AI) to cybersecurity by adding an ability to summarize...
Simbian Unveils Generative AI Platform to Automate Cybersecurity Tasks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Simbian today launched a cybersecurity platform that leverages generative artificial intelligence (AI) to automate tasks that can increase in complexity...
Are you prepared for Google’s 90-day validity period on TLS certificates? – Source: securityboulevard.com
Source: securityboulevard.com – Author: AnneMarie Avalon Google’s proposal for a 90-day validity period on TLS certificates is a game-changer for digital certificate management. It’s not just...
How to Create a Cybersecurity Incident Response Plan – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Kelly Editor’s note: With the increased prevalence of ransomware and other cyberattacks, now is the time to take a moment to...
How to find AMI MegaRAC BMCs running lighttpd with runZero – Source: securityboulevard.com
Source: securityboulevard.com – Author: Blain Smith Latest lighttpd vulnerability Binarly Research discovered that AMI MegaRAC Baseboard Management Controllers (BMC) on servers running lighttpd before version 1.4.51...
Our Security of AI Papers and Blogs Explained – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin Moderately relevant AI made image about AI papers 🙂 steampunk ofc! Recently our team has written several papers and blogs focused...
FBI Calls for Increased Funding to Counter Cyber Threats – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybersecurity Spending , Government , Industry Specific FBI Director Chris Wray Warns U.S. Falling Behind to Adversaries in Cyberspace Chris Riotta...
Identity Security and How to Reduce Risk During M&A – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Banks, insurance, and other financial services institutions are experiencing a growing number of mergers and acquisitions. This activity comes with an...
Raspberry Robin Morphs, Now Spreads via Windows Script Files – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Malware Platform Operators Taket Steps to Obfuscate Code Prajeet Nair (@prajeetspeaks) • April 11, 2024...
Live Webinar | What’s Missing in Your Identity First Security Strategy: Lessons from an ISMG Survey – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Wade Ellery Field Chief Technology Officer, Radiant Logic Wade Ellery, Field Chief Technology Officer and Senior Technical Evangelist with Radiant Logic....
Webinar | Augmenting Email DLP with AI at the Human Layer – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Andrew Goodman Senior Manager of Product Marketing, Proofpoint Andrew Goodman is a Senior Manager of Product Marketing at Proofpoint, specializing in...
Change Healthcare Attack ‘Devastating’ to Doc Practices – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific AMA Survey Finds 80% of Practices Lost Revenue From Unpaid Claims Marianne...
Zscaler Buys Airgap Networks to Fuel Segmentation in IoT, OT – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Internet of Things Security Deal Will Thwart Lateral Movement of Malicious Traffic Inside...
Sisense Password Breach Triggers ‘Ominous’ CISA Warning – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: GK Images via Alamy Stock Photo While details are still emerging, the US federal government...
Knostic Raises $3.3M for Enterprise GenAI Access Control – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE RESTON, Va. and TEL AVIV, Israel, April 11, 2024/PRNewswire-PRWeb/ — Knostic, the world’s first provider of need-to-know access controls for...
Cohesity Extends Collaboration to Strengthen Cyber Resilience With IBM Investment in Cohesity – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN JOSE, Calif. – April 11, 2024 – Cohesity today announced a deepening of its cyber resilience collaboration with IBM. The...
Critical Rust Flaw Poses Exploit Threat in Specific Windows Use Cases – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Monticello via Shutterstock The Rust Project has issued an update for its standard library, after a vulnerability...
DPRK Exploits 2 MITRE Sub-Techniques: Phantom DLL Hijacking, TCC Abuse – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Stuart Miles via Alamy Stock Photo This month, MITRE will be adding two sub-techniques to its ATT&CK...
Expired Redis Service Abused to Use Metasploit Meterpreter Maliciously – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Age Foto Stock via Alamy Stock Photo Attackers are using an 8-year-old version of the Redis open-source...
Apple Warns Users in 150 Countries of Mercenary Spyware Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: nk Drop via Shutterstock Apple this week updated its spyware threat notification system to alert...
Why MLBOMs Are Useful for Securing the AI/ML Supply Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Diana Kelley 3 Min Read Source: Cagkan Sayin via Alamy Stock Photo COMMENTARY The days of large, monolithic apps are withering. Today’s...
Zambia Busts 77 People in China-Backed Cybercrime Operation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: JJ Gouin via Alamy Stock Photo Law enforcement in Zambia this week raided a Chinese...
Leveraging the power of AI and cloud computing – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: As cyber adversaries diversify their tactics and devise increasingly sophisticated attack methods, legacy cyber security tools may not be...
News alert: NTT all photonics network connects data centers in U.S., U.K. at very low latency – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Francisco and Tokyo, Apr. 11, 2024 – At Upgrade 2024, NTT Corporation (NTT) and NTT DATA announced the successful demonstration...
News alert: Simbian launches with $10M to build autonomous, GenAI-powered security platform – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Mountain View, Calif. – April 11, 2024 – Simbian today emerged from stealth mode with oversubscribed $10M seed funding to deliver on fully autonomous security. As a...