Source: securityboulevard.com – Author: Ahona Rudra Reading Time: 6 min There is an old saying- prevention is better than cure. This is exactly the aim of...
Day: April 11, 2024
NIST CSF: A “Fellowship” for Your Cybersecurity Journey to 2.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: CISO Global April 10, 2024 By Samuel Lewis, Senior Security Consultant The National Institute of Standards and Technology (NIST) released version 2.0...
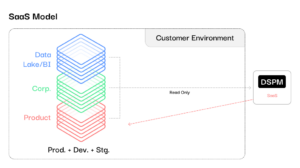
The Irrefutable Case for Customer-Native (In-Your-Cloud) DSPM – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy There is no denying that businesses are under increasing pressure to fortify their defenses and better protect sensitive information. Ransomware payments...
OWASP Top 10 for LLM Applications: A Quick Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: AJ Starita Published in 2023, the OWASP Top 10 for LLM Applications is a monumental effort made possible by a large number...
Why a Cybersecurity Platform Beats Standalone Applications – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith As cyber threats continue to grow in volume and sophistication, businesses are determined to keep their networks and data safe...
USENIX Security ’23 – Discovering Adversarial Driving Maneuvers against Autonomous Vehicles – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: *Ruoyu Song, Muslum Ozgur Ozmen, Hyungsub Kim, Raymond Muller, Z. Berkay Celik, Antonio Bianchi *** This is a Security...
Raspberry Robin Malware Now Using Windows Script Files to Spread – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Raspberry Robin, the highly adaptable and evasive worm and malware loader that first appeared on the cyberthreat scene in 2021,...
Automata An Expert Researcher Never Sleeps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Imagine you had 1,000 expert security researchers working continuously to analyze all the new binaries in your environment to find...
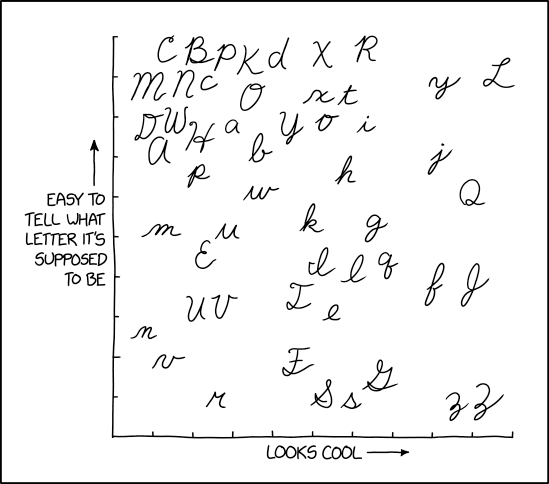
Randall Munroe’s XKCD ‘Cursive Letters’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Microsoft’s April 2024 Patch Tuesday: Updates for 150 Vulnerabilities and Two Zero-Days – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire In a significant security update, Microsoft has released its April 2024 Patch Tuesday updates, which address a hefty 150 vulnerabilities...
Half of UK Firms, Charities Failed to Report Cyber Incidents – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Security Operations , Standards, Regulations & Compliance Survey: SMBs, Charities Mostly Targeted With Phishing, Online Impersonation in 2023...
Cloud Computing – Gain Network-Level Control From Anywhere – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Government , Industry Specific Why Moving to the Cloud Is a Strategic Gain for Federal Agencies Mike Korgan,...
Wiz Buys Startup Gem Security for $350M to Spot Cloud Issues – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Buying CDR Startup Gem Will Help Wiz Address Needs of SecOps, Incident Responders Michael Novinson (MichaelNovinson)...
US CISA Aims to Expand Automated Malware Analysis Support – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Government , Industry Specific , Security Operations US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform Chris Riotta (@chrisriotta) • April...
Cybercrime Group Uses Likely AI Script to Load Info Stealer – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Cybercrime , Fraud Management & Cybercrime Proofpoint Spots Novel Threat Against German Organizations Prajeet Nair...
Guide to Enterprise Risk Management
FREQUENTLY ASKED QUESTIONS In today’s challenging global economy, business opportunities and risks are constantly changing. There is a need for identifying, assessing, managing and monitoring the...
In Memoriam: Ross Anderson, 1956-2024 – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • April 10, 2024 1:12 PM @ Bruce, “he “spent some of his youth busking on...
Guide to Cyber Security Measures
Step by step to a digitally secure organisation The document outlines essential measures for cyber security, emphasizing the importance of regular risk management alongside these measures....
Malware Analysis Guide
The document discusses the significance of interactive malware analysis using ANY.RUN, a platform that offers a unique approach to analyzing malware samples. It emphasizes the importance...
PAUTAS – FUNCIONES – CRIPTOGRÁFICO
Almacenamiento de contraseñas The document provides guidelines on cryptographic functions, emphasizing the importance of considering current threats and the need for specific adaptations due to varying...
GLOBAL THREAT REPORT
The CrowdStrike 2024 Global Threat Report highlights a significant increase in interactive intrusions in 2023, particularly targeting technology sectors. These intrusions saw a 60% rise, indicating...
Global Cybersecurity Trends
The January 2024 Cybersecurity Analysis provides a comprehensive view of the evolving threat landscape. The Threat Analytics section outlines a significant global surge in breaches, with...
Gestión de riesgos
The Risk Management Guide provides a comprehensive approach for entrepreneurs to handle risks effectively. It emphasizes the importance of qualitative and quantitative risk estimation methods, recommending...
Key strategies for building cyber resilience in 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Deryck Mitchelson, EMEA Field Chief Information Security Officer, Check Point Software Technologies. Cyber resilience is more than just a buzzword...