Source: www.proofpoint.com – Author: 1 Source: Yuri Arcurs via Alamy Stock Photo At first, analysts thought the downloader was a variant of well-known malware IcedID —...
Day: April 6, 2024
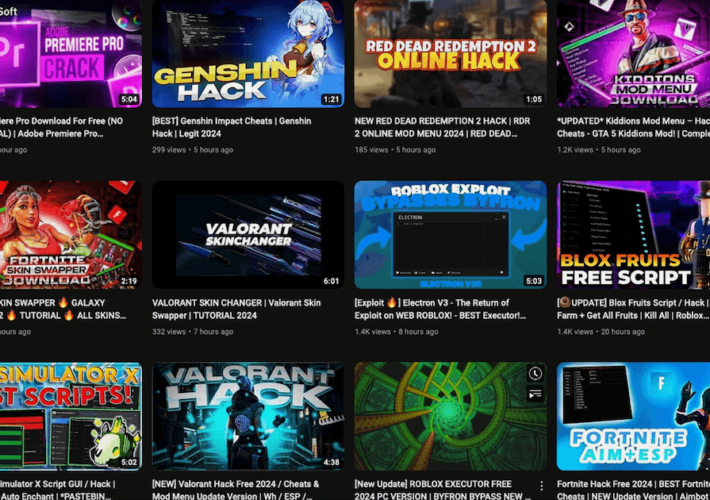
YouTube channels found using pirated video games as bait for malware campaign – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Hackers are distributing malware through multiple YouTube channels that promote cracked or pirated video games, according to researchers at Proofpoint. In...
“Hope Is Not a Strategy”: Cyber Leaders on the Real Keys to Executing a Defense-in-Depth Strategy – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Jesse Fasolo, Director, Technology Infrastructure & Cyber Security, St. Joseph’s Health When it comes to cybersecurity — and by extension, patient...
Friday Squid Blogging: SqUID Bots – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments William • April 5, 2024 5:21 PM Could you imagine discovering that your identity had been used to...
Thread Hijacking: Phishes That Prey on Your Curiosity – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Thread hijacking attacks. They happen when someone you know has their email account compromised, and you are suddenly dropped into an...
Recent Windows updates break Microsoft Connected Cache delivery – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says Windows 10 updates released since the start of the year are breaking Microsoft Connected Cache (MCC) node discovery...
The Week in Ransomware – April 5th 2024 – Virtual Machines under Attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Ransomware attacks targeting VMware ESXi and other virtual machine platforms are wreaking havoc among the enterprise, causing widespread disruption and...
Salt Security Applies Generative AI to API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Salt Security this week revealed it has embedded a generative artificial intelligence (AI) assistant, dubbed Pepper, into its application programming...
Small business cyber security guide: What you should prioritize & where you should spend your budget – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden Think of it this way: The more your team is knowledgeable about cyber attacks, the more likely they will be...
Ghostwriter v4.1: The Custom Fields Update – Source: securityboulevard.com
Source: securityboulevard.com – Author: Christopher Maddalena Let’s dive into what makes this so exciting! There’s so much to cover that we won’t be offended if you...
FCC: Phone Network Bugs Must Be Fixed — But are SS7/Diameter Beyond Repair? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings The Federal Communications Commission is finally minded to address decades-old vulnerabilities. Dusty, moldy, prehistoric protocols from the 1980s and ’90s still...
Ivanti CEO Promises Stronger Security After a Year of Flaws – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The chief executive of vulnerability-plagued Ivanti said the management software maker is revamping its security practices after months of reports...
Automating and maintaining SBOMs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mahesh Raj Mohan Hot Topics FCC: Phone Network Bugs Must Be Fixed — But are SS7/Diameter Beyond Repair? Ivanti CEO Promises Stronger...
xz backdoor Part 2: On the Importance of Runtime Security in the Age of OSS Backdoors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Larkin It’s been a week since the xz backdoor dropped. I stand by my earlier conclusion that the community really dodged...
CISA Unveils Critical Infrastructure Reporting Rule – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy The Cybersecurity and Infrastructure Security Agency (CISA) issued a Notice of Proposed Rulemaking (NPRM) for the Cyber Incident Reporting for...
Update for KernelCare Live Patches for CVE-2024-1086 in AlmaLinux 8 & 9 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joao Correia The KernelCare team is working on deploying a live patch for CVE-2024-1086 for AlmaLinux 8 and AlmaLinux 9 users. As...
What is Certificate Provisioning? – Source: securityboulevard.com
Source: securityboulevard.com – Author: AnneMarie Avalon Certificate provisioning refers to the process of obtaining, deploying, and managing digital certificates within an organization’s IT infrastructure. These certificates,...
Vietnamese Threat Actor Targeting Financial Data Across Asia – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime CoralRaider Looks for Social Media Accounts That Contain Payment Information Mihir Bagwe (MihirBagwe) • April...
Medical Device Cyberthreat Modeling: Top Considerations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific Threat Modeling Expert Adam Shostack on Critical Mistakes to Avoid Marianne Kolbasuk...
Cloudflare Enters Observability Space With Baselime Purchase – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Next-Generation Technologies & Secure Development , Observability Acquiring Baselime Will Give Developers Better Visibility Into Serverless Platforms Michael Novinson (MichaelNovinson) •...
Hackers Can Use AI Hallucinations to Spread Malware – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development A Fake Software Library Made Up by a ChatBot Was...
Sophisticated Latrodectus Malware Linked to 2017 Strain – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management New Malware With Ties to IcedID Loader Evades Detection, Gains...
Government Communications: The Threats – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Nicole Allen, Marketing Manager at Salt Communications In an age where information flows freely and rapidly, government communications have...
Tory MP Luke Evans reveals he was targeted in Westminster sexting scandal – Source: www.theguardian.com
Source: www.theguardian.com – Author: Eleni Courea and Charlie Moloney A Conservative MP has revealed that he was targeted in the Westminster sexting scandal and was the...
An MP who gives colleagues’ numbers to blackmailers. Isn’t William Wragg just right for this Westminster? | Marina Hyde – Source: www.theguardian.com
Source: www.theguardian.com – Author: Marina Hyde Where to start with Westminster’s latest scandal, which – without wishing to speculate on spoilers – I suggest you formally...
Critical Bugs Put Hugging Face AI Platform in a ‘Pickle’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Barry Mason via Alamy Stock Photo Two critical security vulnerabilities in the Hugging Face AI platform opened...
Panera Bread Fuels Ransomware Suspicions With Silence – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading 1 Min Read Source: Judith Collins via Alamy Stock Photo Panera Bread customers and employees reported...
CISO Corner: Ivanti’s Mea Culpa; World Cup Hack; CISOs & Cyber Awareness – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Welcome to CISO Corner, Dark Reading’s weekly digest of articles tailored specifically to security operations...
Magecart Attackers Pioneer Persistent E-Commerce Backdoor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Tawan Chaisom via Alamy Stock Photo Magecart attackers have a new trick: Stashing persistent backdoors...
How Do We Integrate LLMs Security Into Application Development? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Edge Editors Large language models require rethinking how to bake security into the software development process earlier. 4 Min Read Source: Chroma...